SECRET-SEN Online Practice Questions and Answers
You start up a Follower and try to connect to it with a REST call using the server certificate, but you get an SSL connection refused error.
What could be the problem and how should you fix it?
A. The certificate does not contain the Follower hostname as a Subject Alternative Name (SAN). Generate a new certificate for the Follower.
B. One of the PostgreSQL ports (5432. 1999) is blocked by the firewall Open those ports.
C. Port 443 is blocked; open that port.
D. The certificate is unnecessary. Use the command option to suppress SSL certificate checking.
What is a main advantage of using dual accounts in password management?
A. Since passwords are cached for both rotation accounts, it ensures the password for an application will not be changed, reducing the amount of blackout dates when a password expires.
B. It ensures passwords are rotated every 90 days, which respects the expected downtime for a system, database, or application
C. It ensures no delays are incurred when the application needs credentials because a password that is currently used by an application will never be changed
D. Since there are two active accounts, it doubles the probability that a system, database, or application will successfully authenticate.
You have a PowerShell script that is being used on 1000 workstations. It requires a Windows Domain credential that is currently hard coded in the script.
What is the simplest solution to remove that credential from the Script?
A. Modify the script to use the CLI SDK to fetch the secret at runtime using Credential Providers installed on each workstation.
B. Modify the script to make a SOAP call to retrieve the secret from the Central Credential Provider.
C. Modify the script to run on WebSphere using the Application Server Credential Provider to retrieve the secret.
D. Use Conjur Summon to invoke the script and inject the secret at run time.
After manually failing over to your disaster recovery site (Site B) for testing purposes, you need to failback to your primary site (Site A).
Which step is required?
A. Contact CyberArk for a new license file.
B. Reconfigure the Vault Conjur Synchronizer to point to the new Conjur Leader.
C. Generate a seed for the new Leader to be deployed in Site A.
D. Trigger autofailover to promote the Standby in Site A to Leader.
During the configuration of Conjur, what is a possible deployment scenario?
A. The Leader and Followers are deployed outside of a Kubernetes environment; Slandbys can run inside a Kubernetes environment.
B. The Conjur Leader cluster is deployed outside of a Kubernetes environment; Followers can run inside or outside the environment.
C. The Leader cluster is deployed outside a Kubernetes environment; Followers and Standbys can run inside or outside the environment.
D. The Conjur Leader cluster and Followers are deployed inside a Kubernetes environment.
Followers are replications of the Leader configured for which purpose?
A. synchronous replication to ensure that there is always an up-to-date database
B. asynchronous replication from the Leader which allows secret reads at scale
C. asynchronous replication from the Leader with read/write operations capability
D. synchronous replication to ensure high availability
Which statement is correct about this message?
Message: "[number-of-deleted-rows] rows has successfully deleted "CEADBR009D Finished vacuum"?
A. It notes the number of records deleted from the database and does not require any action.
B. The user specified for Conjur does not have the appropriate permissions to retrieve the audit database (audit .db).
C. When audit retention was performed, the query on the Ul audit database (audit.db) generated an error.
D. The Vault Conjur Synchronizer successfully deleted the password objects that were marked for deletion in the PVWA.
What is a possible Conjur node role change?
A. A Standby may be promoted to a Leader.
B. A Follower may be promoted to a Leader.
C. A Standby may be promoted to a Follower.
D. A Leader may be demoted to a Standby in the event of a failover.
In the event of a failover of the Vault server from the primary to the DR, which configuration option ensures that a CP will continue being able to refresh its cache?
A. Add the DR Vault IP address to the "Address" parameter in the file main_appprovider.conf.
B. Add the IP address of the DR vault to the "Address" parameter in the file Vault.ini.file on the machine on which the CP is installed.
C. In the Password Vault Web Access UI, add the IP address of the DR Vault in the Disaster Recovery section under Applications > Options.
D. In the Conjur UI, add the IP address of the DR Vault in the Disaster Recovery section under Cluster Config > Credential Provider > Options.
