NSE7_ATP-2.5 Online Practice Questions and Answers
Examine the FortiGate antivirus logs shown in the exhibit, than answer the following question:
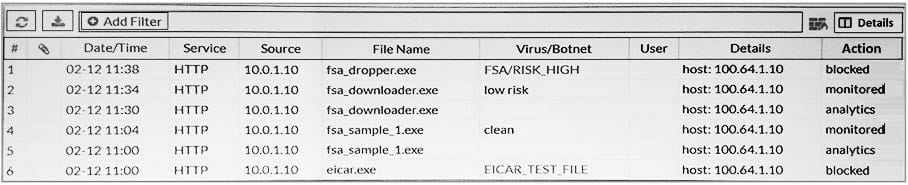
Based on the logs shown, which of the following statements is correct? (Choose two.)
A. The fsa_dropper.exe file was blocked using a local black list entry.
B. The fsa_sample_1.exe file was not sent to FortiSandbox.
C. The eicar.exe file was blocked using a FortiGiard generated signature.
D. The fsa_downloader.exe file was not blocked by FortiGate.
At which stage of the kill chain will an attacker use tools, such as nmap, ARIN, and banner grabbing, on the targeted organization's network?
A. Exploitation
B. Reconnaissance
C. Lateral movement
D. Weaponization
Examine the Suspicious Indicators section of the scan job shown in the exhibit, then answer the following question:

Which FortiSandbox component identified the vulnerability exploits?
A. VM scan
B. Antivirus scan
C. Static analysis
D. Cache check
Which of the following advanced threat protection are capable of preventing patient-zero infections? (Choose two.)
A. FortiWeb and FortiSandbox
B. FortiClient and FortiSandbox
C. FortiMail and FortiSandbox
D. FortiGate and FortiSandbox
FortiSandbox generates structured threat information exchange (STIX) packages for which of the following threats? (Choose two.)
A. Botnet connections
B. Malware
C. Intrusion attempts
D. Malicious URLs
Which FortiSandbox diagnostic command should you use to diagnose Internet connectivity issues on port3?
A. ping
B. tcpdump
C. test-network
D. traceroute
Examine the CLI configuration, than answer the following question:
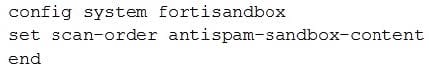
Which of the following statements is true regarding this FortiMail's inspection behavior?
A. Malicious URLs will be removed by antispam and replaced with a message.
B. Suspicious files not detected by antivirus will be inspected by FortiSandbox.
C. Known malicious URLs will be inspected by FortiSandbox.
D. Files are skipped by content profile will be inspected by FortiSandbox.
Which FortiWeb feature supports file submission to FortiSandbox?
A. Attack signature
B. Credential stuffing defense
C. IP reputation
D. File security
Examine the virtual Simulator section of the scan job report shown in the exhibit, then answer the following question:

Based on the behavior observed by the virtual simulator, which of the following statements is the most likely scenario?
A. The file contained a malicious image file.
B. The file contained malicious JavaScript.
C. The file contained a malicious macro.
D. The file contained a malicious URL.
Examine the scan job report shown in the exhibit, then answer the following question: Which of the following statements are true regarding this verdict? (Choose two.)
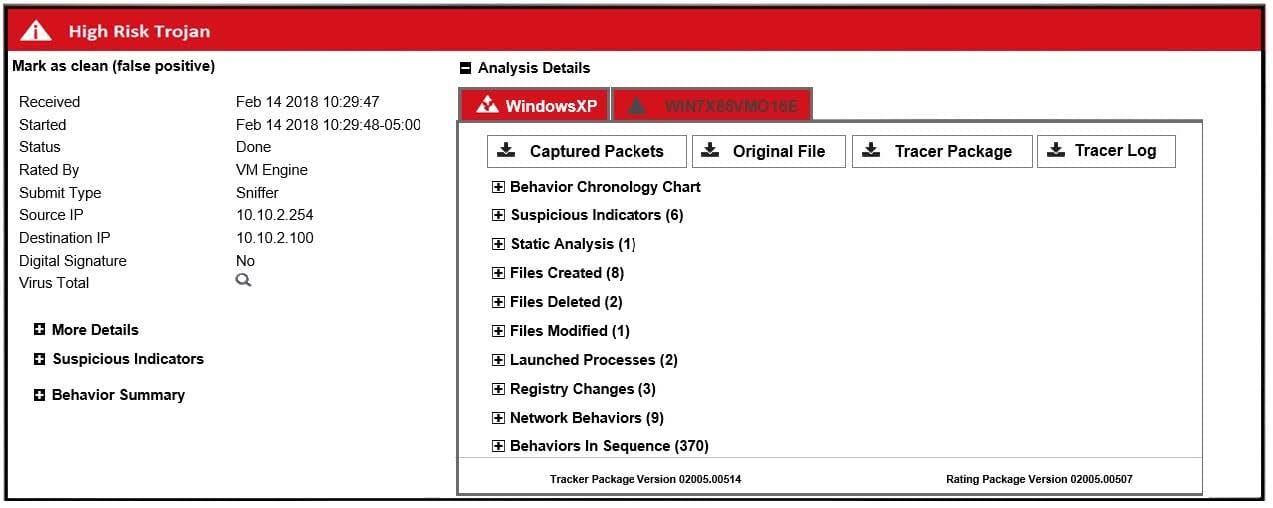
A. The file contained malicious JavaScipt.
B. The file contained a malicious macro.
C. The file was sandboxed in two-guest VMs.
D. The file was extracted using sniffer-mode inspection.