NSE7 Online Practice Questions and Answers
Examine the following partial outputs from two routing debug commands; then answer the question below.
# get router info kernel
tab=254 vf=0 scope=0type=1 proto=11 prio=0 0.0.0.0/0.0.0.0/0->0.0.0.0/0 pref=0.0.0.0
gwy=10.200.1.254 dev=2(port1)
tab=254 vf=0 scope=0type=1 proto=11 prio=10 0.0.0.0/0.0.0.0/0->0.0.0.0/0 pref=0.0.0.0
gwy=10.200.2.254 dev=3(port2)
tab=254 vf=0 scope=253type=1 proto=2 prio=0 0.0.0.0/0.0.0.0/.->10.0.1.0/24 pref=10.0.1.254
gwy=0.0.0.0 dev=4(port3)
# get router info routing-table all s*0.0.0.0/0 [10/0] via 10.200.1.254, portl [10/0] via 10.200.2.254, port2,
[10/0] dO.0.1.0/24 is directly connected, port3 dO.200.1.0/24 is directly connected, portl d0.200.2.0/24 is
directly connected, port2 Which outbound interface or interfaces will be used by this FortiGate to route web traffic from internal users to the Internet?
A. port!
B. port2.
C. Both portl and port2.
D. port3.
What conditions are required for two FortiGate devices to form an OSPF adjacency? (Choose three.)
A. IP addresses are in the same subnet.
B. Hello and dead intervals match.
C. OSPF IP MTUs match.
D. OSPF peer IDs match.
E. OSPF costs match.
Which of the following statements are correct regarding application layer test commands? (Choose two.)
A. They are used to filter real-time debugs.
B. They display real-time application debugs.
C. Some of them display statistics and configuration information about a feature or process.
D. Some of them can be used to restart an application.
When using the SSL certificate inspection method for HTTPS traffic, how does FortiGate filter web requests when the browser client does not provide the server name indication (SNI)?
A. FortiGate uses the Issued To: field in the server's certificate.
B. FortiGate switches to the full SSL inspection method to decrypt the data.
C. FortiGate blocks the request without any further inspection.
D. FortiGate uses the requested URL from the user's web browser.
View the following FortiGate configuration.
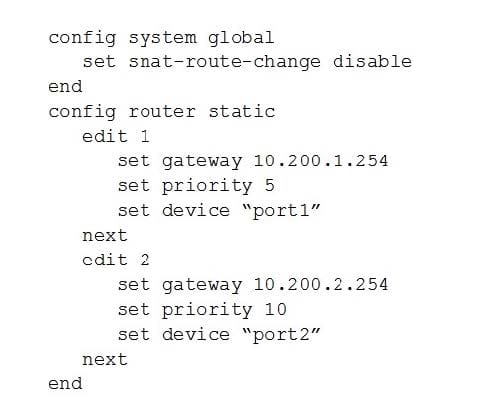
All traffic to the Internet currently egresses from port1. The exhibit shows partial session information for Internet traffic from a user on the internal network:
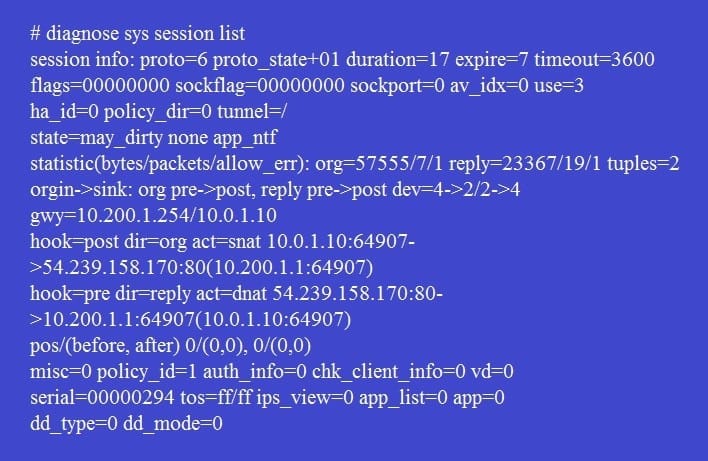
If the priority on route ID 1 were changed from 5 to 20, what would happen to traffic matching that user's session?
A. The session would remain in the session table, and its traffic would still egress from port1.
B. The session would remain in the session table, but its traffic would now egress from both port1 and port2.
C. The session would remain in the session table, and its traffic would start to egress from port2.
D. The session would be deleted, so the client would need to start a new session.
In which of the following states is a given session categorized as ephemeral? (Choose two.)
A. A TCP session waiting to complete the three-way handshake.
B. A TCP session waiting for FIN ACK.
C. A UDP session with packets sent and received.
D. A UDP session with only one packet received.
View the exhibit, which contains the output of a debug command, and then answer the question below.
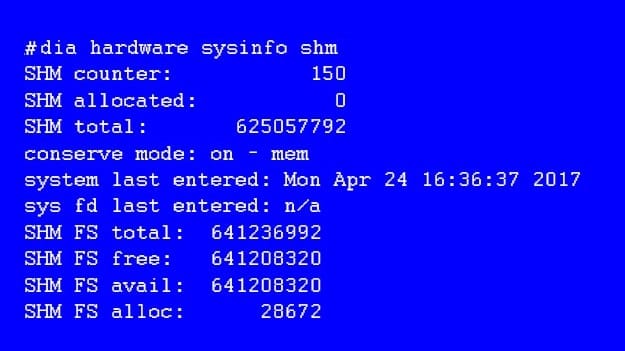
What statement is correct about this FortiGate?
