PCNSE Online Practice Questions and Answers
When overriding a template configuration locally on a firewall, what should you consider?
A. Only Panorama can revert the override
B. Panorama will lose visibility into the overridden configuration
C. Panorama will update the template with the overridden value
D. The firewall template will show that it is out of sync within Panorama
Which CLI command enables an administrator to check the CPU utilization of the dataplane?
A. show running resource-monitor
B. debug data-plane dp-cpu
C. show system resources
D. debug running resources
How would an administrator monitor/capture traffic on the management interface of the Palo Alto Networks NGFW?
A. Use the debug dataplane packet-diag set capture stage firewall file command.
B. Enable all four stages of traffic capture (TX, RX, DROP, Firewall).
C. Use the debug dataplane packet-diag set capture stage management file command.
D. Use the tcpdump command.
Company.com has an in-house application that the Palo Alto Networks device doesn't identify correctly. A Threat Management Team member has mentioned that this in-house application is very sensitive and all traffic being identified needs to be inspected by the Content-ID engine.
Which method should company.com use to immediately address this traffic on a Palo Alto Networks device?
A. Create a custom Application without signatures, then create an Application Override policy that includes the source, Destination, Destination Port/Protocol and Custom Application of the traffic.
B. Wait until an official Application signature is provided from Palo Alto Networks.
C. Modify the session timer settings on the closest referanced application to meet the needs of the in-house application
D. Create a Custom Application with signatures matching unique identifiers of the in-house application traffic
Review the images. A firewall policy that permits web traffic includes the global-logs policy as depicted.
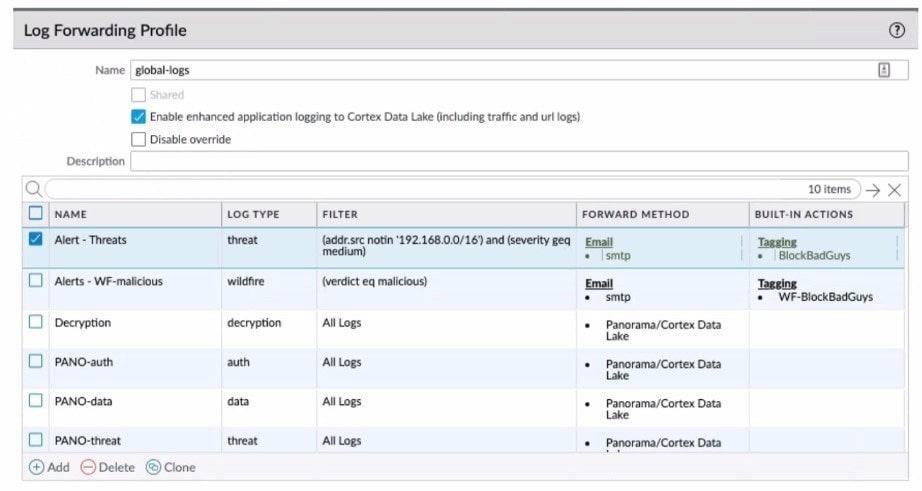
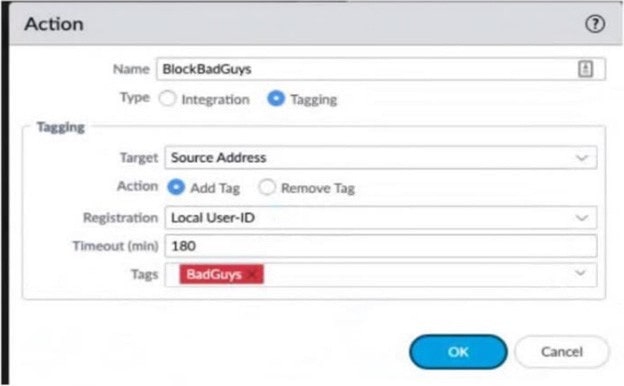
What is the result of traffic that matches the "Alert - Threats" Profile Match List?
A. The source address of SMTP traffic that matches a threat is automatically blocked as BadGuys for 180 minutes.
B. The source address of traffic that matches a threat is automatically blocked as BadGuys for 180 minutes.
C. The source address of traffic that matches a threat is automatically tagged as BadGuys for 180 minutes.
D. The source address of SMTP traffic that matches a threat is automatically tagged as BadGuys for 180 minutes.
An administrator discovers that a file blocked by the WildFire inline ML feature on the firewall is a false-positive action. How can the administrator create an exception for this particular file?
A. Add partial hash and filename in the file section of the WildFire inline ML tab of the Antivirus profile.
B. Set the WildFire inline ML action to allow for that protocol on the Antivirus profile.
C. Add the related Threat ID in the Signature exceptions tab of the Antivirus profile.
D. Disable the WildFire profile on the related Security policy.
An engineer manages a high availability network and requires fast failover of the routing protocols. The engineer decides to implement BFD. Which three dynamic routing protocols support BFD? (Choose three.)
A. OSPF
B. RIP
C. BGP
D. IGRP
E. OSPFv3 virtual link
A security engineer has configured a GlobalProtect portal agent with four gateways.
Which GlobalProtect Gateway will users connect to based on the chart provided?
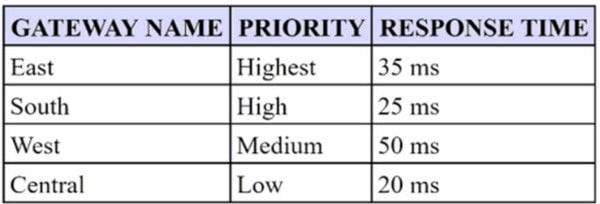
A. East
B. South
C. West
D. Central
Why are external zones required to be configured on a Palo Alto Networks NGFW in an environment with multiple virtual systems?
A. To allow traffic between zones in different virtual systems while the traffic is leaving the appliance
B. External zones are required because the same external zone can be used on different virtual systems
C. To allow traffic between zones in different virtual systems without the traffic leaving the appliance
D. Multiple external zones are required in each virtual system to allow the communications between virtual systems
An administrator wants to prevent users from unintentionally accessing malicious domains where data can be exfiltrated through established connections to remote systems. From the Pre-defined Categories tab within the URL Filtering profile what is the right configuration to prevent such connections?
A. Set the malware category to block
B. Set the Command and Control category to block
C. Set the phishing category to override
D. Set the hacking category to continue