NSE6_FWB-6.1 Online Practice Questions and Answers
When generating a protection configuration from an auto learning report what critical step must you do before generating the final protection configuration?
A. Restart the FortiWeb to clear the caches
B. Drill down in the report to correct any false positives.
C. Activate the report to create t profile
D. Take the FortiWeb offline to apply the profile
How does an ADOM differ from a VDOM?
A. ADOMs do not have virtual networking
B. ADOMs improve performance by offloading some functions.
C. ADOMs only affect specific functions, and do not provide full separation like VDOMs do.
D. Allows you to have 1 administrator for multiple tenants
A client is trying to start a session from a page that should normally be accessible only after they have
logged in.
When a start page rule detects the invalid session access, what can FortiWeb do? (Choose three.)
A. Reply with a "403 Forbidden" HTTP error
B. Allow the page access, but log the violation
C. Automatically redirect the client to the login page
D. Display an access policy message, then allow the client to continue, redirecting them to their requested page
E. Prompt the client to authenticate
Which of the following is true about Local User Accounts?
A. Must be assigned regardless of any other authentication
B. Can be used for Single Sign On
C. Can be used for site publishing
D. Best suited for large environments with many users
What other consideration must you take into account when configuring Defacement protection A. Use FortiWeb to block SQL Injections and keep regular backups of the Database
B. Also incorporate a FortiADC into your network
C. None. FortiWeb completely secures the site against defacement attacks
D. Configure the FortiGate to perform Anti-Defacement as well
Under what circumstances would you want to use the temporary uncompress feature of FortiWeb?
A. In the case of compression being done on the FortiWeb, to inspect the content of the compressed file
B. In the case of the file being a .MP3 music file
C. In the case of compression being done on the web server, to inspect the content of the compressed file.
D. In the case of the file being an .MP4 video
You are deploying FortiWeb 6.0 in an Amazon Web Services cloud. Which 2 lines of this initial setup via CLI are incorrect? (Choose two.)
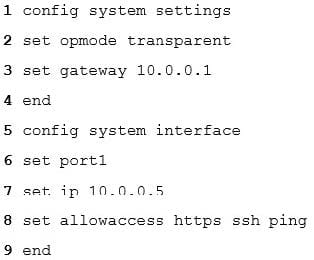
A. 6
B. 9
C. 3
D. 2
When integrating FortiWeb and FortiAnalyzer, why is the selection for FortiWeb Version critical? (Choose two)
A. Defines Log file format
B. Defines communication protocol
C. Defines Database Schema
D. Defines Log storage location
Which operation mode does not require additional configuration in order to allow FTP traffic to your web server?
A. Offline Protection
B. Transparent Inspection
C. True Transparent Proxy
D. Reverse-Proxy
Under which circumstances does FortiWeb use its own certificates? (Choose Two)
A. Secondary HTTPS connection to server where FortiWeb acts as a client
B. HTTPS to clients
C. HTTPS access to GUI
D. HTTPS to FortiGate