NSE7_PBC-6.4 Online Practice Questions and Answers
When configuring the FortiCASB policy, which three configuration options are available? (Choose three.)
A. Intrusion prevention policies
B. Threat protection policies
C. Data loss prevention policies
D. Compliance policies
E. Antivirus policies
You have been tasked with deploying FortiGate VMs in a highly available topology on the Amazon Web
Services (AWS) cloud. The requirements for your deployment are as follows:
You must deploy two FortiGate VMs in a single virtual private cloud (VPC), with an external elastic load
balancer which will distribute ingress traffic from the internet to both FortiGate VMs in an active-active
topology.
Each FortiGate VM must have two elastic network interfaces: one will connect to a public subnet and other
will connect to a private subnet.
To maintain high availability, you must deploy the FortiGate VMs in two different availability zones.
How many public and private subnets will you need to configure within the VPC?
A. One public subnet and two private subnets
B. Two public subnets and one private subnet
C. Two public subnets and two private subnets
D. One public subnet and one private subnet
You are deploying Amazon Web Services (AWS) GuardDuty to monitor malicious or unauthorized behaviors related to AWS resources. You will also use the Fortinet aws-lambda-guardduty script to translate feeds from AWS GuardDuty findings into a list of malicious IP addresses. FortiGate can then consume this list as an external threat feed.
Which Amazon AWS services must you subscribe to in order to use this feature?
A. GuardDuty, CloudWatch, S3, Inspector, WAF, and Shield.
B. GuardDuty, CloudWatch, S3, and DynamoDB.
C. Inspector, Shield, GuardDuty, S3, and DynamoDB.
D. WAF, Shield, GuardDuty, S3, and DynamoDB.
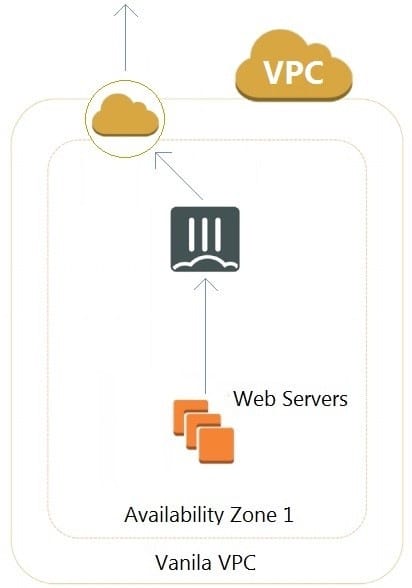
Refer to the exhibit. A customer has deployed an environment in Amazon Web Services (AWS) and is now trying to send outbound traffic from the Web servers to the Internet. The FortiGate policies are configured to allow all outbound traffic; however, the traffic is not reaching the FortiGate internal interface.
What are two possible reasons for this behavior? (Choose two.)
A. The web servers are not configured with the default gateway.
B. The Internet gateway (IGW) is not added to VPC (virtual private cloud).
C. AWS source and destination checks are enabled on the FortiGate interfaces.
D. AWS security groups may be blocking the traffic.
What is the bandwidth limitation of an Amazon Web Services (AWS) transit gateway VPC attachment?
A. Up to 1.25 Gbps per attachment
B. Up to 50 Gbps per attachment
C. Up to 10 Gbps per attachment
D. Up to 1 Gbps per attachment
You have been asked to secure your organization's salesforce application that is running on Microsoft Azure, and find an effective method for inspecting shadow IT activities in the organization. After an initial investigation, you find that many users access the salesforce application remotely as well as on-premises. Your goal is to find a way to get more visibility, control over shadow IT-related activities, and identify any data leaks in the salesforce application.
Which three steps should you take to achieve your goal? (Choose three.)
A. Deploy and configure FortiCASB with a Fortinet FortiCASB subscription license.
B. Configure FortiCASB and set up access rights, privileges, and data protection policies.
C. Use FortiGate, FortiGuard, and FortiAnalyzer solutions.
D. Deploy and configure FortiCWP with a workload guardian license.
E. Deploy and configure FortiGate with Security Fabric solutions, and FortiCWP with a storage guardian advance license.
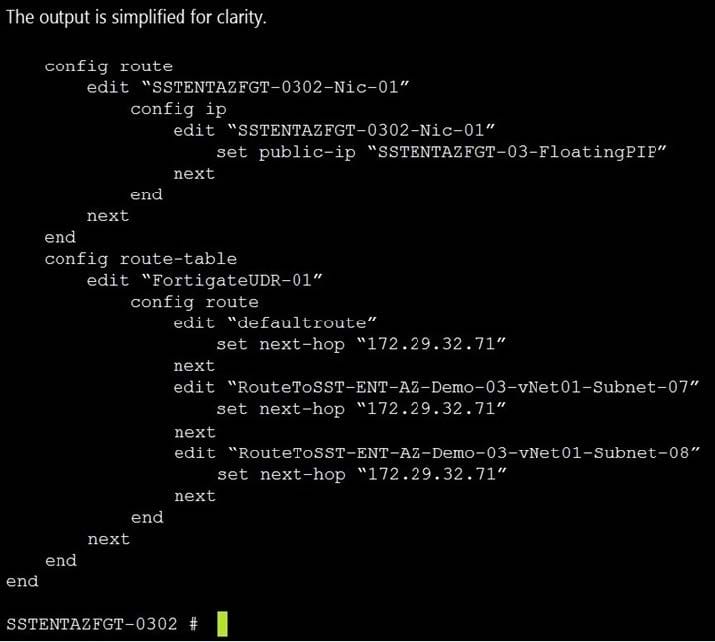
Refer to the exhibit. Consider an active-passive HA deployment in Microsoft Azure. The exhibit shows an excerpt from the passive FortiGate-VM node.
