QSSA2018 Online Practice Questions and Answers
A system administrator adds RIM B to a two-node environment using the central node as the proxy. The system administrator is using the default virtual proxy for the central node to access the hub.
The system administrator sets up a load balancing rule to have all apps served on both RIM A and RIM B. The system administrator performs the following steps:
1.
Disables the default load balancing rule, "ResourcesOnNonCentralNodes"
2.
Creates a new rule with the Resource filter "App_*" and checks Load balancing
3.
Sets the condition to ((node.name="RIM A" or node.name="RIM B"))
The rule is successfully verified. The system administrator has users log in to the hub and open apps to verify that they are opening on RIM B. However, after multiple users open the same app, there is still NO report of activity on RIM B.
What is causing this issue?
A. There is a rule overlapping the custom load balancing rule
B. The filter should be ((node.name="RIM A") and (node.name="RIM B"))
C. A network connection problem is occurring and the load balancing is NOT working
D. The RIM B Engine has NOT been added to the virtual proxy
A company recently experienced a merger and needs to integrate new users into the Qlik Sense environment.
A system administrator must make sure that the system sizing and the tokens match the requirements for all employees in the future.
The system administrator learns the following information: 450 active Qlik Sense users before the merger 300 new Qlik Sense users 500 current token licenses Reloads must have the same performance as before the merger The number of apps will approximately double
Management requests an estimate from the system administrator about server resources and additional licenses.
Which set of tools should the system administrator use to meet these requirements?
A. Performance Monitor, Reloads Monitor, Scalability Tools, and License Monitor
B. Performance Monitor, License Monitor, Operations Monitor, and Scalability Tools
C. Performance Monitor, Reloads Monitor, QlikCockpit, and License Monitor
D. Performance Monitor, Reloads Monitor, Operations Monitor, and Scalability Tools
A system administrator must set up security that does NOT allow certain users to create objects in published apps. The users that should NOT be able to create objects are in an AD group called LimitedUsers.
Which security rule should the administrator use to meet this requirement?
A. Resource filter: App_* Action: Create Rule Condition: (resource.objectType="charts" and user.group!="LimitedUsers") Context: Both in hub and QMC
B. Resource filter: App.Object_* Action: Create Rule Condition: (resource.objectType="sheet" and user.group!="LimitedUsers")
Context: Only in hub
C. Resource filter: App.Object_* Action: Create Rule Condition: (resource.objectType="charts" and user.group!="LimitedUsers") Context: Both in hub and QMC
D. Resource filter: App_* Action: Create Rule Condition: (resource.objectType="sheet" and user.group!="LimitedUsers") Context: Only in hub
A user must connect to a shared folder named "SharedItems" located on Machine1. All users have permission to view the SharedItems folder.
The user maps the Z: drive to access the "Data" folder located under SharedItems. The user tries to create a new data connection to the shared folder. In the Path property section, only "Computer" and the C: and
D: drives are available.
What should be entered into the data connection path text box?
A. Z:\Data\
B. \\SharedItems\Data\Machine1
C. \\Machine1\SharedItems\Data
D. \\Machine1\Data$\SharedItems
A system administrator creates a new content library to give the developers access to images. The system administrator tests the new library in the Qlik Management Console (QMC) by adding an image into a text and image object in an app on the hub. The developers are unable to see the new content library, but can see the default library.
What should the administrator do to make sure the developers have access to the new content library?
A. Build a security rule to give access to the new content library
B. Have the users create their own individual content libraries in the QMC
C. Have the users upload their own images to the app in the hub
D. Store all required images in the default content library
A Qlik Sense environment has users from Active Directory. A system administrator creates a task to synchronize the users from Active Directory with Qlik Sense.
The system administrator adds a new user to Active Directory, and manually executes the synchronization task in Qlik Sense. The administrator observes that the new user was NOT added to the Qlik Sense environment.
What should the system administrator do to ensure the new user is added?
A. Look for an LDAP filter on the UDC for users from Active Directory
B. Ensure the synchronization task has sufficient rights to find new users
C. Wait 10 minutes for the new user in Active Directory to become visible for Qlik Sense
D. In the UDC, check Sync user data for existing users and re-run the synchronization task
A system administrator installs Qlik Sense Enterprise and is testing the product with a small team of 10 users.
