NSE5_FCT-6.2 Online Practice Questions and Answers
Refer to the exhibit.
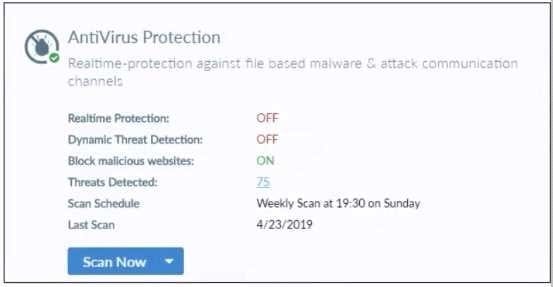
Based on the settings shown in the exhibit what action will FortiClient take when it detects that a user is trying to download an infected file?
A. Blocks the infected files as it is downloading
B. Quarantines the infected files and logs all access attempts
C. Sends the infected file to FortiGuard for analysis
D. Allows the infected file to download without scan
Refer to the exhibit.
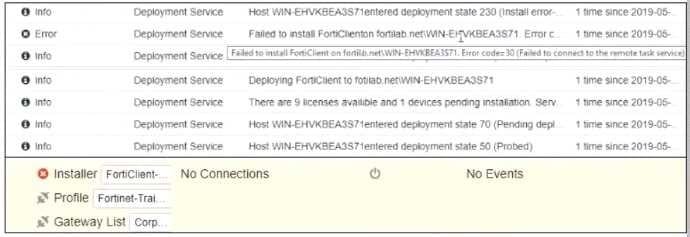
Based on the logs shown in the exhibit, why did FortiClient EMS fail to install FortiClient on the endpoint?
A. Windows firewall is not running
B. Windows installer service is not running
C. Remote registry service is not running
D. Task scheduler service is not running
Which statement about FortiClient comprehensive endpoint protection is true?
A. It helps to safeguard systems from email spam
B. It helps to safeguard systems from data loss.
C. It helps to safeguard systems from DDoS.
D. lt helps to safeguard systems from advanced security threats, such as malware.
A new chrome book is connected in a schools network
Which component can the EMS administrator use to manage the FortiClient web filter extension installed on the Google Chromebook endpoint?
A. FortiClient customer URL list
B. FortiClient web filter extension
C. FortiClient EMS
D. FortiClient site categories
Refer to the exhibit.
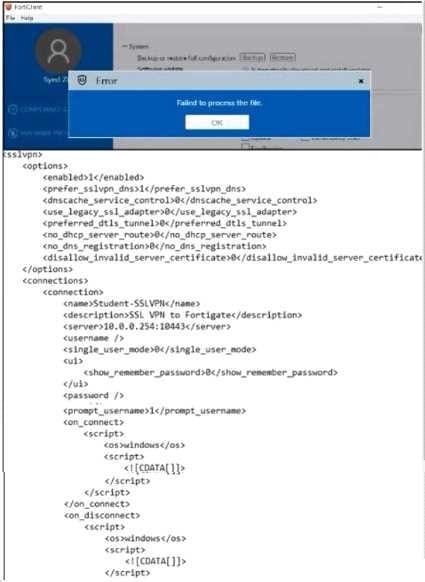
A. An administrator has restored the modified XML configuration file to FortiClient and sees the error shown in the exhibit
B. Based on the XML settings shown in the exhibit, what must the administrator do to resolve the issue with the XML configuration file?
C. The administrator must resolve the XML syntax error. The administrator must use a password to decrypt the file The administrator must change the file size
D. The administrator must save the file as FortiClient-config conf.
What does FortiClient do as a fabric agent? (Choose two )
A. Provides application inventory
B. Provides IOC verdicts
C. Automates Responses
D. Creates dynamic policies
What is the function of the quick scan option on FortiClient?
A. It performs a full system scan including all files, executable files, DLLs, and drivers for threats.
B. It scans executable files. DLLs, and drivers that are currently running, for threats.
C. It allows users to select a specific file folder on your local hard disk drive (HDD), to scan for threats
D. It scans programs and drivers that are currently running for threats
An administrator is required to maintain a software inventory on the endpoints. without showing the feature on the FortiClient dashboard What must the administrator do to achieve this requirement?
A. The administrator must use default endpoint profile
B. The administrator must not select the vulnerability scan feature in the deployment package.
C. The administrator must select the vulnerability scan feature in the deployment package, but disable the feature on the endpoint profile
D. The administrator must click the hide icon on the vulnerability scan tab
An administrator installs FortiClient on Windows Server. What is the default behavior of real-time protection control?
A. Real-time protection must update AV signature database
B. Real-time protection sends malicious files to FortiSandbox when the file is not detected locally
C. Real-time protection is disabled
D. Real-time protection must update the signature database from FortiSandbox
Which network component sends a notification after identifying a connected endpoint in the quarantine automation process?
A. FortiGate
B. FortiClient
C. FortiClient EMS
D. FortiAnalyzer