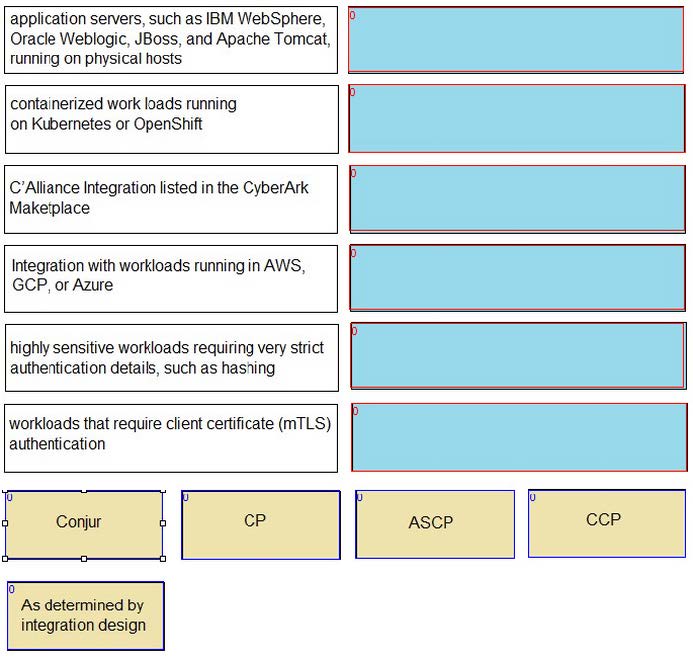
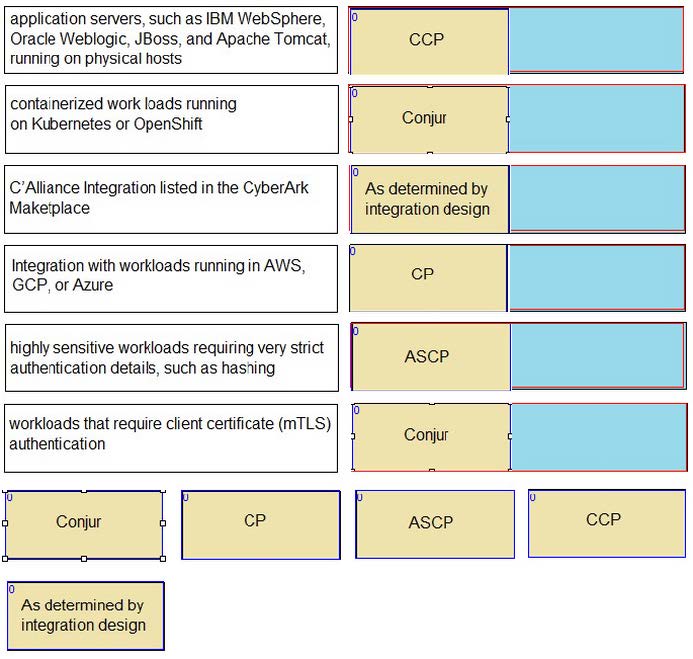
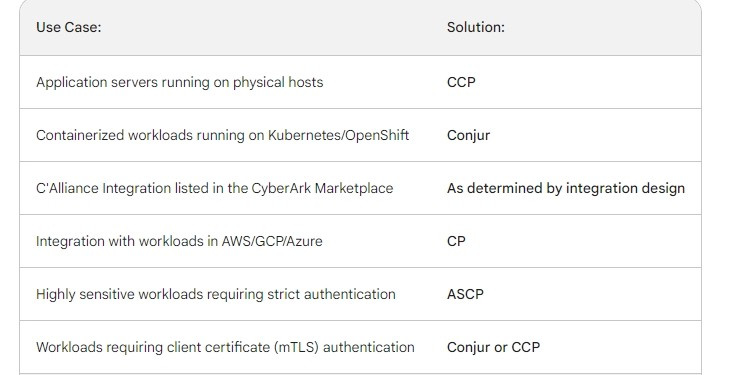
DRAG DROP
Match each use case to the appropriate Secrets Manager Solution.
Select and Place: