NSE6_FWF-6.4 Online Practice Questions and Answers
When configuring Auto TX Power control on an AP radio, which two statements best describe how the radio responds? (Choose two.)
A. When the AP detects any other wireless signal stronger that -70 dBm, it will reduce its transmission power until it reaches the minimum configured TX power limit.
B. When the AP detects PF Interference from an unknown source such as a cordless phone with a signal stronger that -70 dBm, it will increase its transmission power until it reaches the maximum configured TX power limit.
C. When the AP detects any wireless client signal weaker than -70 dBm, it will reduce its transmission power until it reaches the maximum configured TX power limit.
D. When the AP detects any interference from a trusted neighboring AP stronger that -70 dBm, it will reduce its transmission power until it reaches the minimum configured TX power limit.
Refer to the exhibits. Exhibit A.
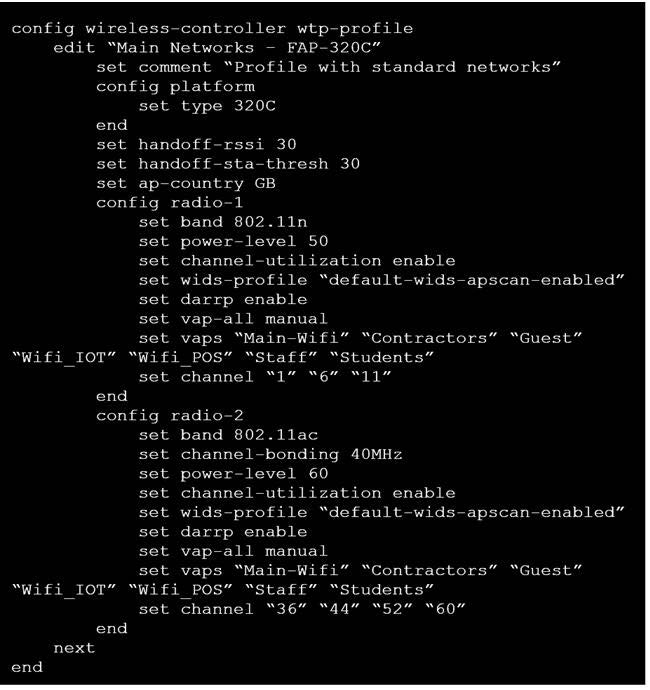
Exhibit B.
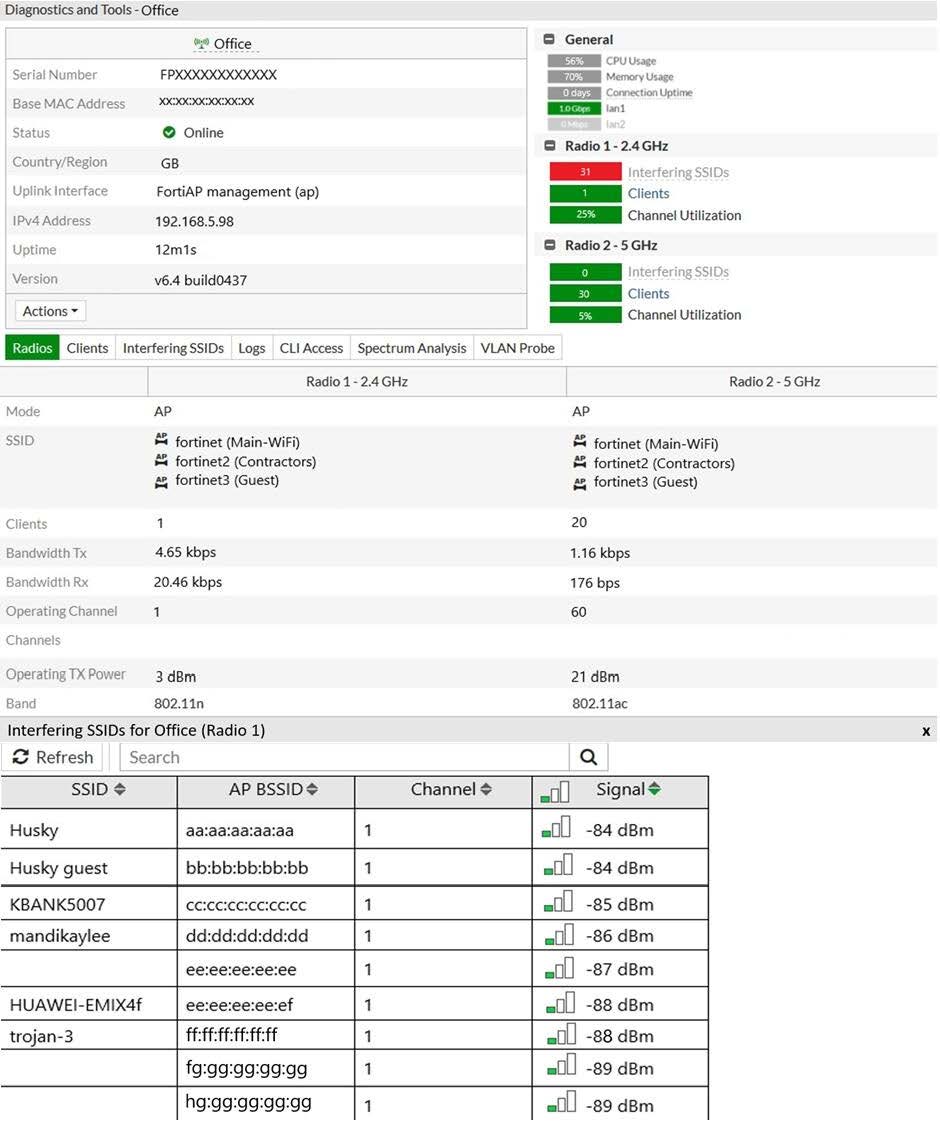
Exhibit C.
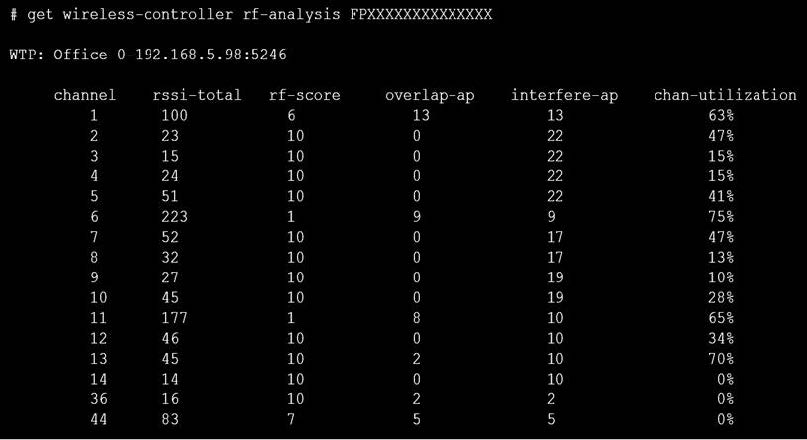
A wireless network has been installed in a small office building and is being used by a business to connect its wireless clients. The network is used for multiple purposes, including corporate access, guest access, and connecting point-of-sale and IoТ devices.
Users connecting to the guest network located in the reception area are reporting slow performance. The network administrator is reviewing the information shown in the exhibits as part of the ongoing investigation of the problem. They show the profile used for the AP and the controller RF analysis output together with a screenshot of the GUI showing a summary of the AP and its neighboring APs.
To improve performance for the users connecting to the guest network in this area, which configuration change is most likely to improve performance?
A. Increase the transmission power of the AP radios
B. Enable frequency handoff on the AP to band steer clients
C. Reduce the number of wireless networks being broadcast by the AP
D. Install another AP in the reception area to improve available bandwidth
Which two configurations are compatible for Wireless Single Sign-On (WSSO)? (Choose two.)
A. A VAP configured for captive portal authentication
B. A VAP configured for WPA2 or 3 Enterprise
C. A VAP configured to authenticate locally on FortiGate
D. A VAP configured to authenticate using a radius server
Where in the controller interface can you find a wireless client's upstream and downstream link rates?
A. On the AP CLI, using the cw_diag ksta command
B. On the controller CLI, using the diag wireless-controller wlac -d sta command
C. On the AP CLI, using the cw_diag -d sta command
D. On the controller CLI, using the WiFi Client monitor
Which administrative access method must be enabled on a FortiGate interface to allow APs to connect and function?
A. Security Fabric
B. SSH
C. HTTPS
D. FortiTelemetry
Which statement describes FortiPresence location map functionality?
A. Provides real-time insight into user movements
B. Provides real-time insight into user online activity
C. Provides real-time insight into user purchase activity
D. Provides real-time insight into user usage stats
Which of the following is a requirement to generate analytic reports using on-site FortiPresence deployment?
A. SQL services must be running
B. Two wireless APs must be sending data
C. DTLS encryption on wireless traffic must be turned off
D. Wireless network security must be set to open
As a network administrator, you are responsible for managing an enterprise secure wireless LAN. The controller is based in the United States, and you have been asked to deploy a number of managed APs in a remote office in Germany. What is the correct way to ensure that the RF channels and transmission power limits are appropriately configured for the remote APs?
A. Configure the APs individually by overriding the settings in Managed FortiAPs
B. Configure the controller for the correct country code for Germany
C. Clone a suitable FortiAP profile and change the county code settings on the profile
D. Create a new FortiAP profile and change the county code settings on the profile
When deploying a wireless network that is authenticated using EAP PEAP, which two configurations are required? (Choose two.)
A. An X.509 certificate to authenticate the client
B. An X.509 to authenticate the authentication server
C. A WPA2 or WPA3 personal wireless network
D. A WPA2 or WPA3 Enterprise wireless network
Which statement is correct about security profiles on FortiAP devices?
A. Security profiles on FortiAP devices can use FortiGate subscription to inspect the traffic
B. Only bridge mode SSIDs can apply the security profiles
C. Disable DTLS on FortiAP
D. FortiGate performs inspection the wireless traffic