NSE6_FWB-6.4 Online Practice Questions and Answers
Which statement about local user accounts is true?
A. They are best suited for large environments with many users.
B. They cannot be used for site publishing.
C. They must be assigned, regardless of any other authentication.
D. They can be used for SSO.
How does FortiWeb protect against defacement attacks?
A. It keeps a complete backup of all files and the database.
B. It keeps hashes of files and periodically compares them to the server.
C. It keeps full copies of all files and directories.
D. It keeps a live duplicate of the database.
Which two statements about the anti-defacement feature on FortiWeb are true? (Choose two.)
A. Anti-defacement can redirect users to a backup web server, if it detects a change.
B. Anti-defacement downloads a copy of your website to RAM, in order to restore a clean image, if it detects defacement.
C. FortiWeb will only check to see if there are changes on the web server; it will not download the whole file each time.
D. Anti-defacement does not make a backup copy of your databases.
What must you do with your FortiWeb logs to ensure PCI DSS compliance?
A. Store in an off-site location
B. Erase them every two weeks
C. Enable masking of sensitive data
D. Compress them into a .zip file format
Refer to the exhibit.
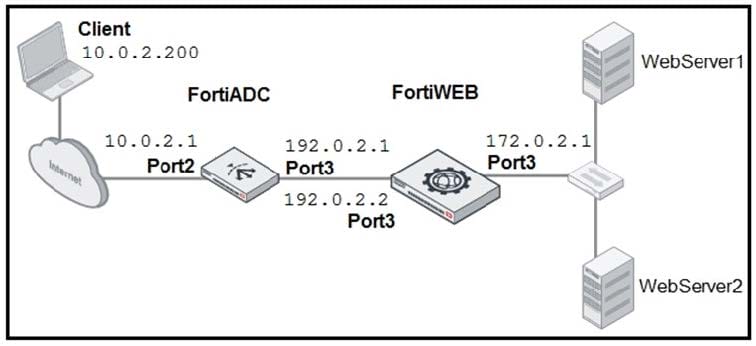
FortiADC is applying SNAT to all inbound traffic going to the servers. When an attack occurs, FortiWeb blocks traffic based on the 192.0.2.1 source IP address, which belongs to FortiADC. The setup is breaking all connectivity and genuine clients are not able to access the servers.
What must the administrator do to avoid this problem? (Choose two.)
A. Enable the Use X-Forwarded-For setting on FortiWeb.
B. No Special configuration is required; connectivity will be re-established after the set timeout.
C. Place FortiWeb in front of FortiADC.
D. Enable the Add X-Forwarded-For setting on FortiWeb.
Which operation mode does not require additional configuration in order to allow FTP traffic to your web server?
A. Offline Protection
B. Transparent Inspection
C. True Transparent Proxy
D. Reverse-Proxy
A client is trying to start a session from a page that should normally be accessible only after they have logged in.
When a start page rule detects the invalid session access, what can FortiWeb do? (Choose three.)
A. Reply with a "403 Forbidden" HTTP error
B. Allow the page access, but log the violation
C. Automatically redirect the client to the login page
D. Display an access policy message, then allow the client to continue, redirecting them to their requested page
E. Prompt the client to authenticate
What is one of the key benefits of the FortiGuard IP reputation feature?
A. It maintains a list of private IP addresses.
B. It provides a document of IP addresses that are suspect, so that administrators can manually update their blacklists.
C. It is updated once per year.
D. It maintains a list of public IPs with a bad reputation for participating in attacks.
In which operation mode(s) can FortiWeb modify HTTP packets? (Choose two.)
A. Transparent Inspection
B. Offline protection
C. True transparent proxy
D. Reverse proxy
How does offloading compression to FortiWeb benefit your network?
A. free up resources on the database server
B. Free up resources on the web server
C. reduces file size on the client's storage
D. free up resources on the FortiGate