OMG-OCSMP-MBI300 Online Practice Questions and Answers
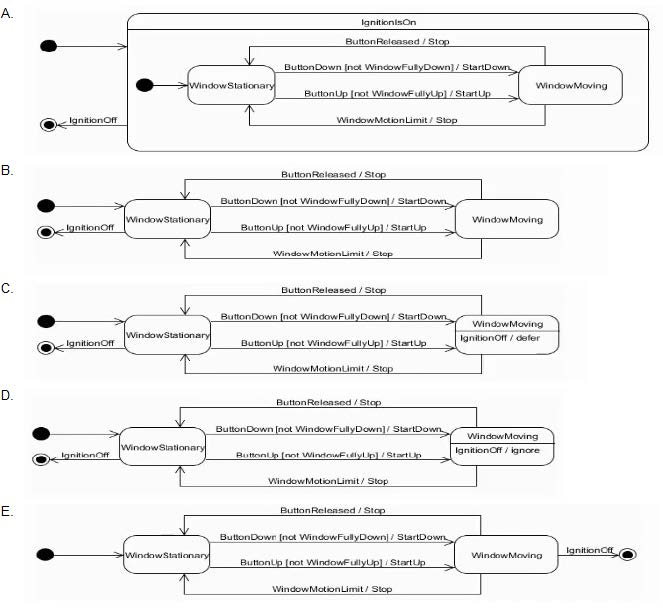
Choose the correct answer The following are behavioral requirements for an automobile electric window
(1)
When the window button is moved into the up position and the window is not fully up the window shall begin to move up
(2)
When the window button is moved into the down position and the window is not hilly down, the window shall begin to move down
(3)
When the window button is released or the window reaches the fully up or fully down position, the window shall stop moving
(4)
Requirements (1-3) apply when the ignition is on. However, turning the ignition off shall lake effect only after the window has stopped moving. Which state machine diagram fragment describes the required behavior?
A.
Option A
B.
Option B
C.
Option C
D.
Option D
E.
Option E
Choose the correct answer Given the following diagram:
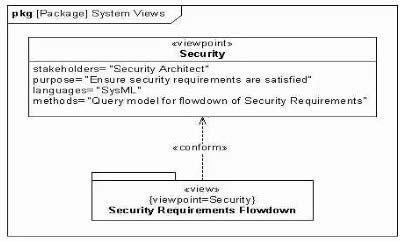
Which statement is true?
A. The Security viewpoint conforms to the requirements specified by the Security view
B. The Security view is intended to address the purpose specified by the Security viewpoint
C. The Security view imports the Security viewpoint to ensure the security requirements are satisfied
D. The Security viewpoint imports the model elements associated with flowing down the security requirements
Choose the correct answer.
The area of a rectangle is calculated through analysis of its height and width:
How is this represented in a model?
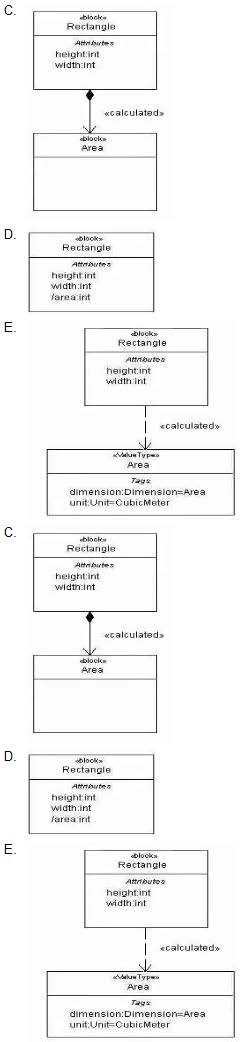
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
Choose the correct answer.
