PW0-071 Online Practice Questions and Answers
You are hired by ABC Company to recommend an appropriate solution for their wireless network. They would like to operate in the 2.4 GHz ISM frequency band and will require data throughput in excess of 10 Mbps. To meet that need, you recommend equipment compliant with the ______ or ______ amendments to the 802.11 standard. (Choose 2)
A. 802.11a
B. 802.11b
C. 802.11i
D. 802.11g
E. 802.11n
Exhibit:
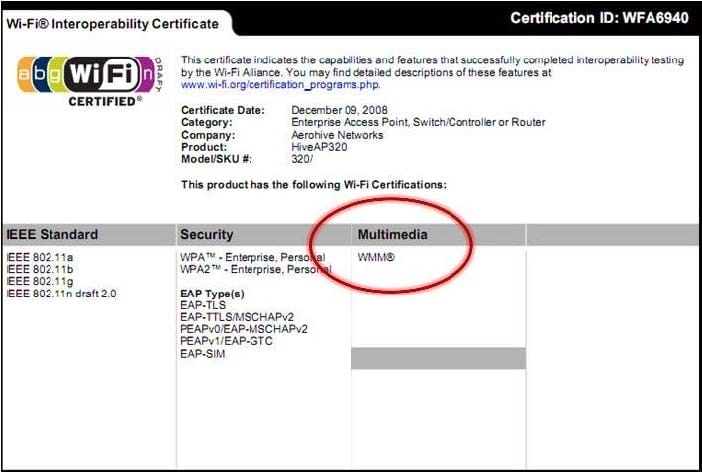
The Wi-Fi Multimedia (WMM) certification, which is illustrated in the exhibit, pertains to which topic?
A. Fast BSS Transition B. Radio Resource Measurement
C. Quality of Service
D. Mesh Networking
E. Dynamic Frequency Selection
F. Security Enhancements
What is a difference between an Infrastructure Basic Service Set (BSS) network and an Ad Hoc network?
A. In an Ad Hoc network, only one WLAN controller is used. A BSS allows multiple WLAN controllers to be connected together to form a mobility domain.
B. An Ad Hoc network allows only legacy security options such as WEP. A BSS allows the creation of a robust security network (RSN) using security methods such as WPA2- Personal.
C. A BSS is recommended for enterprise WLANs, while Ad Hoc deployments are recommended for small and medium businesses.
D. In a BSS, an access point is used for connectivity to the wired network infrastructure. In an Ad Hoc network, client stations communicate directly with each other.
Exhibit:
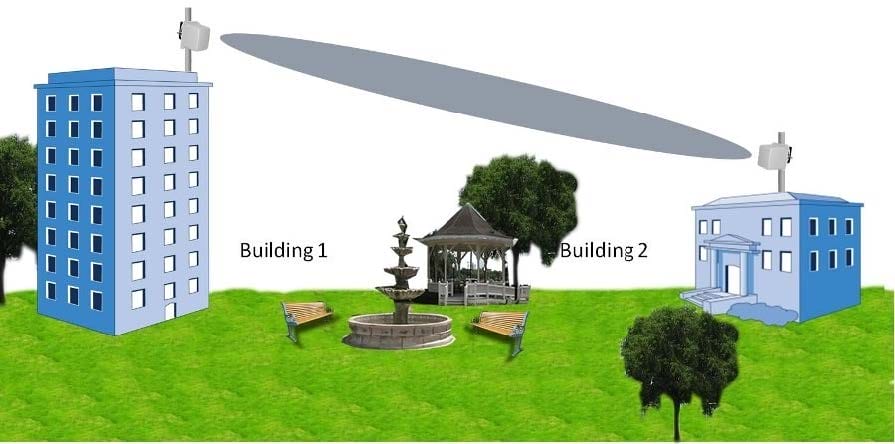
In order to extend network access from Building 1 to Building 2, ABC Company has implemented a Wi-Fi solution. What type of Wi-Fi solution is shown in the figure? (Choose 3)
A. Point-to-point
B. Point-to-multipoint
C. Omnidirectional
D. Semidirectional
E. Mesh
F. Bridge
Given: ABC Company has asked you to recommend a solution that will provide wireless connectivity for desktop computers at various locations in their warehouse. The locations of the desktop computers prevent the use of Cat5e cabling.
What type of client adapter would provide Wi-Fi connectivity to these desktop computers?
A. USB 2.0
B. Mini-PCIe
C. ExpressCard
D. CardBus
E. Secure Digital
What tool is best suited for locating and identifying sources of RF interference, such as microwave ovens?
A. Spectrum analyzer
B. Wi-Fi client utilities
C. Wireless protocol analyzer
D. Predictive analysis software
E. High-gain omni antenna
In what situation is an RF site survey LEAST needed?
A. Office with 3 APs in a multi-tenant building
B. Wi-Fi network with 100 APs at a hospital
C. Telecommuters using a single "remote AP" at home
D. Wi-Fi hot-spot with 10 APs at an airport
Where is the use of a Wireless Internet Service Provider (WISP) most appropriate?
A. Wi-Fi bridging between two or more buildings within a city
B. To provide guest access to the Internet in an office building
C. As hot-spot connectivity in large airports and conference centers
D. Last mile wireless data delivery to homes and businesses
As an alternative to using leased lines to connect two offices on the same campus, your customer wants to implement a Wi-Fi solution. When asked by your customer, what advantages do you cite regarding use of a Wi-Fi infrastructure instead of a leased line? (Choose 2)
A. Wi-Fi implementations are more reliable than leased lines.
B. Wi-Fi implementations have a lower total cost of ownership than leased lines.
C. Wi-Fi implementations are not susceptible to outages caused by inclement weather.
D. Wi-Fi implementations support larger numbers of simultaneous connections than leased lines.
E. Wi-Fi implementations offer more flexibility and easier expansion than leased lines.
Given: In order to reduce travel-related expenses, your CFO has enacted a company policy that eliminates cellular data connectivity for traveling users. Many of your users must connect to the office network during travel, but you have security concerns about wireless hot-spot usage.
To address these concerns, what advice should you give to your traveling users with regard to wireless hot-spot usage? (Choose 2)
A. Only use hot-spots that offer either WPA2-PSK or 802.1X/EAP user-based security.
B. Before connecting at hot-spots, conduct a scan to see if hacking tools are in use.
C. Verify that personal firewall and antivirus software are both enabled before connecting.
D. You should only use fee-based hot-spots which are more secure than free hot-spots.
E. Always use company-provided VPN client software after connecting to the Wi-Fi network.