NSE5_EDR-5.0 Online Practice Questions and Answers
What is true about classifications assigned by Fortinet Cloud Sen/ice (FCS)?
A. The core is responsible for all classifications if FCS playbooks are disabled
B. The core only assigns a classification if FCS is not available
C. FCS revises the classification of the core based on its database
D. FCS is responsible for all classifications
What is the role of a collector in the communication control policy?
A. A collector blocks unsafe applications from running
B. A collector is used to change the reputation score of any application that collector runs
C. A collector records applications that communicate externally
D. A collector can quarantine unsafe applications from communicating
A company requires a global communication policy for a FortiEDR multi-tenant environment.
How can the administrator achieve this?
A. An administrator creates a new communication control policy and shares it with other organizations
B. A local administrator creates new a communication control policy and shares it with other organizations
C. A local administrator creates a new communication control policy and assigns it globally to all organizations
D. An administrator creates a new communication control policy for each organization
Exhibit.


Based on the forensics data shown in the exhibit which two statements are true? (Choose two.)
A. The device cannot be remediated
B. The event was blocked because the certificate is unsigned
C. Device C8092231196 has been isolated
D. The execution prevention policy has blocked this event.
An administrator needs to restrict access to the ADMINISTRATION tab in the central manager for a specific account. What role should the administrator assign to this account?
A. Admin
B. User
C. Local Admin
D. REST API
Refer to the exhibits.
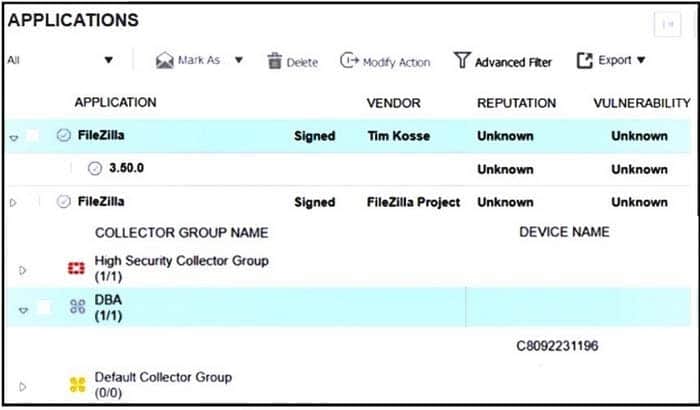
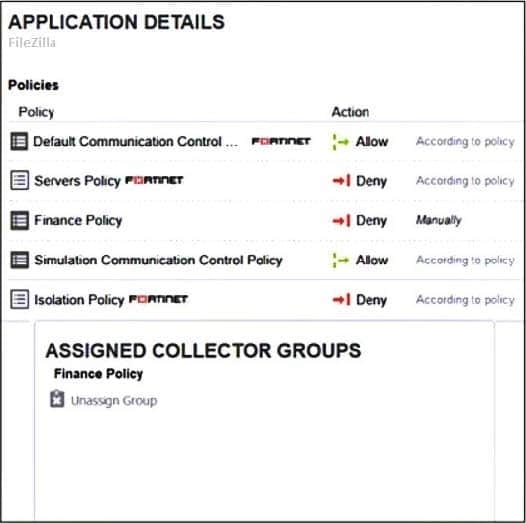
The exhibits show application policy logs and application details Collector C8092231196 is a member of the Finance group What must an administrator do to block the FileZilia application?
A. Deny application in Finance policy
B. Assign Finance policy to DBA group
C. Assign Finance policy to Default Collector Group
D. Assign Simulation Communication Control Policy to DBA group
Which two statements are true about the remediation function in the threat hunting module? (Choose two.)
A. The file is removed from the affected collectors
B. The threat hunting module sends the user a notification to delete the file
C. The file is quarantined
D. The threat hunting module deletes files from collectors that are currently online.
The FortiEDR axe classified an event as inconclusive, out a few seconds later FCS revised the classification to malicious.
What playbook actions ate applied to the event?
A. Playbook actions applied to inconclusive events
B. Playbook actions applied to handled events
C. Playbook actions applied to suspicious events
D. Playbook actions applied to malicious events
Which FortiEDR component must have JumpBox functionality to connect with FortiAnalyzer?
A. Collector
B. Core
C. Central manager
D. Aggregator
Which two events can trigger FortiEDR NGAV policy violations? (Choose two.)
A. When a malicious file attempts to communicate externally
B. When a malicious file is executed
C. When a malicious file is read
D. When a malicious file attempts to access data