PCCSE Online Practice Questions and Answers
Which container scan is constructed correctly?
A. twistcli images scan -u api -p api --address https://us-west1.cloud.twistlock.com/us-3-123456789 --container myimage/latest
B. twistcli images scan --docker-address https://us-west1.cloud.twistlock.com/us-3-123456789 myimage/latest
C. twistcli images scan -u api -p api --address https://us-west1.cloud.twistlock.com/us-3-123456789 --details myimage/latest
D. twistcli images scan -u api -p api --docker-address https://us-west1.cloud.twistlock.com/us-3-123456789 myimage/latest
A customer finds that an open alert from the previous day has been resolved. No auto-remediation was Configured. Which two reasons explain this change in alert status? (Choose two.)
A. user manually changed the alert status.
B. policy was changed.
C. resource was deleted.
D. alert was sent to an external integration.
Which three steps are involved in onboarding an account for Data Security? (Choose three.)
A. Create a read-only role with in-line policies
B. Create a Cloudtrail with SNS Topic
C. Enable Flow Logs
D. Enter the RoleARN and SNSARN
E. Create a S3 bucket
An administrator has deployed Console into a Kubernetes cluster running in AWS. The administrator also has Configured a load balancer in TCP passthrough mode to listen on the same ports as the default Prisma Compute Console
configuration. In the build pipeline, the administrator wants twistcli to talk to Console over HTTPS.
Which port will twistcli need to use to access the Prisma Compute APIs?
A. 8084
B. 443
C. 8083
D. 8081
The Prisma Cloud administrator has Configured a new policy.
Which steps should be used to assign this policy to a compliance standard?
A. Edit the policy, go to step 3 (Compliance Standards), click + at the bottom, select the compliance standard, fill in the other boxes, and then click Confirm.
B. Create the Compliance Standard from Compliance tab, and then select Add to Policy.
C. Open the Compliance Standards section of the policy, and then save.
D. Custom policies cannot be added to existing standards.
What is the behavior of Defenders when the Console is unreachable during upgrades?
A. Defenders continue to alert, but not enforce, using the policies and settings most recently cached before upgrading the Console.
B. Defenders will fail closed until the web-socket can be re-established.
C. Defenders will fail open until the web-socket can be re-established.
D. Defenders continue to alert and enforce using the policies and settings most recently cached before upgrading the Console.
What are two key requirements for integrating Okta with Prisma Cloud when multiple Amazon Web Services (AWS) cloud accounts are being used? (Choose two.)
A. Super Administrator permissions
B. A valid subscription for the IAM security module
C. An Okta API token for the primary AWS account
D. Multiple instances of the Okta app
Which three actions are available for the container image scanning compliance rule? (Choose three.)
A. Allow
B. Snooze
C. Block
D. Ignore
E. Alert
Which IAM RQL query would correctly generate an output to view users who enabled console access with both access keys and passwords?
A. config from network where api.name = `aws-iam-get-credential-report' AND json.rule = cert_1_active is true or cert_2_active is true and password_enabled equals "true"
B. config from cloud.resource where api.name = 'aws-iam-get-credential-report' AND json.rule = access_key_1_active is true or access_key_2_active is true and password_enabled equals "true"
C. config from cloud.resource where api.name = 'aws-iam-get-credential-report' AND json.rule = access_key_1_active is false or access_key_2_active is true and password_enabled equals "*"
D. config where api.name = `aws-iam-get-credential-report' AND json.rule= access_key_1_active is true or access_key_2_active is true and password_enabled equals "true"
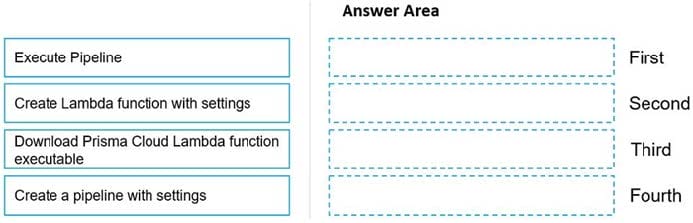
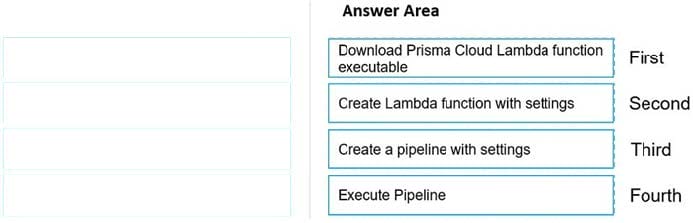
DRAG DROP
Move the steps to the correct order to set up and execute a serverless scan using AWS DevOps.
Select and Place: