S10-210 Online Practice Questions and Answers
A number of servers are experiencing slower than expected performance. Analyzing the server, switch, and storage logs do not indicate any issues. You have been asked by the customer to address this issue.
What will improve performance?
A. Increase the current queue depth setting from 1.
B. Change the frame size from 2148 bytes,
C. Decrease the buffer-to-buffer credits setting.
D. Enable write caching functionality for the device driver.
A colleague asks you if the added cost of using encrypting tape drives and sending the tapes off- site is warranted, since your IT organization already has large security investments such as firewalls and database table encryption.
What is your response?
A. The correct firewall rule set would make encrypted tape drives obsolete, but there has not always been strong confidence in the firewall administrators.
B. Encrypted database tables only protect data against inappropriate access by super users such as database or server administrators abusing root privileges.
C. Encrypt tape drives as part of a defense in depth strategy to ensure that one security mechanism being compromised does not expose all information to a malicious user.
D. The existing firewalls and database table encryption do not replace encrypted tape drives, but implementing an intrusion protection system (IPS) will make tape encryption obsolete.
The latest storage utilization report shows that 80% of the current 500 TB of enterprise storage is allocated. The storage administrator must specify the amount of additional storage needed for local copies for approximately half of the active storage.
How much additional storage should the administrator request?
A. 400 TB
B. 300 TB
C. 200 TB
D. 100 TB
What is a common protocol used in cloud communications?
A. WebDAV
B. SCP
C. HTTP
D. CDMI
Click the Exhibit button.
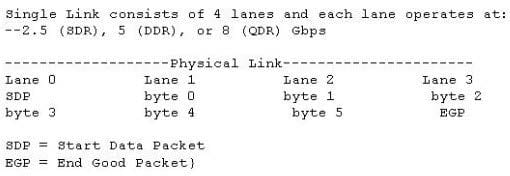
The physical interface shown in the exhibit is taken from which transport protocol?
A. Ethernet
B. FCP
C. FCoE
D. InfiniBand
What are two concerns when trying to migrate from one cloud storage provider to another one? (Choose two.)
A. Stability
B. Accessibility
C. Different drive types
D. CAN protocol compatibility
Which process allows for the reduction of disk space consumption on a shared storage of OS images used by 200 users?
A. Thin provisioning
B. Deduplication
C. Synchronous replication
D. Defragmentation
You are asked to secure management access to your SAN devices.
Which three actions should you perform? (Choose three.)
A. Disable all unused protocols.
B. Limit network access.
C. Create individual access accounts.
D. Write to the syslog server.
E. Enable NTP synchronization.
Which storage related offering serves as intermediaries to multiple cloud storage providers?
A. Cloud storage provider
B. Cloud storage broker
C. Cloud storage gateway
D. Cloud storage shifting
You are using asynchronous storage replication to protect your critical database server. There are no replication agents installed on the database server. After a disaster, you are unable to bring up the database at the DR site.
What is the cause?
A. The database requires replication from a second storage array.
B. The database requires synchronous storage replication.
C. Two copies of databases are required at the DR site to be able to replay transaction logs.
D. An installed agent is required for the database to be quiesce and replicated in crash-consistent state.