NSE7_SDW-7.0 Online Practice Questions and Answers
Which two statements describe how IPsec phase 1 main mode is different from aggressive mode when performing IKE negotiation? (Choose two )
A. A peer ID is included in the first packet from the initiator, along with suggested security policies.
B. XAuth is enabled as an additional level of authentication, which requires a username and password.
C. A total of six packets are exchanged between an initiator and a responder instead of three packets.
D. The use of Diffie Hellman keys is limited by the responder and needs initiator acceptance.
Refer to the exhibit.
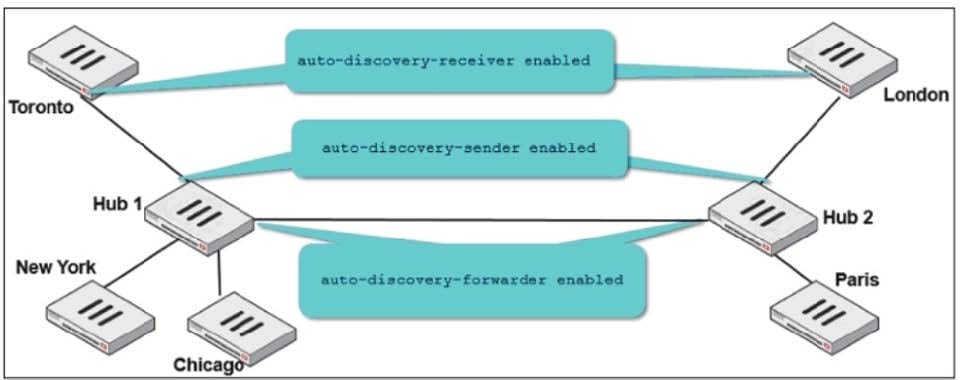
Two hub-and-spoke groups are connected through a site-to-site IPsec VPN between Hub 1 and Hub 2. The administrator configured ADVPN on both hub-and-spoke groups.
Which two outcomes are expected if a user in Toronto sends traffic to London? (Choose two.)
A. London generates an IKE information message that contains the Toronto public IP address.
B. Traffic from Toronto to London triggers the dynamic negotiation of a direct site-to-site VPN.
C. Toronto needs to establish a site-to-site tunnel with Hub 2 to bypass Hub 1.
D. The first packets from Toronto to London are routed through Hub 1 then to Hub 2.
Refer to the exhibit. Exhibit A
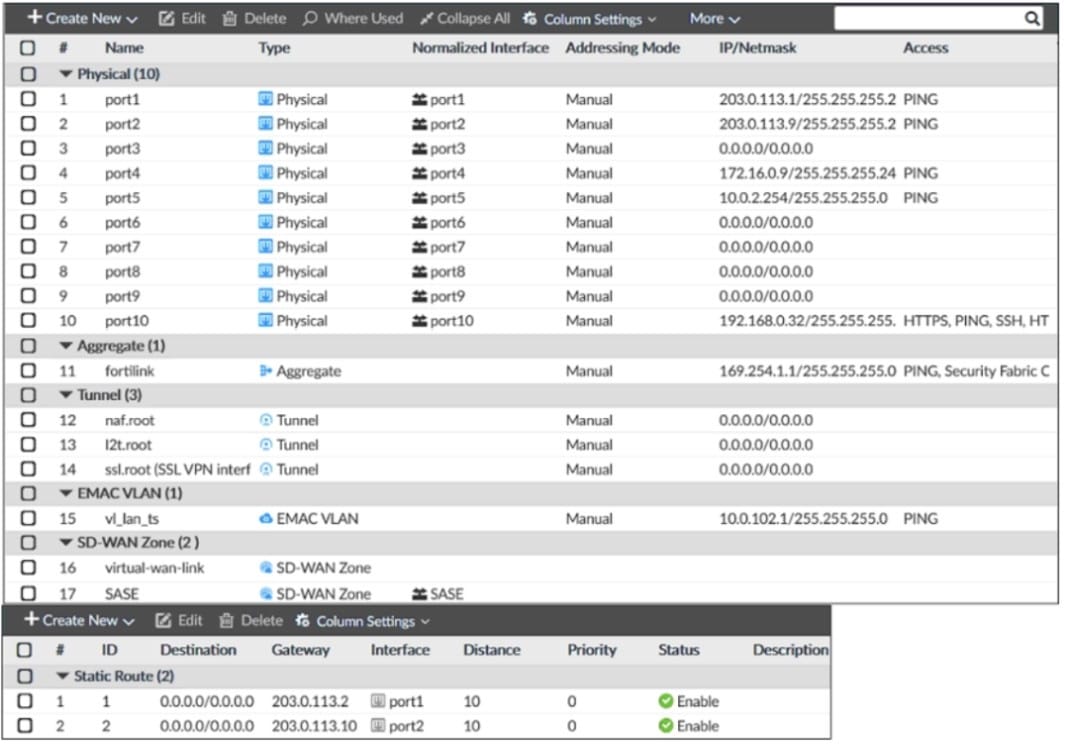
Exhibit B
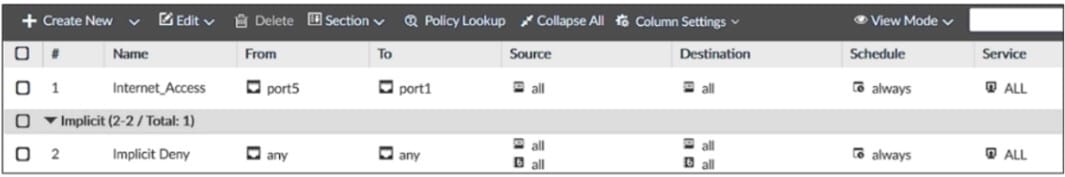
Exhibit A shows the system interface with the static routes and exhibit B shows the firewall policies on the managed FortiGate.