If the active FortiGate-VM fails, what are the results of the API calls made by the FortiGate named SSTENTAZFGT-0302? (Choose two.)
A. SSTENTAZFGT-03-FloatingPIP is assigned to the IP configuration with the name SSTENTAZFGT0302-Nic-01, under the network interface SSTENTAZFGT-0302-Nic-01
B. 172.29.32.71 is set as a next hop IP for all routes under FortigateUDR-01
C. The network interface of the active unit moves to itself
D. SSTENTAZFGT-03-FloatingPIP public IP is assigned to NIC SSTENTAZFGT-0302-Nic-01
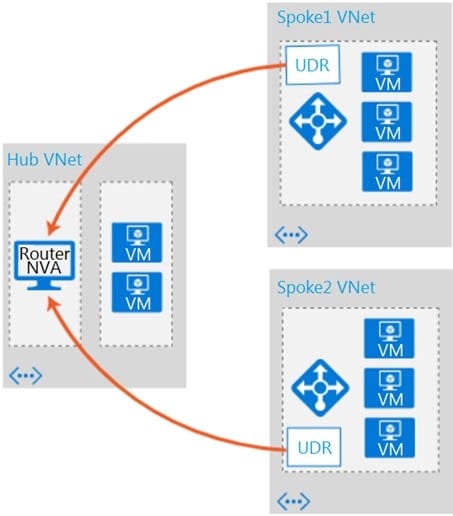
Refer to the exhibit. Which two conditions will enable you to segregate and secure the traffic between the hub and the spokes in Microsoft Azure? (Choose two.)
A. Implement the FortiGate-VM network virtual appliance (NVA) in the hub and use user-defined routes (UDRs) in the spokes.
B. Use ExpressRoute to interconnect the hub VNets and spoke VNets.
C. Configure VNet peering between the spokes only.
D. Configure VNet peering between the hub and spokes.
Which statement about FortiSandbox in Amazon Web Services (AWS) is true?
A. In AWS, virtual machines (VMs) that inspect files do not have to be reset after inspecting a file.
B. FortiSandbox in AWS uses Windows virtual machines (VMs) to inspect files.
C. In AWS, virtual machines (VMs) that inspect files are constantly up and running.
D. FortiSandbox in AWS can have a maximum of eight virtual machines (VMs) that inspect files.
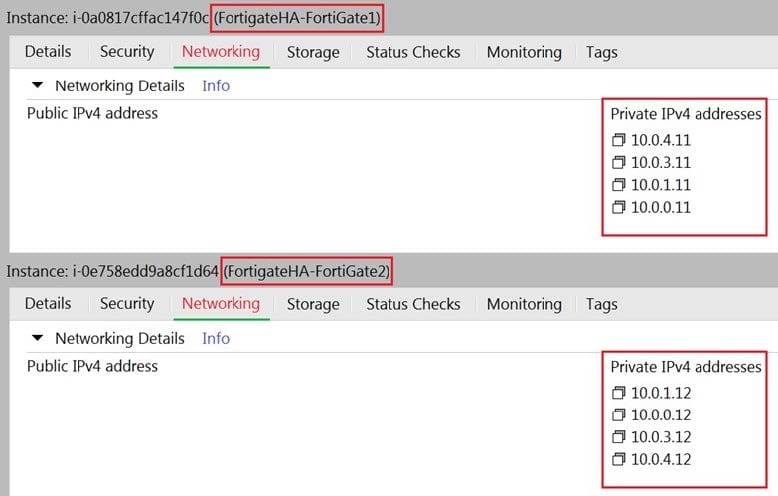
Refer to the exhibit. You are configuring an active-passive FortiGate clustering protocol (FGCP) HA configuration in a single availability zone in Amazon Web Services (AWS), using a cloud formation template.
After deploying the template, you notice that the AWS console has IP information listed in the FortiGate VM firewalls in the HA configuration. However, within the configuration of FortiOS, you notice that port1 is using an IP of 10.0.0.13, and port2 is using an IP of 10.0.1.13.
What should you do to correct this issue?
A. Configure FortiOS to use static IP addresses with the IP addresses reflected in the ENI primary IP address configuration (as per the exhibit).
B. Delete the deployment and start again. You have in put the wrong parameters during the cloud formation template deployment.
C. Configure FortiOS to use DHCP so that it will get the correct IP addresses on the ports.
D. Nothing, in AWS cloud, it is normal for a FortiGate ENI primary IP address to be different than the FortiOS IP address configuration.