PW0-270 Online Practice Questions and Answers
Which statements are true regarding Beacons from an AP in an HT infrastructure BSS that is configured with multiple WLAN profiles? (Choose 3)
A. Beacons can be disabled for security purposes.
B. The BSSID and Source Address are always the same.
C. The Destination Address is always FF:FF:FF:FF:FF:FF.
D. The Receiver address and the BSSID are always the same.
E. When the SSID is "hidden," the ESS subfield of the Capability Information field distinguishes one BSS from another.
F. All Beacons generated by APs contain a TIM information element.
G. The Beacon interval must be the same for all WLANs (SSIDs) supported by a single AP
Using the exhibit as a reference, answer the following.
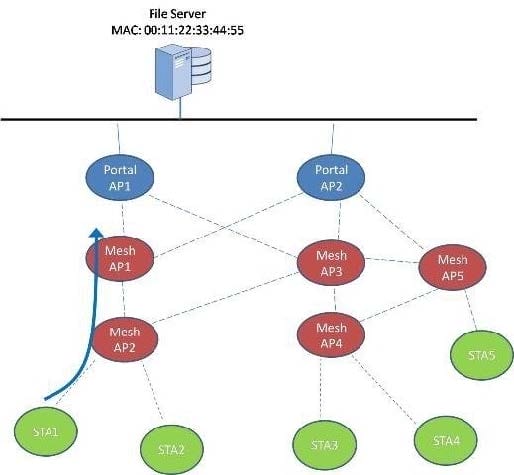
STA1 sent a data frame to Mesh AP2 destined for a local file server on the same subnet with MAC address 00:11:22:33:44:55. Mesh AP2's mesh forwarding algorithm determined that the frame should be forwarded through Mesh AP1.
In the frame sent from Mesh AP2 to Mesh AP1, what is true of the contents of the MAC header? (Choose 3)
A. SA = Mesh AP2's MAC Address
B. RA = Mesh AP1's MAC Address
C. TA = STA1's MAC Address
D. DA = 00:11:22:33:44:55
E. To DS = 0
F. From DS = 1
The Retry subfield is found in which IEEE 802.11 frame field?
A. Sequence Control field
B. Protocol Order field
C. Data Control field
D. Frame Control field
E. MAC Service Data Unit field
F. QoS Control field
What two IEEE 802.11 entities may be used to separate successful transmissions within an EDCA TXOP? (Choose 2)
A. SIFS
B. AIFS
C. ACK
D. CAP
E. PIFS
F. EIFS
G. RIFS
Which statements accurately describe IEEE 802.11 EDCA collision handling in a WMM-compliant infrastructure WLAN? (Choose 2)
A. When frames collide within a QoS STA, data frames from lower priority ACs behave (as it relates to contention) as if there were an external collision on the wireless medium.
B. Collisions between contending EDCAFs within a QoS STA are resolved within the QoS STA
C. When a frame transmission on the wireless medium fails, the transmitter may not transmit another frame from any AC or to any destination until the frame experiencing a failure is successfully transmitted or the max retry count for that frame is reached.
D. The WMM specification requires use of RTS/CTS as part of the EDCAF within each QoS STA to avoid internal collisions between ACs.
E. After frames collide within a QoS STA and the lower priority AC subsequently gains a TXOP, the retry bit in the MAC header must be set to 1 to indicate a retry.
Which statements are true regarding frame acknowledgement in an IEEE 802.11 WLAN? (Choose 3)
A. Following non-QoS Data frames with the More Fragments bit set to 1, the Duration/ID field of the ACK frame is set to a value equal to two SIFS plus the next Data fragment and its ACK.
B. A client station's Reassociation Request frames are only acknowledged with a Reassociation Response from the access point and not with an ACK frame.
C. Probe request acknowledgement (sending of a Probe Response frame) is configurable in the access point and is always linked to SSID broadcast configuration in Beacons.
D. In an EDCA BSS, encrypted Data frames are only acknowledged by client stations, never by access points.
E. Data frame fragments are acknowledged individually (with an ACK frame).
F. The RA field of ACK frames is always obtained from the Address 2 field in the corresponding frame being acknowledged.
Given: Your network consists of HT and ERP access points, and you are implementing VoWiFi with support for U-APSD.
When an ERP handset operating in WMM Power Save mode with a ReceiveDTIMs parameter of TRUE receives a Beacon containing a DTIM indicating queued broadcast traffic, what task is the handset required to perform?
A. The handset must send a PS-Poll frame to the access point for every broadcast frame it receives with the More Data bit set to one.
B. The handset must arbitrate for the medium and immediately issue an RTS directed to the access point with the NAV set to a value of 32,768.
C. The handset must broadcast a CTS-to-Self frame indicating the station's need to control the medium long enough to receive all of the broadcast frames.
D. The handset is to remain awake to receive the broadcast frame(s) following the Beacon that contains the DTIM.
As it pertains to HT L-SIG TXOP Protection, what statement is true?
A. Support for L-SIG TXOP Protection is indicated by HT stations in the L-SIG field of the PLCP header of HT-mixed format frames.
B. Support for L-SIG TXOP Protection is indicated in the HT Capabilities Info field of (re)association request frames sent by ERP, OFDM, and HT-OFDM stations.
C. An L-SIG TXOP protected frame exchange sequence always begins with an RTS/CTS or a CTS-to- Self.
D. L-SIG TXOP Protection is specified for the purpose of protecting OFDM (802.11a/g) and HT- OFDM (802.11n) transmissions from HR/DSSS stations.
What is indicated to a QoS AP when a QoS STA sets U-APSD Flag bits to 1 in (Re) Association frames?
A. Which access categories are both trigger-enabled and delivery-enabled
B. Which user priorities require use of a TSPEC
C. Which access categories require admission control
D. Which user priorities are mapped to access categories
E. Which access categories are scheduled
Given: Before installing a Wi-Fi network, ABC Company performed a spectrum analysis looking for problems. The 2.4 GHz RF spectrum looked like Image-A. After installing an ERP WLAN, ABC Company performed another spectrum analysis during business hours. The 2.4 GHz RF spectrum then looked like Image-B close to an AP on channel 1.

Now the 2.4 GHz RF spectrum looks like Image-C and access points and clients can no longer communicate on channel 1. What is happening on channel 1?
A. The access point's antenna connectors have been tampered with, causing "spike and shear" RF transmissions that are not compatible with the OFDM PHY format. For that reason, client devices cannot receive the AP's transmissions without error.
B. A high-power, narrowband RF interference source on channel 1 is causing the CCA energydetects(ED) function on 802.11 devices to indicate a busy medium because the signal source is above the ED threshold.
C. Stronger transmissions from licensed 2.4 GHz users, such as HAM operators, are compressing the transmissions from the channel 1 access points into the lower portion of the band.
D. The shape of the signals in images B and C indicates that a licensed user in this frequency range has enabled the "guard bands" in an effort to restrict local interference with other systems.
E. Detection of a DFS radar event has discontinued 802.11 operation on channel 1, but the access point's Channel Switch Announcement frame cannot be sent due to the presence of radar.