SC-300 Online Practice Questions and Answers
HOTSPOT
You have a Microsoft 365 tenant named contoso.com.
Guest user access is enabled.
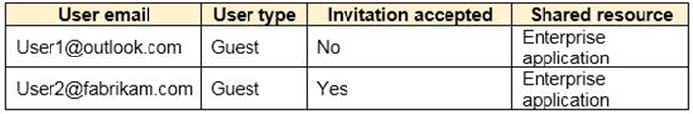
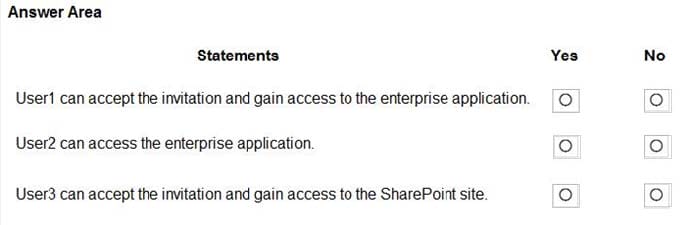
Users are invited to collaborate with contoso.com as shown in the following table.
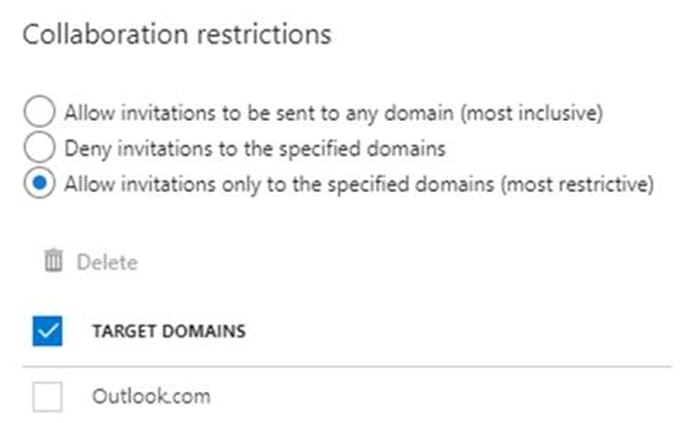
From the External collaboration settings in the Azure Active Directory admin center, you configure the Collaboration restrictions settings as shown in the following exhibit.
From a Microsoft SharePoint Online site, a user invites [email protected] to the site.
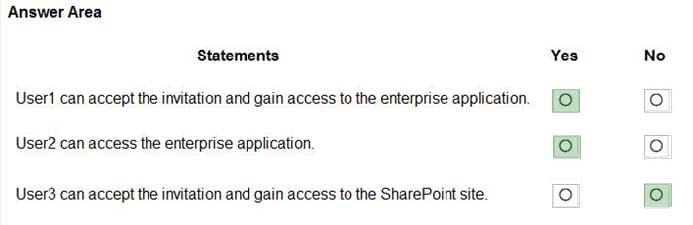
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
HOTSPOT
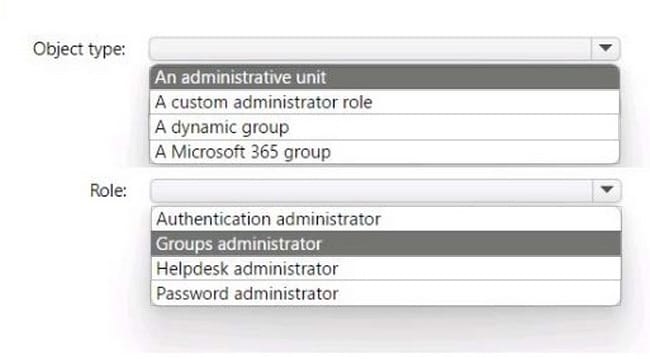
You have a Microsoft 365 tenant that has 5,000 users. One hundred of the users are executives. The executives have a dedicated support team.
You need to ensure that the support team can reset passwords and manage multi-factor authentication (MFA) settings for only the executives. The solution must use the principle of least privilege.
Which object type and Azure Active Directory (Azure AD) role should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
HOTSPOT
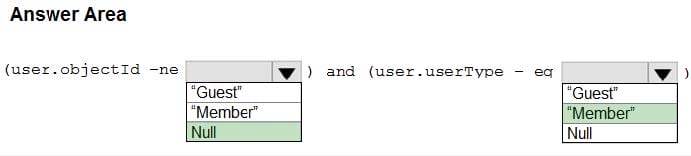
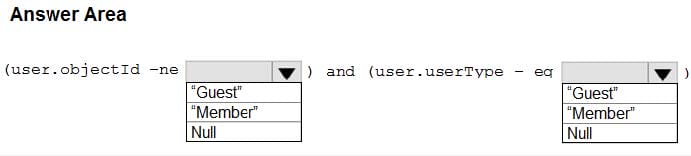
You need to create the LWGroup1 group to meet the management requirements.
