PCDRA Online Practice Questions and Answers
In the Cortex XDR console, from which two pages are you able to manually perform the agent upgrade action? (Choose two.)
A. Asset Management
B. Agent Installations
C. Action Center
D. Endpoint Administration
Which statement is correct based on the report output below?
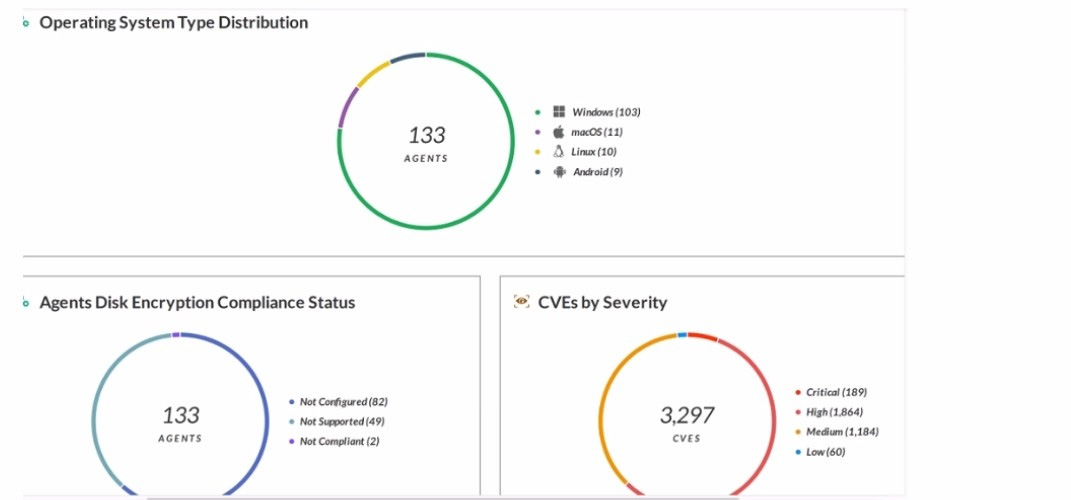
A. Host Inventory Data Collection is enabled.
B. 3,297 total incidents have been detected.
C. Forensic inventory data collection is enabled.
D. 133 agents have full disk encryption.
Which module provides the best visibility to view vulnerabilities?
A. Live Terminal module
B. Device Control Violations module
C. Host Insights module
D. Forensics module
Can you disable the ability to use the Live Terminal feature in Cortex XDR?
A. Yes, via the Cortex XDR console or with an installation switch.
B. No, a separate installer package without Live Terminal is required.
C. No, it is a required feature of the agent.
D. Yes, via Agent Settings Profile.
What does the following output tell us?
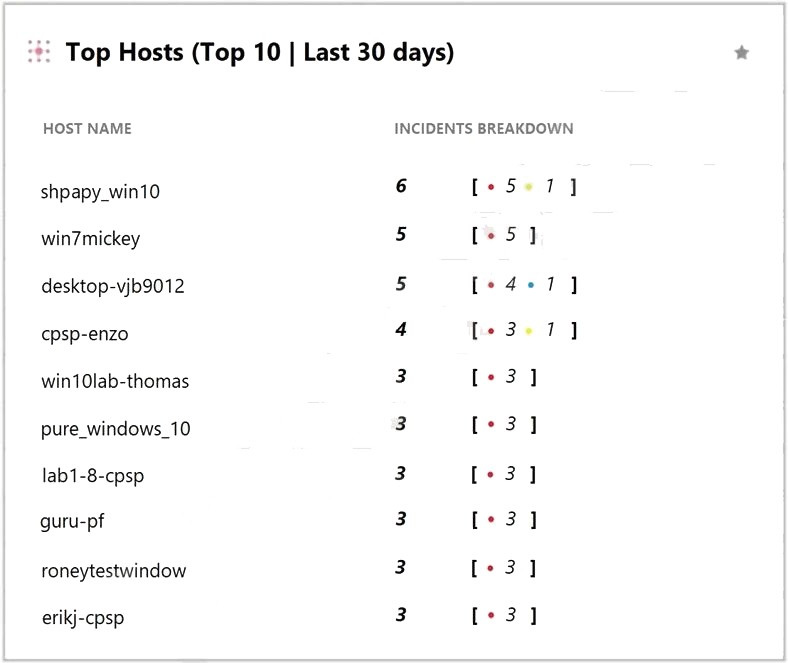
A. There is one low severity incident.
B. Host shpapy_win10 had the most vulnerabilities.
C. There is one informational severity alert.
D. This is an actual output of the Top 10 hosts with the most malware.
Which function describes the removal of a specific file from its location on a local or removable drive to a protected folder to prevent the file from being executed?
A. Search and destroy
B. Isolation
C. Quarantine
D. Flag for removal
When investigating security events, which feature in Cortex XDR is useful for reverting the changes on the endpoint?
A. Remediation Automation
B. Machine Remediation
C. Automatic Remediation
D. Remediation Suggestions
Where would you view the WildFire report in an incident?
A. next to relevant Key Artifacts in the incidents details page
B. under Response --> Action Center
C. under the gear icon --> Agent Audit Logs
D. on the HUB page at apps.paloaltonetworks.com
When using the "File Search and Destroy" feature, which of the following search hash type is supported?
A. SHA256 hash of the file
B. AES256 hash of the file
C. MD5 hash of the file
D. SHA1 hash of the file
As a Malware Analyst working with Cortex XDR you notice an alert suggesting that there was a prevented attempt to open a malicious Word document. You learn from the WildFire report and AutoFocus that this document is known to have been used in Phishing campaigns since 2018. What steps can you take to ensure that the same document is not opened by other users in your organization protected by the Cortex XDR agent?
A. Enable DLL Protection on all endpoints but there might be some false positives.
B. Create Behavioral Threat Protection (BTP) rules to recognize and prevent the activity.
C. No step is required because Cortex shares IOCs with our fellow Cyber Threat Alliance members.
D. No step is required because the malicious document is already stopped.