NSE4_FGT-7.2 Online Practice Questions and Answers
Which three statements are true regarding session-based authentication? (Choose three.)
A. HTTP sessions are treated as a single user.
B. IP sessions from the same source IP address are treated as a single user.
C. It can differentiate among multiple clients behind the same source IP address.
D. It requires more resources.
E. It is not recommended if multiple users are behind the source NAT
An administrator has configured outgoing Interface any in a firewall policy. Which statement is true about the policy list view?
A. Policy lookup will be disabled.
B. By Sequence view will be disabled.
C. Search option will be disabled
D. Interface Pair view will be disabled.
Refer to the exhibit.
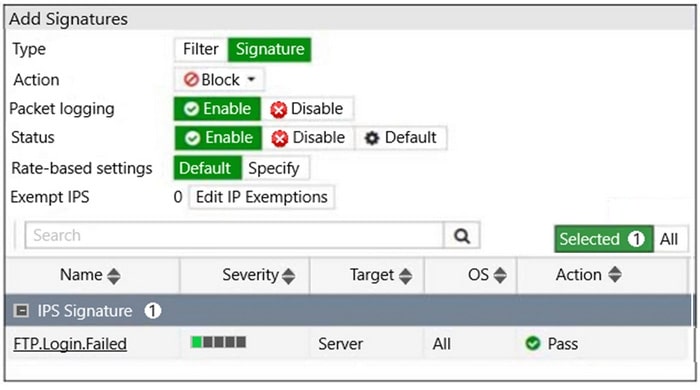
Review the Intrusion Prevention System (IPS) profile signature settings. Which statement is correct in adding the FTP.Login.Failed signature to the IPS sensor profile?
A. The signature setting uses a custom rating threshold.
B. The signature setting includes a group of other signatures.
C. Traffic matching the signature will be allowed and logged.
D. Traffic matching the signature will be silently dropped and logged.
Refer to the exhibits.
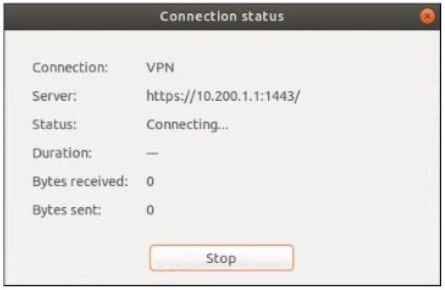
The SSL VPN connection fails when a user attempts to connect to it. What should the user do to successfully connect to SSL VPN?
A. Change the SSL VPN port on the client.
B. Change the Server IP address.
C. Change the idle-timeout.
D. Change the SSL VPN portal to the tunnel.
Which statement about the policy ID number of a firewall policy is true?
A. It is required to modify a firewall policy using the CLI.
B. It represents the number of objects used in the firewall policy.
C. It changes when firewall policies are reordered.
D. It defines the order in which rules are processed.
Which two attributes are required on a certificate so it can be used as a CA certificate on SSL Inspection? (Choose two.)
A. The keyUsage extension must be set to keyCertSign.
B. The common name on the subject field must use a wildcard name.
C. The issuer must be a public CA.
D. The CA extension must be set to TRUE.
View the exhibit.
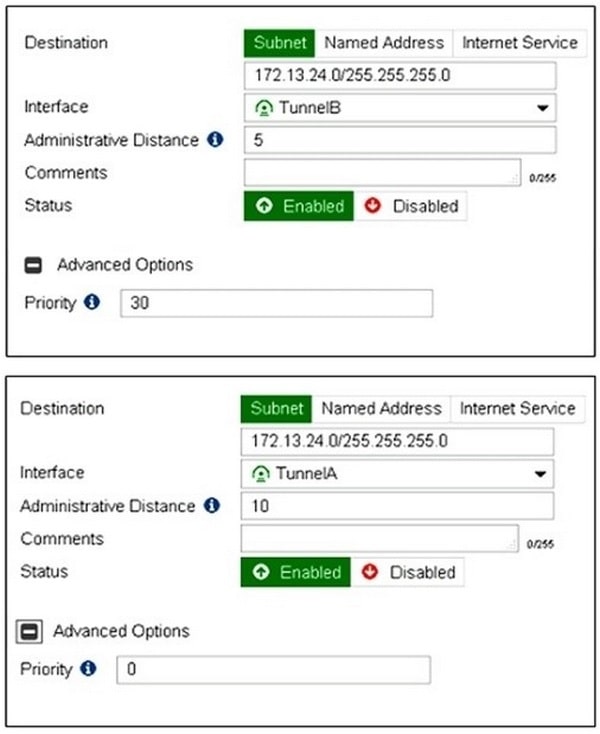
Which of the following statements are correct? (Choose two.)
A. This setup requires at least two firewall policies with the action set to IPsec.
B. Dead peer detection must be disabled to support this type of IPsec setup.
C. The TunnelB route is the primary route for reaching the remote site. The TunnelA route is used only if the TunnelB VPN is down.
D. This is a redundant IPsec setup.
Which two features of IPsec IKEv1 authentication are supported by FortiGate? (Choose two.)
A. Extended authentication (XAuth) for faster authentication because fewer packets are exchanged
B. Extended authentication (XAuth) to request the remote peer to provide a username and password
C. No certificate is required on the remote peer when you set the certificate signature as the authentication method
D. Pre-shared key and certificate signature as authentication methods
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
A. The collector agent uses a Windows API to query DCs for user logins.
B. NetAPI polling can increase bandwidth usage in large networks.
C. The collector agent must search security event logs.
D. The NetSession Enum function is used to track user logouts.
Which three authentication timeout types are availability for selection on FortiGate? (Choose three.)
A. hard-timeout
B. auth-on-demand
C. soft-timeout
D. new-session
E. Idle-timeout