A. It is currently in system conserve mode because of high CPU usage.
B. It is currently in FD conserve mode.
C. It is currently in kernel conserve mode because of high memory usage.
D. It is currently in system conserve mode because of high memory usage.
View the exhibit, which contains a partial web filter profile configuration, and then answer the question
below.
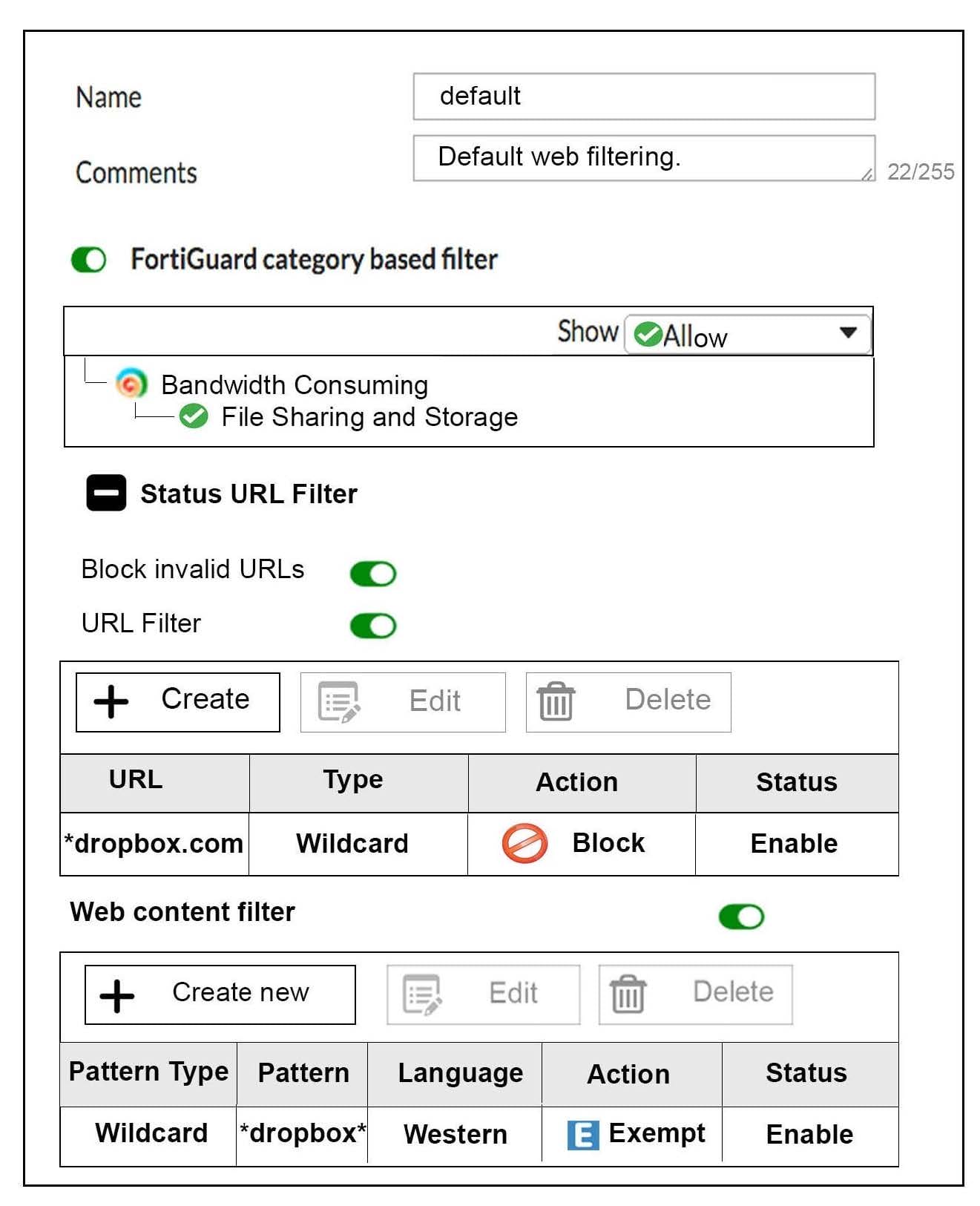
Which action will FortiGate take if a user attempts to access www.dropbox.com, which is categorized as File Sharing and Storage?
A. FortiGate will exempt the connection based on the Web Content Filter configuration.
B. FortiGate will block the connection based on the URL Filter configuration.
C. FortiGate will allow the connection based on the FortiGuard category based filter configuration.
D. FortiGate will block the connection as an invalid URL.
A corporate network allows Internet Access to FSSO users only. The FSSO user student does not have Internet access after successfully logged into the Windows AD network. The output of the `diagnose debug authd fsso list' command does not show student as an active FSSO user. Other FSSO users can access the Internet without problems. What should the administrator check? (Choose two.)
A. The user student must not be listed in the CA's ignore user list.
B. The user student must belong to one or more of the monitored user groups.
C. The student workstation's IP subnet must be listed in the CA's trusted list.
D. At least one of the student's user groups must be allowed by a FortiGate firewall policy.
A FortiGate is configured as an explicit web proxy. Clients using this web proxy are reposting DNS errors when accessing any website. The administrator executes the following debug commands and observes that the n-dns-timeout counter is increasing:

What should the administrator check to fix the problem?
A. The connectivity between the FortiGate unit and the DNS server.
B. The connectivity between the client workstations and the DNS server.
C. That DNS traffic from client workstations is allowed by the explicit web proxy policies.
D. That DNS service is enabled in the explicit web proxy interface.