NSE6_FML-6.0 Online Practice Questions and Answers
Examine the FortiMail recipient-based policy shown in the exhibit; then answer the question below.
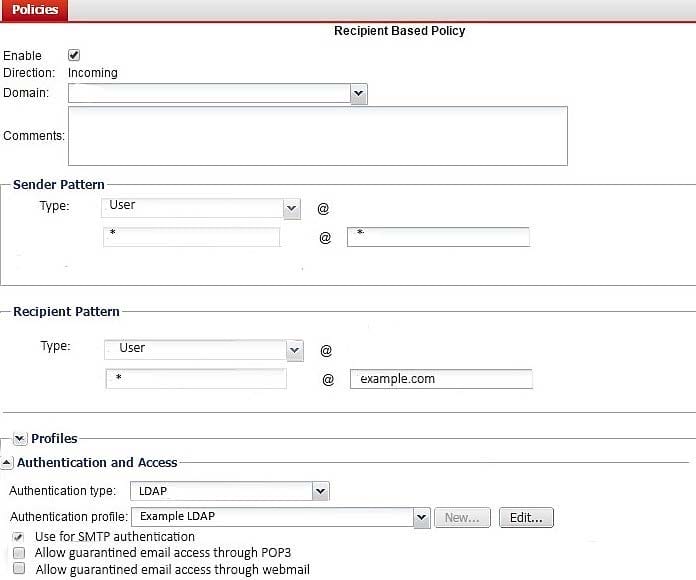
After creating the policy, an administrator discovered that clients are able to send unauthenticated email using SMTP. What must be done to ensure clients cannot send unauthenticated email?
A. Configure a matching IP policy with SMTP authentication and exclusive flag enabled
B. Move the recipient policy to the top of the list
C. Configure an access receive rule to verify authentication status
D. Configure an access delivery rule to enforce authentication
FortiMail is configured with the protected domain "example.com". Identify which of the following envelope addresses will require an access receive rule to relay for unauthenticated senders? (Choose two.)
A. MAIL FROM: [email protected] RCPT TO: [email protected]
B. MAIL FROM: [email protected] RCPT TO: [email protected]
C. MAIL FROM: [email protected] RCPT TO: [email protected]
D. MAIL FROM: [email protected] RCPT TO: [email protected]
Examine the FortMail mail server settings shown in the exhibit; then answer the question below.
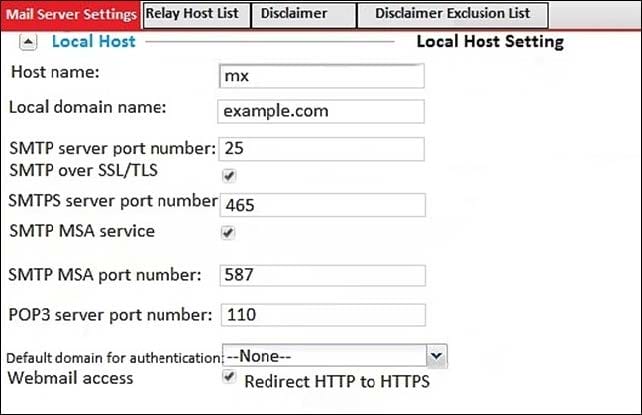
Which of the following statements are true? (Choose two.)
A. mx.example.com will enforce SMTPS on all outbound sessions
B. mx.example.com will display STARTTLS as one of the supported commands in SMTP sessions
C. mx.example.com will accept SMTPS connections
D. mx.example.com will drop any inbound plaintext SMTP connection
Examine the FortiMail active-passive cluster shown in the exhibit; then answer the question below.
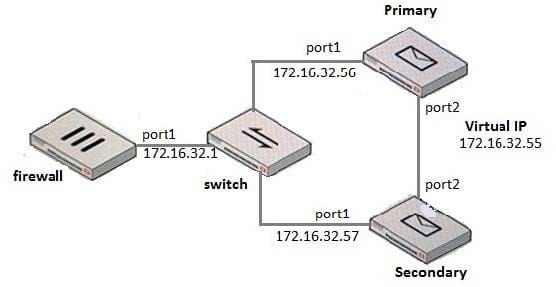
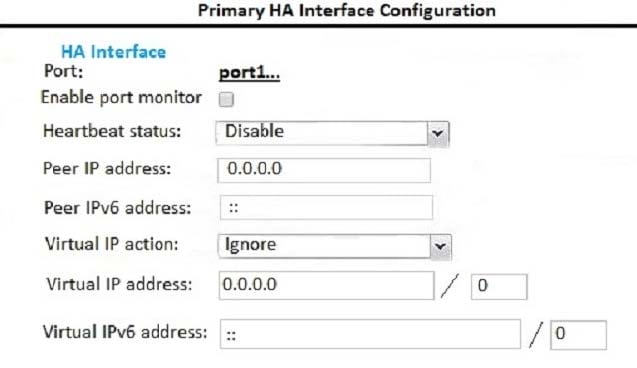
Which of the following parameters are recommended for the Primary FortiMail's HA interface configuration? (Choose three.)
A. Enable port monitor: disable
B. Peer IP address: 172.16.32.57
C. Heartbeat status: Primary
D. Virtual IP address: 172.16.32.55/24
E. Virtual IP action: Use
Which of the following CLI commands, if executed, will erase all data on the log disk partition? (Choose two.)
