NSE8_812 Online Practice Questions and Answers
You are creating the CLI script to be used on a new SD-WAN deployment You will have branches with a different number of internet connections and want to be sure there is no need to change the Performance SLA configuration in case more connections are added to the branch.
The current configuration is:
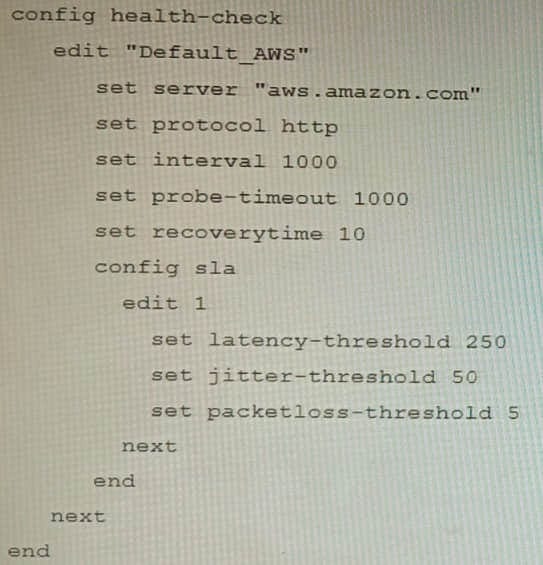
Which configuration do you use for the Performance SLA members?
A. set members any
B. set members 0
C. current configuration already fulfills the requirement
D. set members all
You want to use the MTA adapter feature on FortiSandbox in an HA-Cluster. Which statement about this solution is true?
A. The configuration of the MTA Adapter Local Interface is different than on port1.
B. The MTA adapter is only available in the primary node.
C. The MTA adapter mode is only detection mode.
D. The configuration is different than on a standalone device.
Review the following FortiGate-6000 configuration excerpt:
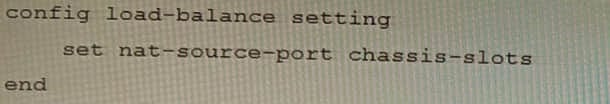
Based on the configuration, which statement is correct regarding SNAT source port partitioning behavior?
A. It dynamically distributes SNAT source ports to operating FPCs or FPMs.
B. It is the default SNAT configuration and preserves active sessions when an FPC or FPM goes down.
C. It statically distributes SNAT source ports to operating FPCs or FPMs
D. It equally distributes SNAT source ports across chassis slots.
A retail customer with a FortiADC HA cluster load balancing five webservers in L7 Full NAT mode is receiving reports of users not able to access their website during a sale event. But for clients that were able to connect, the website works fine.
CPU usage on the FortiADC and the web servers is low, application and database servers are still able to handle more traffic, and the bandwidth utilization is under 30%.
Which two options can resolve this situation? (Choose two.)
A. Change the persistence rule to LB_PERSIS_SSL_SESSJD.
B. Add more web servers to the real server poof
C. Disable SSL between the FortiADC and the web servers
D. Add a connection-pool to the FortiADC virtual server
Which two statements are correct on a FortiGate using the FortiGuard Outbreak Protection Service (VOS)? (Choose two.)
A. The FortiGuard VOS can be used only with proxy-base policy inspections.
B. If third-party AV database returns a match the scanned file is deemed to be malicious.
C. The antivirus database queries FortiGuard with the hash of a scanned file
D. The AV engine scan must be enabled to use the FortiGuard VOS feature
E. The hash signatures are obtained from the FortiGuard Global Threat Intelligence database.
Refer to the exhibit showing a firewall policy configuration.
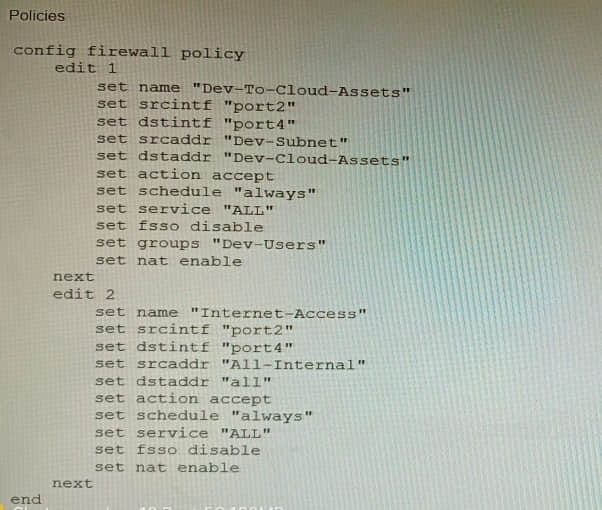
To prevent unauthorized access of their cloud assets, an administrator wants to enforce authentication on firewall policy ID 1. What change does the administrator need to make?
