NSE5_FCT-7.0 Online Practice Questions and Answers
A FortiClient EMS administrator has enabled the compliance rule for the sales department. Which Fortinet device will enforce compliance with dynamic access control?
A. FortiClient
B. FortiClient EMS
C. FortiGate
D. FortiAnalyzer
Refer to the exhibit.
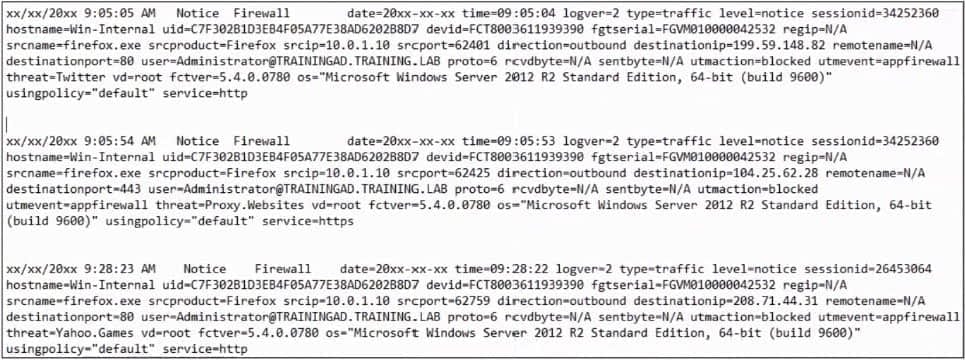
Based on the FortiClient logs shown in the exhibit, which software application is blocked by the application firewall?
A. Twitter
B. Facebook
C. Internet Explorer
D. Firefox
An administrator is required to maintain a software vulnerability on the endpoints, without showing the feature on the FortiClient dashboard. What must the administrator do to achieve this requirement?
A. Disable select the vulnerability scan feature in the deployment package
B. Use the default endpoint profile
C. Select the vulnerability scan feature in the deployment package, but disable the feature on the endpoint profile
D. Click the hide icon on the vulnerability scan tab
Which two benefits are benefits of using multi-tenancy mode on FortiClient EMS? (Choose two.)
A. The fabric connector must use an IP address to connect to FortiClient EMS
B. It provides granular access and segmentation.
C. Licenses are shared among sites.
D. Separate host servers manage each site.
Refer to the exhibit, which shows the endpoint summary information on FortiClient EMS.
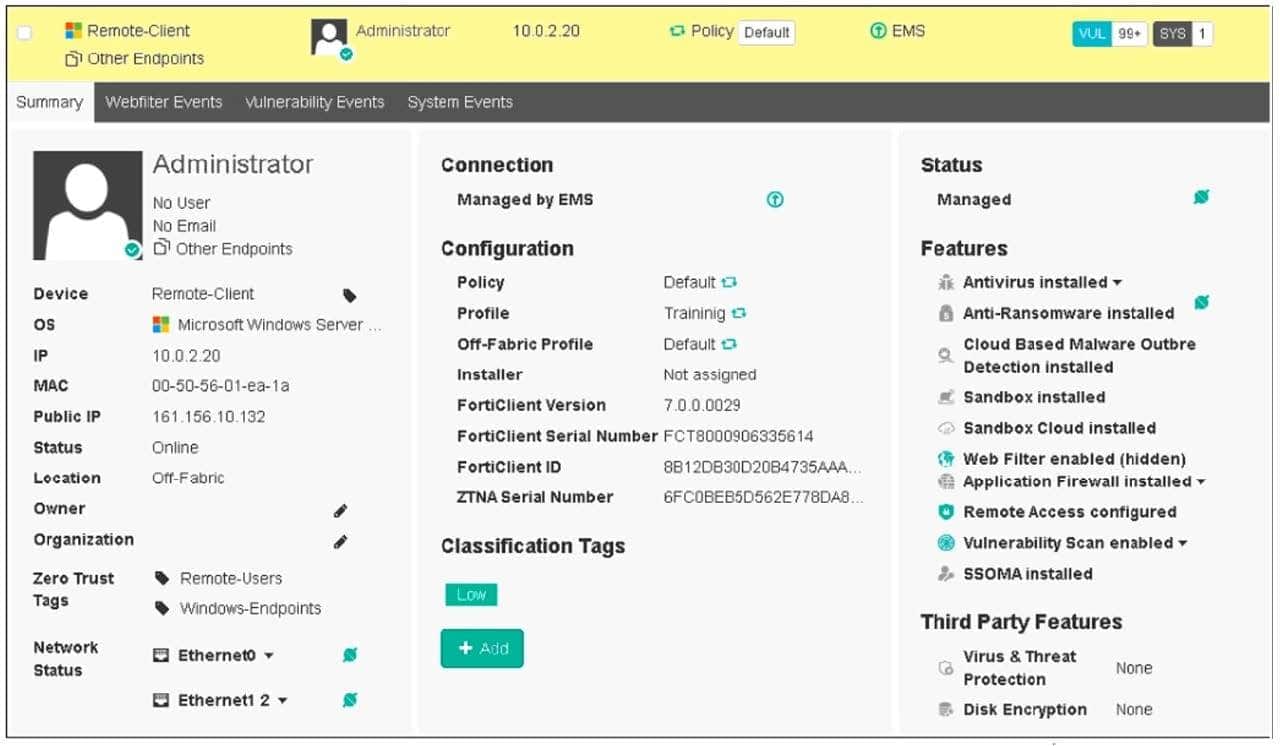
What two conclusions can you make based on the Remote-Client status shown above? (Choose two.)
