NSE4_FGT-7.0 Online Practice Questions and Answers
Why does FortiGate Keep TCP sessions in the session table for several seconds, even after both sides (client and server) have terminated the session?
A. To allow for out-of-order packets that could arrive after the FIN/ACK packets
B. To finish any inspection operations
C. To remove the NAT operation
D. To generate logs
In which two ways can RPF checking be disabled? (Choose two )
A. Enable anti-replay in firewall policy.
B. Disable the RPF check at the FortiGate interface level for the source check
C. Enable asymmetric routing.
D. Disable strict-arc-check under system settings.
In an explicit proxy setup, where is the authentication method and database configured?
A. Proxy Policy
B. Authentication Rule
C. Firewall Policy
D. Authentication scheme
Refer to the exhibit.
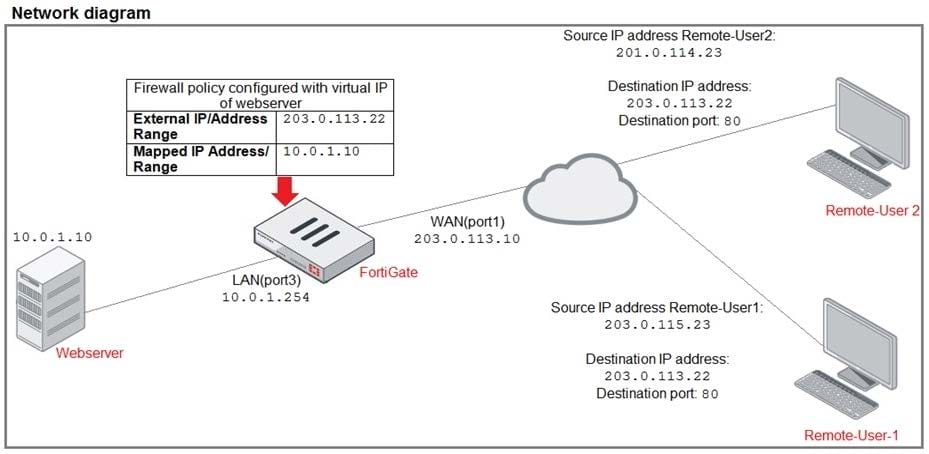
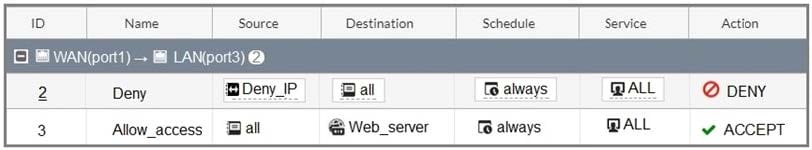
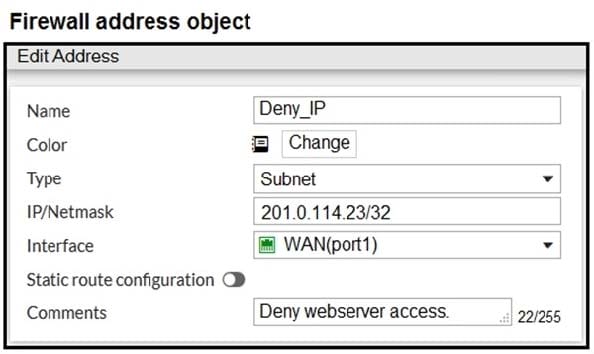
The exhibit contains a network diagram, firewall policies, and a firewall address object configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-user2. Remote-user2 is still able to access Webserver.
Which two changes can the administrator make to deny Webserver access for Remote- User2? (Choose two.)
A. Disable match-vip in the Deny policy.
B. Set the Destination address as Deny_IP in the Allow-access policy.
C. Enable match vip in the Deny policy.
D. Set the Destination address as Web_server in the Deny policy.
Which statements about the firmware upgrade process on an active-active HA cluster are true? (Choose two.)
A. The firmware image must be manually uploaded to each FortiGate.
B. Only secondary FortiGate devices are rebooted.
C. Uninterruptable upgrade is enabled by default.
D. Traffic load balancing is temporally disabled while upgrading the firmware.
Refer to the FortiGuard connection debug output.