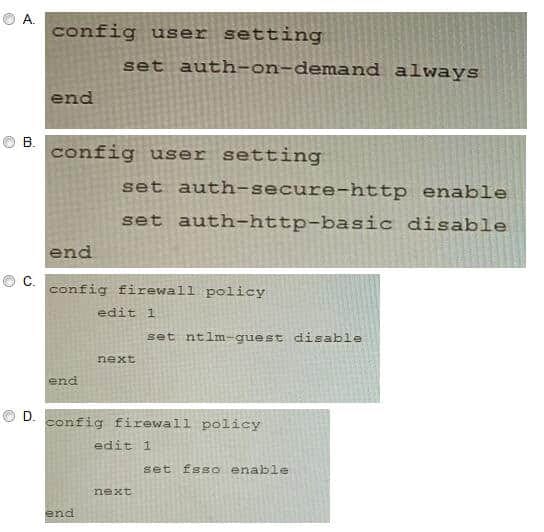
A. Option A
B. Option B
C. Option C
D. Option D
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1).
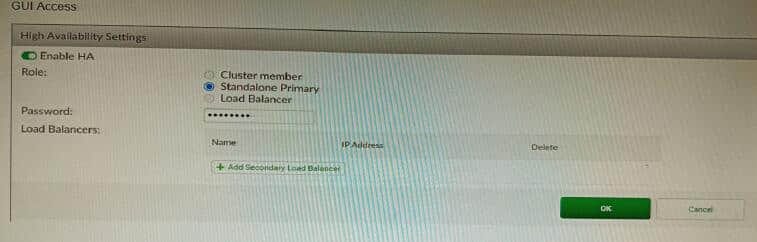
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?
A. FAC2 can only process requests when FAC1 fails.
B. FAC2 can have its HA interface on a different network than FAC1.
C. The FortiToken license will need to be installed on the FAC2.
D. FSSO sessions from FAC1 will be synchronized to FAC2.
Refer to the exhibit showing an SD-WAN configuration. According to the exhibit, if an internal user pings 10.1.100.2 and 10.1.100.22 from subnet 172.16.205.0/24, which outgoing interfaces will be used?
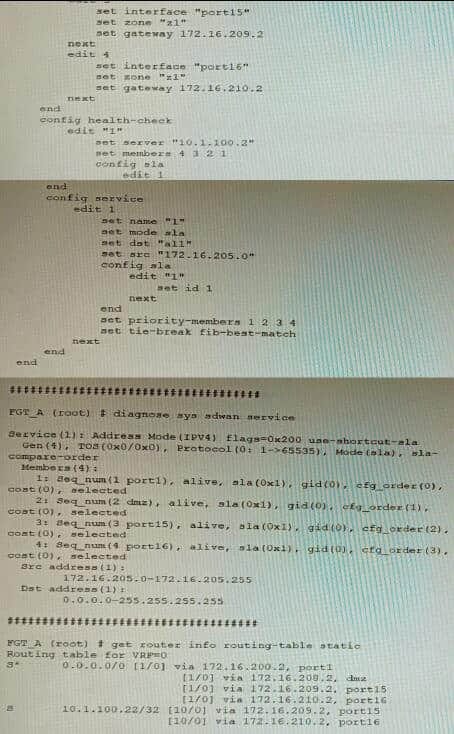
A. port16 and port1
B. port1 and port1
C. port16 and port15
D. port1 and port15
Refer to the CLI output:
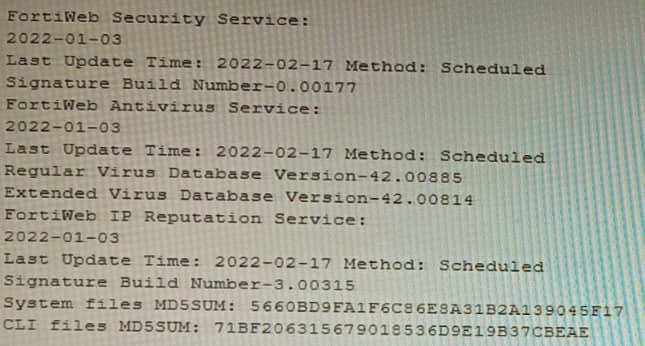
Given the information shown in the output, which two statements are correct? (Choose two.)
A. Geographical IP policies are enabled and evaluated after local techniques.
B. Attackers can be blocked before they target the servers behind the FortiWeb.
C. The IP Reputation feature has been manually updated
D. An IP address that was previously used by an attacker will always be blocked
E. Reputation from blacklisted IP addresses from DHCP or PPPoE pools can be restored
An HA topology is using the following configuration:
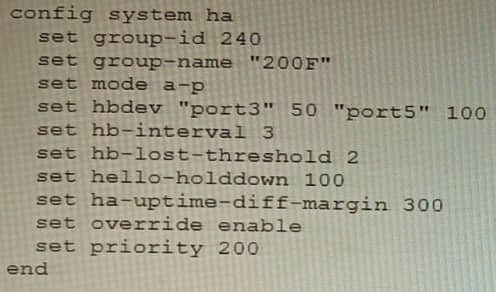
Based on this configuration, how long will it take for a failover to be detected by the secondary cluster member?
A. 600ms
B. 200ms
C. 300ms
D. 100ms