TM12 Online Practice Questions and Answers
You are performing a quality risk analysis for a CSCI (Computer Software Configuration Item) used to implement a CBIT (Continuous Built-In Test) module of a safety-critical system.
During the quality risk analysis, you are trying to identify the ways in which failures of the CBIT module can occur, for each of them trying to determine the potential causes and likely effects, and the risk level (calculated as the product of three factors: severity, occurrence and detection).
Which of the following risk analysis techniques are you working with?
A. A lightweight product risk analysis technique
B. Failure Mode and Effect Analysis
C. Wide Band Delphi
D. Cost of Exposure
Assume you are currently working on a project developing a system where functional requirements are very well specified. Unfortunately, non-functional requirements do almost not exist.
You are the Test Manager. You have to choose a technique for test selection that allows testing of nonfunctional characteristics, especially reliability.
Which of the following techniques for test selection do you expect being most useful in this scenario?
A. A model-based technique based on the creation of operational profiles
B. Ambiguity reviews
C. Test condition analysis
D. Cause-effect graphing
In the test strategy document your organization declares:
to adopt a V-model development lifecycle, with three formal levels of testing: unit, integration and system testing to use a blended risk-based and regression-averse testing strategy for each level of testing
The following is an excerpt of the "approach" section for the system test plan document of a new project:
"Testing will only use manual tests. Due to the short period of time for test execution, the following activities will be performed in parallel with test execution: Test planning, test analysis and test design.
Basic metrics will be taken for test effort (i.e. person-hours), test cases executed (passed/failed), and incidents (no more metrics, such as code coverage, will be collected)."
In the system test plan, no deviations from the test strategy are described. Based only on the given information, which of the following statements is true?
A. The approach described in the system test plan document is consistent with the test strategy.
B. The approach described in the system test plan document is consistent with the risk-based testing strategy, but it is inconsistent with the regression testing strategy.
C. The approach described in the system test plan document is consistent with the regression testing strategy, but it is inconsistent with the risk-based testing strategy.
D. The approach described the system test plan document is inconsistent with both the risk-based and regression testing strategies.
Based on the historical data of 5 past and similar projects, you have calculated these average numbers of defects detected in system testing:
for each 10000 LOC (lines of code), 200 defects for each person-month of development team effort, 49 defects
You want to use this information to perform estimation for a new project.
The project manager tells you that he/she has estimated 20000 new LOC for this new project.
Four developers work for four months on this project before system testing.
During system testing, 797 defects are discovered.
Assume that the system test of this new project is using the same amount of work as spent in the past projects.
Based on this information only, which of the following statement is certainly true about this project?
A. The code for the new project contains a higher defect density than the code of the past projects.
B. The number of defects found during the system test phase on the new project is approximately proportional to the development team effort.
C. 40000 LOC have been delivered to system testing (against the 20000 LOC planned by the project manager).
D. More LOC than planned have been delivered to system testing with a higher defect density than the past projects.
Which one of the following metrics to be produced needs traceability between the test cases and each item in a proper test basis?
A. Requirements coverage
B. Trends in the lag time from defect reporting to resolution
C. Mean time between failures for the system
D. Cumulative number of reported defects versus cumulative number of resolved defects
After the presentation, you are asked to explain the chart. Assume you have applied a full risk-based testing strategy.
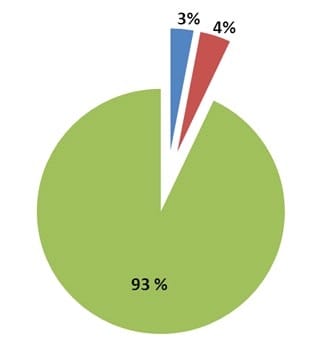
Which of the following answers would you expect to best describe the pie chart?
A. All the risk items have been covered with tests. No more risk items remain to test.
B. According to the full risk-based testing strategy applied, it is very likely that the highest-risk items, tests and bugs remain in the blue and red areas. Therefore, it is very risky to release the application.
C. Only the lowest-risk items, tests and bugs should remain in the blue and red areas. Therefore, the application can be released at any time subject to management of the items identified in those areas.
D. 97 percent of the risk items has been tested. No open bugs or test failures remain. Only 3 percent of risk items remains to be covered by the remaining test.
You are managing the system testing for a SOA based system. The integrated system consists of several subsystems:
a SOA middleware a CRM (Customer Relationship Management) system a BRM (Billing and Revenue Management) system a SMS (Subscriber Management System) system
and you performed a risk analysis based on these subsystems.
At the end of the scheduled period for test execution you produce a first classical report based on the traditional metrics of testing. Test pass/fail status and bug status (open/resolved) That table provides you a distorted picture of the quality risk, because there is no indication of the risk level of the failed tests, the tests not run, or the open bugs. Thus, you produce the following table to solve this distortion issue: In the table above, where you have introduced the concept of risk weighting, the highest risk test or bug report has a score of 1, while the lowest risk test or bug report has a score of 0.04.
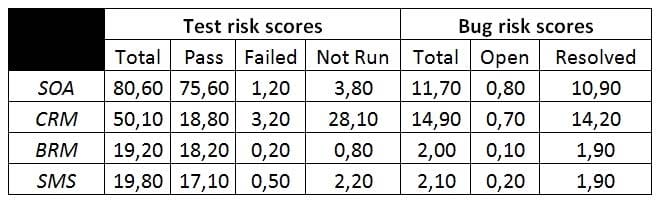
Which of the following subsystems, based on the risk scores of the table, is most risky?
A. SOA
B. CRM
C. BRM
D. SMS
For which of the following activities would the costs be classified as a cost of detection?
A. Writing test specifications according to the test design.
B. Training developers to better understand the new features of the coding language they will use on the project.
C. Re-running a test case, during the system testing phase, to verify that a fix eliminates a previously found defect.
D. Fixing field failures.
During the follow-up phase the following conditions are checked:
X1. The code has been completely reviewed.
X2. All the identified defects have been correctly fixed and the modified code has been compiled
successfully and run through all the static analyzers used by the project without warnings and errors.
X3. The modified code is available under the configuration management system with a new version
number for the specified CI.
If these conditions are fulfilled then the review process terminates.
Which of the following characteristics of a formal review is missing in this description?
A. Defined entry and exit criteria
B. Checklists to be used by the reviewers
C. Deliverables such as reports, evaluation sheets or other review summary sheets
D. Metrics for reporting on the review effectiveness, efficiency, and progress
Your test team consists of four members (Mary, Bob, Mark, Dave) with different interpersonal skills.
The following skills assessment spreadsheet shows the characteristics of the team members with respect to a list of interpersonal-skills (for each characteristic only the member with the highest level of that characteristic is indicated and marked with `X'): On the next project a member of your test team will have to perform some routine tasks requiring collaboration with other teams.

Who in your test team would you expect to be most suitable at doing these tasks?
A. Mary
B. Bob
C. Mark
D. Dave