PT0-003 Online Practice Questions and Answers
HOTSPOT
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
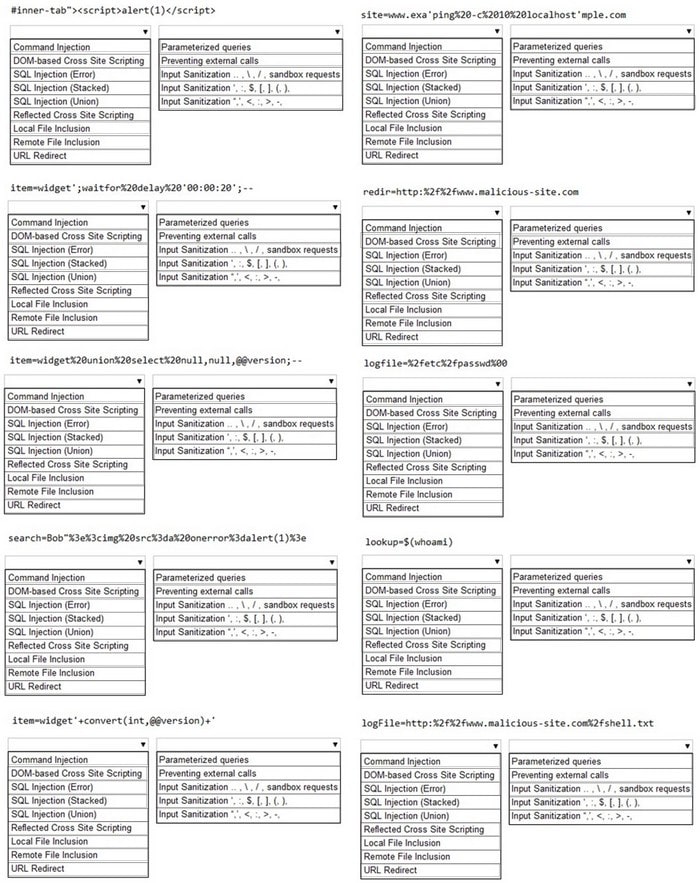
Hot Area:
A penetration tester wants to use the following Bash script to identify active servers on a network:
1 network_addr="192.168.1"
2 for h in {1..254}; do
3 ping -c 1 -W 1 $network_addr.$h > /dev/null
4 if [ $? -eq 0 ]; then
5 echo "Host $h is up" 6 else
7 echo "Host $h is down"
8 fi
9 done
Which of the following should the tester do to modify the script?
A. Change the condition on line 4.
B. Add 2>and1 at the end of line 3.
C. Use seq on the loop on line 2.
D. Replace $h with ${h} on line 3.
While performing an internal assessment, a tester uses the following command:
crackmapexec smb 192.168.1.0/24 -u user.txt -p Summer123@
Which of the following is the main purpose of the command?
A. To perform a pass-the-hash attack over multiple endpoints within the internal network
B. To perform common protocol scanning within the internal network
C. To perform password spraying on internal systems
D. To execute a command in multiple endpoints at the same time
During an engagement, a penetration tester wants to enumerate users from Linux systems by using finger and rwho commands. However, the tester realizes these commands alone will not achieve the desired result. Which of the following is the best tool to use for this task?
A. Nikto
B. Burp Suite
C. smbclient
D. theHarvester
During a security assessment, a penetration tester needs to exploit a vulnerability in a wireless network's authentication mechanism to gain unauthorized access to the network. Which of the following attacks would the tester most likely perform to gain access?
A. KARMA attack
B. Beacon flooding
C. MAC address spoofing
D. Eavesdropping
Which of the following protocols would a penetration tester most likely utilize to exfiltrate data covertly and evade detection?
A. FTP
B. HTTPS
C. SMTP
D. DNS
A penetration tester creates a list of target domains that require further enumeration. The tester writes the following script to perform vulnerability scanning across the domains:
line 1: #!/usr/bin/bash
line 2: DOMAINS_LIST = "/path/to/list.txt"
line 3: while read -r i; do
line 4: nikto -h $i -o scan-$i.txt and
line 5: done
The script does not work as intended. Which of the following should the tester do to fix the script?
A. Change line 2 to {"domain1", "domain2", "domain3", }.
B. Change line 3 to while true; read -r i; do.
C. Change line 4 to nikto $i | tee scan-$i.txt.
D. Change line 5 to done < "$DOMAINS_LIST".
Which of the following post-exploitation activities allows a penetration tester to maintain persistent access in a compromised system?
A. Creating registry keys
B. Installing a bind shell
C. Executing a process injection
D. Setting up a reverse SSH connection
A penetration tester is performing an assessment against a customer's web application that is hosted in a major cloud provider's environment. The penetration tester observes that the majority of the attacks attempted are being blocked by the
organization's WAF.
Which of the following attacks would be most likely to succeed?
A. Reflected XSS
B. Brute-force
C. DDoS
D. Direct-to-origin
A penetration tester is working on a scoping document with a new client. The methodology the client uses includes the following:
Pre-engagement interaction (scoping and ROE) Intelligence gathering (reconnaissance) Threat modeling Vulnerability analysis Exploitation and post exploitation Reporting
Which of the following methodologies does the client use?
A. OWASP Web Security Testing Guide
B. PTES technical guidelines
C. NIST SP 800-115
D. OSSTMM