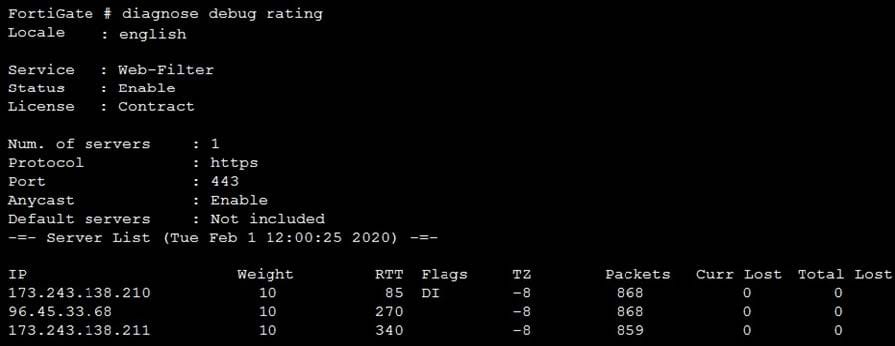
Based on the output shown in the exhibit, which two statements are correct? (Choose two.)
A. A local FortiManager is one of the servers FortiGate communicates with.
B. One server was contacted to retrieve the contract information.
C. There is at least one server that lost packets consecutively.
D. FortiGate is using default FortiGuard communication settings.
Which statement regarding the firewall policy authentication timeout is true?
A. It is an idle timeout. The FortiGate considers a user to be "idle" if it does not see any packets coming from the user's source IP.
B. It is a hard timeout. The FortiGate removes the temporary policy for a user's source IP address after this timer has expired.
C. It is an idle timeout. The FortiGate considers a user to be "idle" if it does not see any packets coming from the user's source MAC.
D. It is a hard timeout. The FortiGate removes the temporary policy for a user's source MAC address after this timer has expired.
Which security feature does FortiGate provide to protect servers located in the internal networks from attacks such as SQL injections?
A. Denial of Service
B. Web application firewall
C. Antivirus
D. Application control
Which two types of traffic are managed only by the management VDOM? (Choose two.)
A. FortiGuard web filter queries
B. PKI
C. Traffic shaping
D. DNS
Refer to the exhibit.
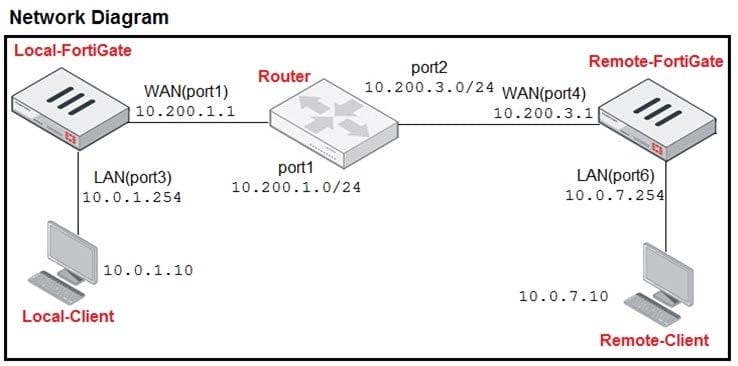
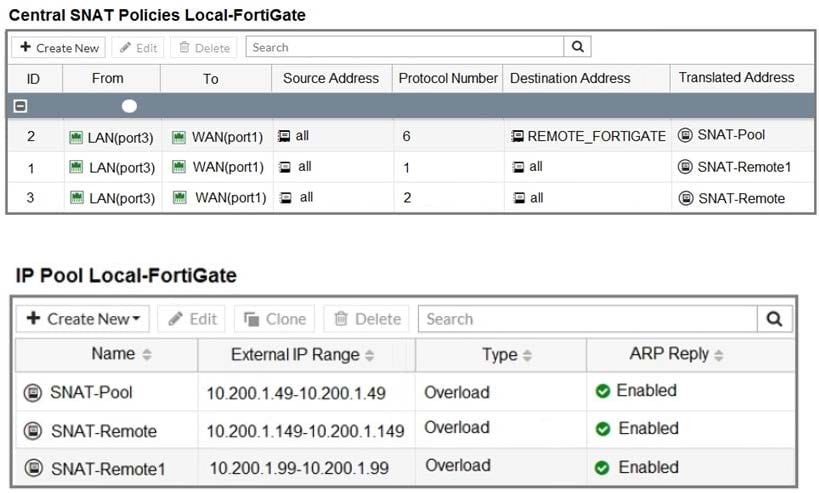
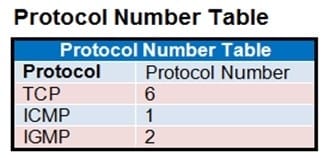
The exhibit contains a network diagram, central SNAT policy, and IP pool configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
A firewall policy is configured to allow to destinations from LAN (port3) to WAN (port1).
Central NAT is enabled, so NAT settings from matching Central SNAT policies will be applied.
Which IP address will be used to source NAT the traffic, if the user on Local-Client (10.0.1.10) pings the IP
address of Remote-FortiGate (10.200.3.1)?
A. 10.200.1.149
B. 10.200.1.1
C. 10.200.1.49
D. 10.200.1.99