A. The endpoint is classified as at risk.
B. The endpoint has been assigned the Default endpoint policy.
C. The endpoint is configured to support FortiSandbox.
D. The endpoint is currently off-net.
Which component or device shares ZTNA tag information through Security Fabric integration?
A. FortiGate
B. FortiGate Access Proxy
C. FortiClient
D. FortiClient EMS
Refer to the exhibit.
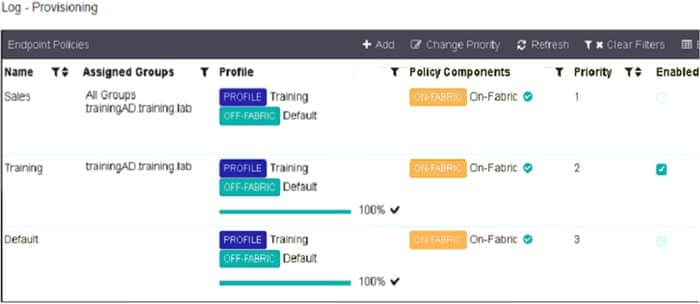
Which shows multiple endpoint policies on FortiClient EMS.
Which policy is applied to the endpoint in the AD group trainingAD?
A. The Sales policy
B. The Training policy
C. Both the Sales and Training policies because their priority is higher than the Default policy
D. The Default policy because it has the highest priority
Refer to the exhibit, which shows the Zero Trust Tagging Rule Set configuration.

Which two statements about the rule set are true? (Choose two.)
A. The endpoint must satisfy that only Windows 10 is running.
B. The endpoint must satisfy that only AV software is installed and running.
C. The endpoint must satisfy that antivirus is installed and running and Windows 10 is running.
D. The endpoint must satisfy that only Windows Server 2012 R2 is running.
Which two statements are true about ZTNA? (Choose two.)
A. ZTNA provides role-based access
B. ZTNA manages access for remote users only
C. ZTNA manages access through the client only
D. ZTNA provides a security posture check
Refer to the exhibit.
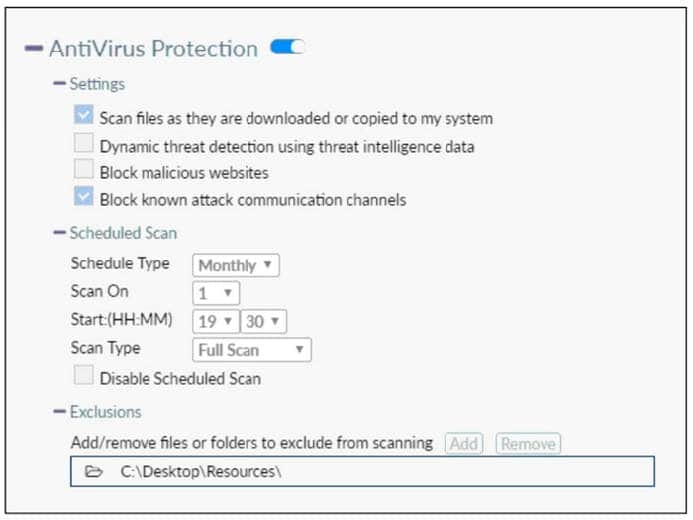
Based on the settings shown in the exhibit which statement about FortiClient behavior is true?
A. FortiClient quarantines infected files and reviews later, after scanning them.
B. FortiClient blocks and deletes infected files after scanning them.
C. FortiClient scans infected files when the user copies files to the Resources folder
D. FortiClient copies infected files to the Resources folder without scanning them.