Based on the FortiGate configuration shown in the exhibits, what issue might you encounter when creating an SD-WAN zone for port1 and port2?
A. port1 is assigned a manual IP address.
B. port1 is referenced in a firewall policy.
C. port2 is referenced in a static route.
D. port1 and port2 are not administratively down.
Which two statements about SD-WAN central management are true? (Choose two.)
A. The objects are saved in the ADOM common object database.
B. It does not support meta fields.
C. It uses templates to configure SD-WAN on managed devices.
D. It supports normalized interfaces for SD-WAN member configuration.
Refer to exhibits.
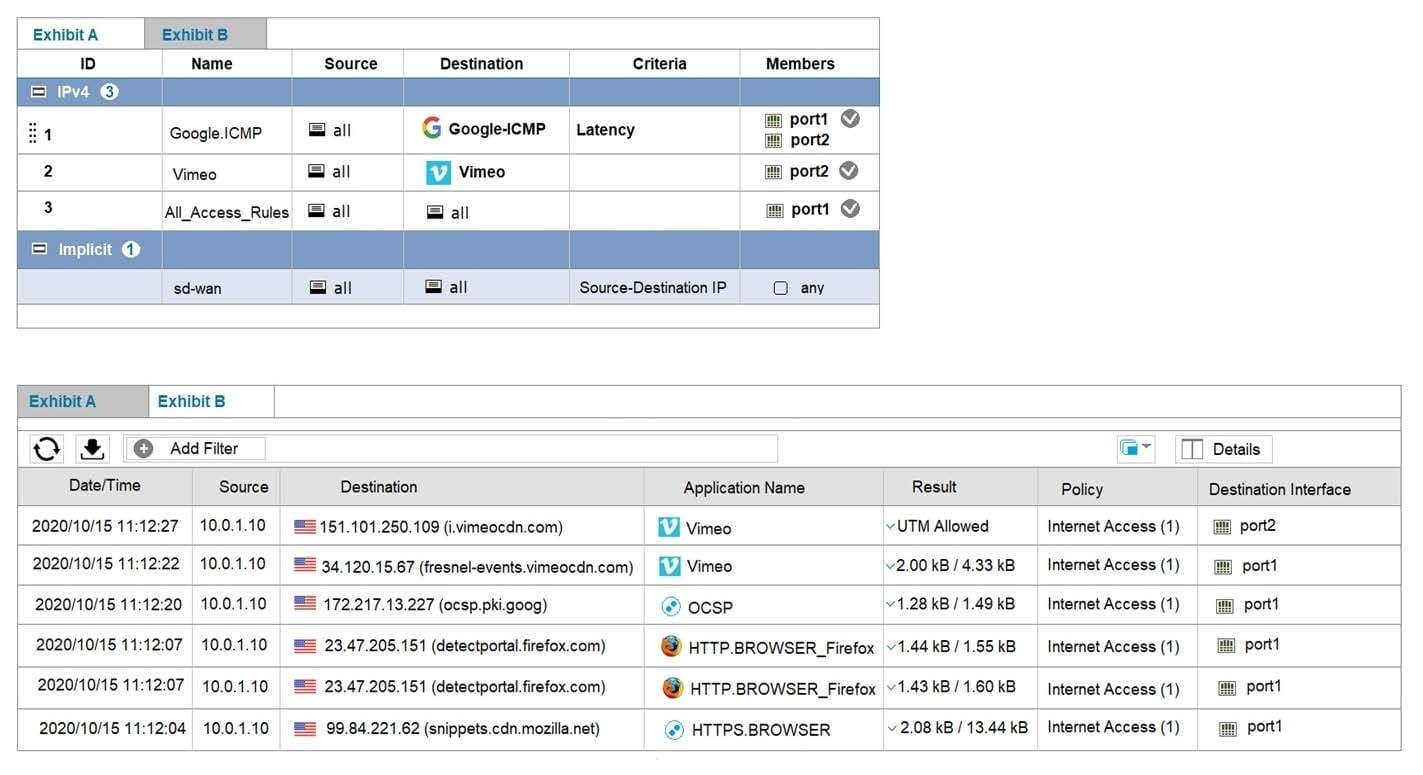
Exhibit A shows the SD-WAN rules and exhibit B shows the traffic logs. The SD-WAN traffic logs reflect how FortiGate processed traffic. Which two statements about how the configured SD-WAN rules are processing traffic are true? (Choose two.)