A. execute formatmaildisk
B. execute formatmaildisk_backup
C. execute formatlogdisk
D. execute partitionlogdisk 40
Examine the FortiMail IBE users shown in the exhibit; then answer the question below Which one of the following statements describes the Pre-registered status of the IBE user [email protected]?
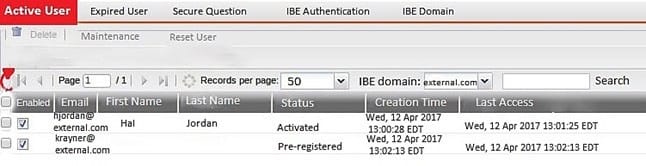
A. The user was registered by an administrator in anticipation of IBE participation
B. The user has completed the IBE registration process but has not yet accessed their IBE email
C. The user has received an IBE notification email, but has not accessed the HTTPS URL or attachment yet
D. The user account has been de-activated, and the user must register again the next time they receive an IBE email
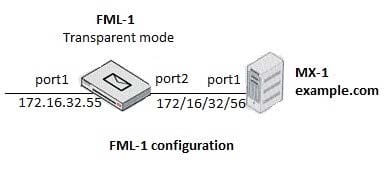
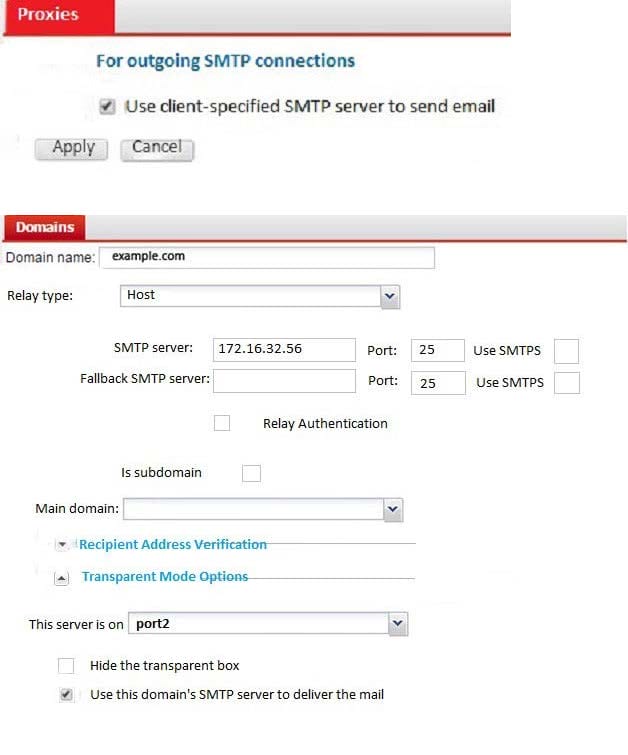
Which of the following statements are true regarding the transparent mode FortiMail's email routing for the example.com domain? (Choose two.)
A. FML-1 will use the built-in MTA for outgoing sessions
B. FML-1 will use the transparent proxy for incoming sessions
C. If incoming email are undeliverable, FML-1 can queue them to retry again later
D. If outgoing email messages are undeliverable, FML-1 can queue them to retry later
A FortiMail is configured with the protected domain "example.com". For this FortiMail, which of the following envelope addresses are considered incoming? (Choose two.)
A. MAIL FROM: [email protected] RCPT TO: [email protected]
B. MAIL FROM: [email protected] PCPT TO: [email protected]
C. MAIL FROM: [email protected] RCPT TO: [email protected]
D. MAIL FROM: [email protected] RCPT TO: [email protected]
Examine the FortiMail topology and IP-based policy shown in the exhibit; then answer the question below.
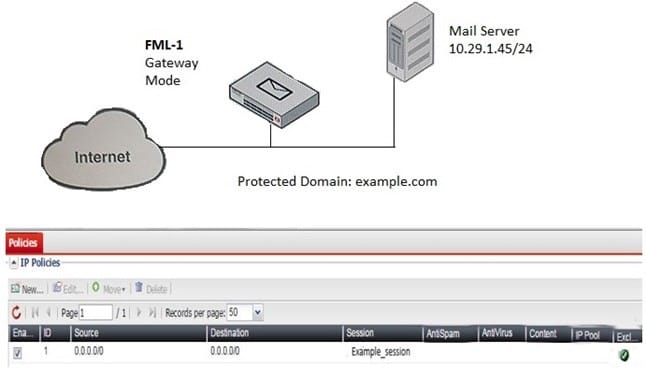
An administrator has enabled the sender reputation feature in the Example_Session profile on FML-1. After a few hours, the deferred queue on the Mail Server started filing up with undeliverable email. What changes should the administrator make to fix this issue? (Choose two.)
A. Clear the sender reputation database using the CLI
B. Create an outbound recipient policy to bypass outbound email from session profile inspections
C. Disable the exclusive flag in IP policy ID 1
D. Apply a session profile with sender reputation disabled on a separate IP policy for outbound sessions
While reviewing logs, an administrator discovered that an incoming email was processed using policy IDs:
0:4:9.
Which of the following statements are true? (Choose two.)
A.
FortiMail applied the default behavior for relaying inbound email
B.
FortiMail configuration is missing an access delivery rule to process incoming email
C.
Incoming recipient policy ID 9 has the exclusive flag set
D.
Email was processed using IP policy ID 4