The users report that the page is NOT trusted on their machines and they receive a certificate warning message. When the system administrator tries to validate this feedback on the server, the administrator does NOT see the same issue.
The system administrator completes the following steps in the proxy configuration: Opens all necessary ports Checks in MMC that there is a personal certificate on the server Creates a DNS entry for an easier URL Tries to connect with various Internet browsers on different machines including mobile devices Adds the page to trusted sites in the Internet configurations Installs OpenSSL in the environment
Which steps should the system administrator take to resolve this issue?
A. 1. Generate a valid certificate for organizational needs using OpenSSL
2.
Add the certificate to the personal certificate store of the Qlik Sense Service User
3.
Add the thumbprint of the third-party certificate to the proxy configuration in the QMC
B. 1. Acquire a third-party certificate from a trusted root certificate authority (CA)
2.
Add the certificate to the personal local computer certificate store
3.
Add the thumbprint of the third-party certificate to the proxy configuration in the QMC
C. 1. Acquire a third-party certificate from a trusted root certificate authority (CA)
2.
Add the certificate to the personal certificate store of the Qlik Sense Service User
3.
Add the thumbprint of the third-party certificate to the proxy configuration in the QMC
D. 1. Acquire a third-party certificate from a trusted root certificate authority (CA) including private key
2.
Add the certificate to the personal local computer certificate store
3.
Add the thumbprint of the third-party certificate to the proxy configuration in the QMC
A system administrator must make sure that only members of the "Dev" Active Directory group have the Work stream and are able to create Qlik Sense apps.
The administrator creates a security rule that only allows members of the "Dev" group to create apps, but other users can still see the Personal Work area and are able to create apps.
What is the cause of this issue?
A. The security rules are corrupted
B. The default security rule for app creation is enabled
C. The Create app functionality is disabled for "Dev" group
D. Security rules do NOT impact the Work stream
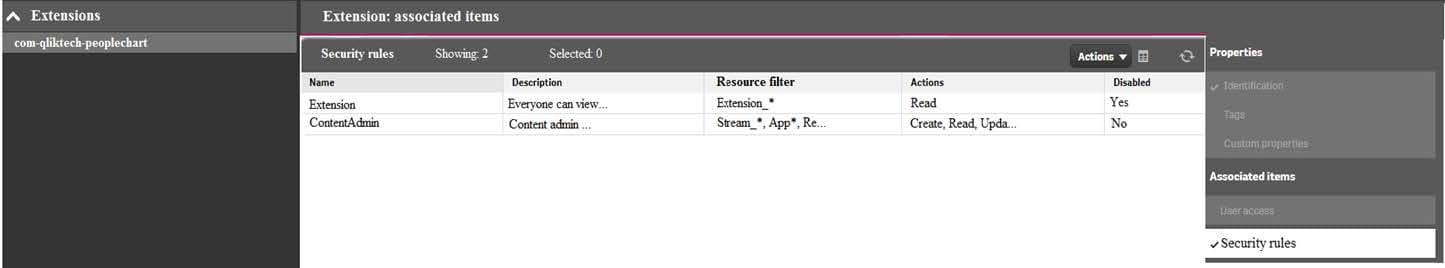
Refer to the exhibit.
One user can see an extension, but another user can NOT see the same extension. The system administrator reviews the extension in the QMC.
What is causing this issue?
A. The user has NOT imported the extension
B. The security rule is set to QMC only
C. The user does NOT have the Content Admin role
D. The user is NOT the owner of the extension
A data architect creates an app in Qlik Sense Desktop with an ODBC data connection from Apache Hive using a single sign-on solution (SSO). When the app is published in the hub, the data connection fails.
A system administrator tests the login credentials for the ODBC connection on the server and is able to access the database. Why does the data connection fail?
A. Qlik Sense Desktop is NOT allowing Qlik Sense server to use Apache Hive
B. The data architect's account is NOT assigned the RootAdmin role
C. The service account user is NOT part of the SSO solution in Apache Hive
D. The Qlik Sense server does NOT support ODBC connections with Apache Hive