Assume the following state machine is In the T-1 State when ev Z occurs:
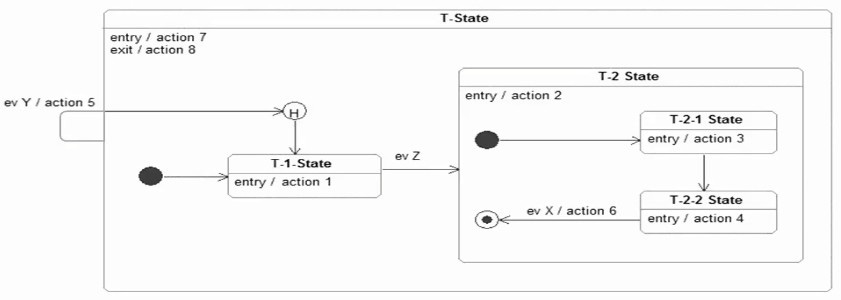
Subsequently ev Voccurs.
Which sequence of actions will be executed?
A. action 2
B. action 2 action 3
C. action 2 action 4
D. action 3
E. action 4
F. action 5 action 2 action 3
G. action 5 action 2 action 4
H. action 5 action 1 action 2 action 3
I. action 5 action 1 action 2 action4
J. action 8 action 5 action 7 action 2 action 3
K. action 8 action 5 action 7 action 2 action 3 action 4
L. action 8 action 5 action 7 action 2 action 4
Choose the correct answer. Given the following block:

Which SysML construct correctly models Geographic Coordinate?

A. Option A
B. Option B
C. Option C
D. Option D
Choose the correct answer.
Given the following package diagram depicting profile and model library relationships to a user model.
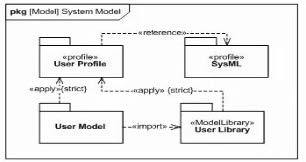
The User Profile extends SysML with two new stereotypes of Block Hardware and Software. Which bdd fragment is valid, yet does not contain unnecessary or redundant information?
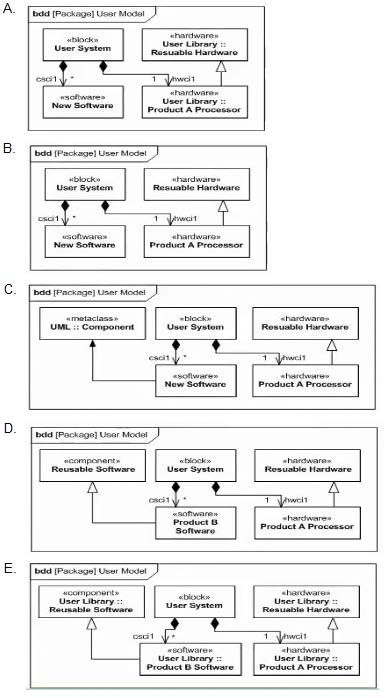
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
Choose the correct answer. Given the following diagram:
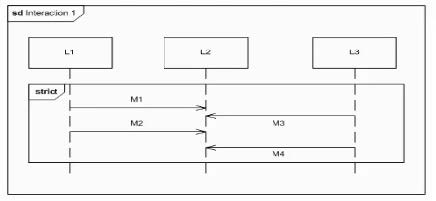
Which message ordering is valid?
A. M1, M2. M3, M4
B. M3. M1. M2, M4
C. M3, M4. M1, M2
D. None of these orderings is valid.
Choose the correct answer
What is an effective and efficient approach to project modeling standards and conventions?
A. Every project should create its own domain specific profile to describe modeling standards and conventions
B. Organizations should create specific modeling standards and conventions to ensure modeling consistency across projects
C. The SysML specification alone is sufficient to describe modeling standards and conventions when the modeling tool has a proper implementation of SysML
D. The SysML specification and the modeling tool documentation are sufficient to describe modeling standards and conventions
Choose the correct answer
Which statement is true about the read only keyword when it appears next to a property?
A. It states that the corresponding property is provided for reading purposes only
B. It specifies that the corresponding property cannot be redefined
C. It specifies that the value of the corresponding property cannot change during the lifetime of its owner.
D. It specifies that the value of the corresponding property can be changed by its owner, but can only be read by other blocks
Choose the correct answer
How would a modeler refine a use case textual narrative?
A. provide a detailed definition of the use case using a behavioral diagram
B. specify all of the triggers preconditions, and post conditions for the use case
C. specify all extension points for extend use cases and specify all secondary actors
D. provide a complete textual description of the main flow and alternative/exceptional flows for the use case