A. The implicit rule overrides all other rules because parameters widely cover sources and destinations.
B. SD-WAN rules are evaluated in the same way as firewall policies: from top to bottom.
C. The All_Access_Rules rule load balances Vimeo application traffic among SD-WAN member interfaces.
D. The initial session of an application goes through a learning phase in order to apply the correct rule.
Which three protocols are available only on the command line to configure as performance SLA status check? (Choose three.)
A. smtp
B. tcp-echo
C. twamp
D. udp-echo
E. icmp
When attempting to establish an IPsec tunnel to FortiGate, all remote users match the FIRST_VPN IPsec VPN. This includes remote users that want to connect to the SECOND_VPN IPsec VPN. Which two configuration changes must you make on both IPsec VPNs so that remote users can connect to their intended IPsec VPN? (Choose two.)
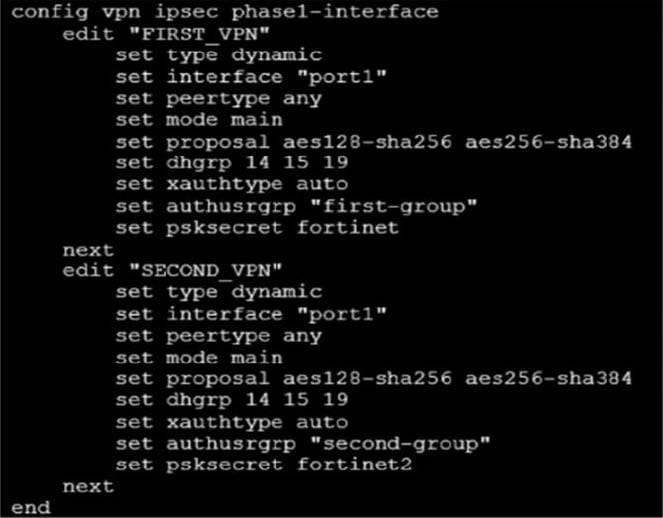
A. Configure different proposals.
B. Configure a unique peer ID.
C. Change the IKE mode to aggressive.
D. Configure different Diffie Hellman groups.
Which two protocols in the IPsec suite are most used for authentication and encryption? (Choose two)
A. Secure Shell (SSH)
B. Encapsulating Security Payload (ESP)
C. Internet Key Exchange (IKE)
D. Transport Layer Security (TLS)
E. Security Association (SA)
Which two benefits from using forward error correction (FEC) in IPsec VPNs are true? (Choose two.)
A. FEC transmits the original payload in full to recover the error in transmission.
B. FEC reduces the stress on the remote device buffer to reconstruct packet loss.
C. FEC transmits additional packets as redundant data to the remote device.
D. FEC improves reliability, which overcomes adverse WAN conditions such as noisy links.
Refer to the exhibit.
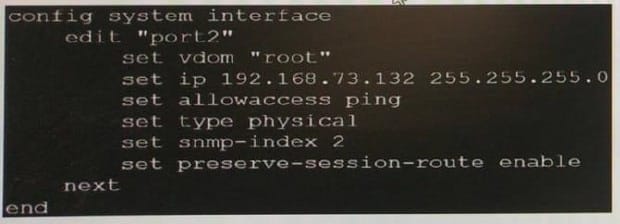
Based on the exhibit, which two actions does FortiGate perform on traffic passing through the SD-WAN member port2? (Choose two.)
A. FortiGate performs routing lookups for new sessions only after a route change.
B. FortiGate marks the routing information on existing sessions as persistent.
C. FortiGate flushes all routing information from the session table after a route change.
D. FortiGate always blocks all traffic after a route change.