How should you complete the dynamic membership rule? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
You have an Azure Active Directory (Azure AD) tenant named contoso.com that has Azure AD Identity Protection policies enforced.
You create an Azure Sentinel instance and configure the Azure Active Directory connector.
You need to ensure that Azure Sentinel can generate incidents based on the risk alerts raised by Azure AD Identity Protection.
What should you do first?
A. Add an Azure Sentinel data connector.
B. Configure the Notify settings in Azure AD Identity Protection.
C. Create an Azure Sentinel playbook.
D. Modify the Diagnostics settings in Azure AD.
You have an Azure Active Directory (Azure AD) tenant.
You open the risk detections report.
Which risk detection type is classified as a user risk?
A. password spray
B. anonymous IP address
C. malicious IP address
D. leaked credentials
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1.
You need to ensure that User1 can create new catalogs and add resources to the catalogs they own.
What should you do?
A. From the Roles and administrators blade, modify the Service support administrator role.
B. From the identity Governance blade, modify the Entitlement management settings.
C. From the Identity Governance blade, modify the roles and administrators for the General catalog
D. From the Roles and administrators blade, modify the Groups administrator role.
You have an Azure AD tenant that contains two users named User1 and User2. You plan to perform the following actions:
1.
Create a group named Group1.
2.
Add User1 and User2 to Group1.
3.
Assign Azure AD roles to Group1.
You need to create Group1.
Which two settings can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Group type: Microsoft 365 - Membership type: Assigned
B. Group type: Security - Membership type: Assigned
C. Group type: Security - Membership type: Dynamic User
D. Group type: Microsoft 365 - Membership type: Dynamic User
E. Group type: Security - Membership type: Dynamic Device
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1.
You need to ensure that users can request access to Site1. The solution must meet the following requirements:
1.
Automatically approve requests from users based on their group membership.
2.
Automatically remove the access after 30 days. What should you do?
A. Create a Conditional Access policy.
B. Create an access package.
C. Configure Role settings in Azure AD Privileged Identity Management.
D. Create a Microsoft Defender for Cloud Apps access policy.
You create a conditional access policy that blocks access when a user triggers a high-severity sign-in alert. You need to test the policy under the following conditions:
1.
A user signs in from another country.
2.
A user triggers a sign-in risk. What should you use to complete the test?
A. the Conditional Access What If tool
B. sign-ins logs in Azure Active Directory (Azure AD)
C. the activity logs in Microsoft Defender for Cloud Apps
D. access reviews in Azure Active Directory (Azure AD)
Your company has two divisions named Contoso East and Contoso West. The Microsoft 365 identity architecture for both divisions is shown in the following exhibit.
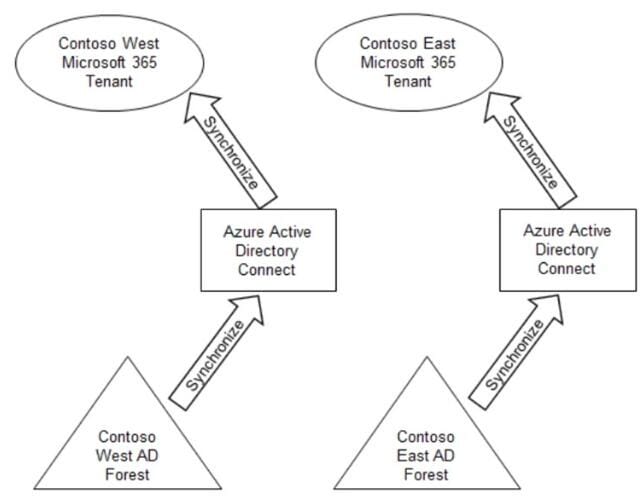
You need to assign users from the Contoso East division access to Microsoft SharePoint Online sites in the Contoso West tenant. The solution must not require additional Microsoft 365 licenses. What should you do?
A. Configure Azure AD Application Proxy in the Contoso West tenant.
B. Invite the Contoso East users as guests in the Contoso West tenant.
C. Deploy a second Azure AD Connect server to Contoso East and configure the server to sync the Contoso East Active Directory forest to the Contoso West tenant.
D. Configure the existing Azure AD Connect server in Contoso East to sync the Contoso East Active Directory forest to the Contoso West tenant.