XK0-004 Online Practice Questions and Answers
Which of the following is the purpose of the vmlinux file on a Linux system?
A. To prevent a Linux kernel panic
B. To start a Linux virtual machine
C. To provide the executable kernel for the system
D. To enable resource access to the network
A systems administrator must clean up all application files in the directory /var/log/app. However, the company's security policy requires the files to be kept on the backup server for one year. The Linux server has only the tar and bzip2 packages installed.
Which of the following commands will package and compress the files?
A. tar -zcvf applicationfiles.tar.bz2 /var/log/app/*
B. tar -jcvf applicationfiles.tar.bz2 /var/log/app/*
C. tar -cvf applicationfiles.tar.bz2 /var/log/app/*
D. tar -xvf applicationfiles.tar.bz2 /var/log/app/*
A security administrator must use a password and a token to log in to the server. Which of the following processes does this describe?
A. Kerberos authentication
B. RADIUS authentication
C. Biometric authentication
D. Multifactor authentication
E. LDAP authentication
Which of the following default files are typically used to contain a list of public keys from other computers? (Choose two.)
A. ~/.ssh/authorized_keys
B. ~/.ssh/config
C. ~/.ssh/id_dsa.pub
D. ~/.ssh/known_hosts
E. ~/.ssh/id_rsa
F. ~/.ssh/id_rsa.pub
A systems administrator is investigating low performance a server. After executing some diagnostic commands, the administrator analyzes the data: Which of the following is the cause of low performance on the server?
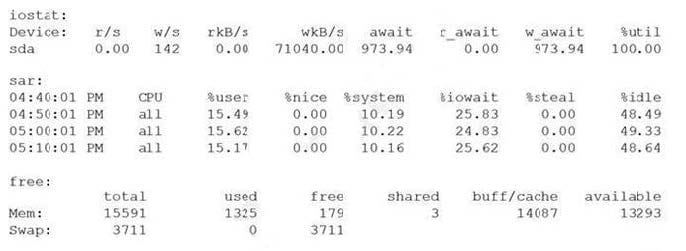
A. Lack of swap space
B. Lack of available memory
C. User processes have taken up all the available CPU time
D. High disk activity
A Linux administrator wants to configure log messages of critical or higher severity levels from the cron utility to be logged to the console. Which of the following will accomplish this objective?
A. Edit the /etc/logrotate.d/cron file to include the line cron.emerg.* /dev/console
B. Edit the /etc/rsyslog.conf file to include the line cron.emerg.* /dev/console
C. Edit the /etc/logrotate.conf file to include the line cron.emerg.* /dev/console
D. Edit the /etc/rsyslog.d/conf file to include the line cron.emerg.* /dev/console
A junior Linux administrator needs to create 16 empty files quickly that will contain sales information for each quarter for the past four years. Which of the following commands will meet this requirement?
A. touch {2015,2016,2017,2018}.{q1,q2,q3,q4}
B. touch [2015,2016,2017,2018].[q1,q2,q3,q4]
C. touch `2015,2016,2017,2018`.`q1,q2,q3,q4`
D. touch {2015.2016.2017.2018}.{q1.q2.q3.q4}
An organization wants to consolidate its entire user information in centralized storage using an X.500- based protocol. Which of the following protocols should be used for this implementation?
A. RADIUS
B. LDAP
C. DNS
D. DHCP
A systems administrator needs to connect to a remote Linux machine to run system updates from within a graphical interface. Which of the following should the administrator use?
A. MATE
B. Wayland
C. VNC
D. Unity
Which of the following Linux server roles should be installed to monitor and log local web traffic?
A. Proxy server
B. AAA server
C. SSH server
D. HTTP server
E. Name server