NSE4_FGT-6.2 Online Practice Questions and Answers
An administrator wants to block HTTP uploads. Examine the exhibit, which contains the proxy address created for that purpose.
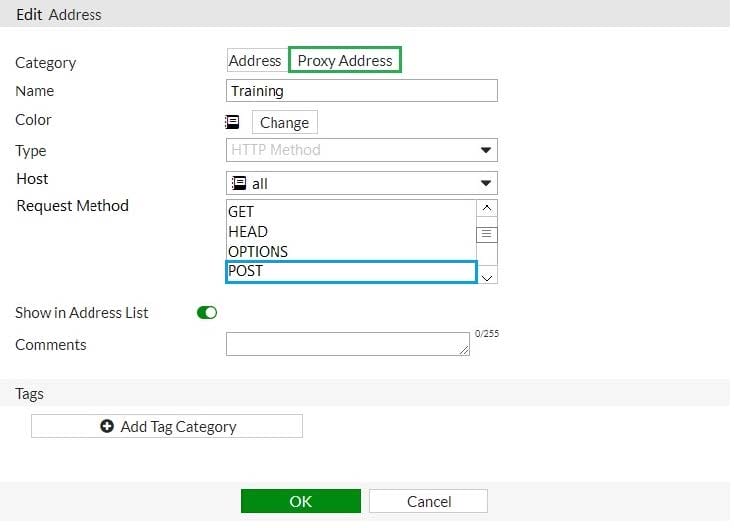
Where must the proxy address be used?
A. As the source in a firewall policy.
B. As the source in a proxy policy.
C. As the destination in a firewall policy.
D. As the destination in a proxy policy.
What FortiGate components are tested during the hardware test? (Choose three.)
A. Administrative access
B. HA heartbeat
C. CPU
D. Hard disk
E. Network interfaces
NGFW mode allows policy-based configuration for most inspection rules. Which security profile's configuration does not change when you enable policy-based inspection?
A. Web filtering
B. Antivirus
C. Web proxy
D. Application control
Which statements about HA for FortiGate devices are true? (Choose two.)
A. Sessions handled by proxy-based security profiles cannot be synchronized.
B. Virtual clustering can be configured between two FortiGate devices that have multiple VDOMs.
C. HA management interface settings are synchronized between cluster members.
D. Heartbeat interfaces are not required on the primary device.
An administrator is running the following sniffer command:
diagnose sniffer packet any "host 10.0.2.10" 3
What information will be included in the sniffer output? (Choose three.)
A. IP header
B. Ethernet header
C. Packet payload
D. Application header
E. Interface name
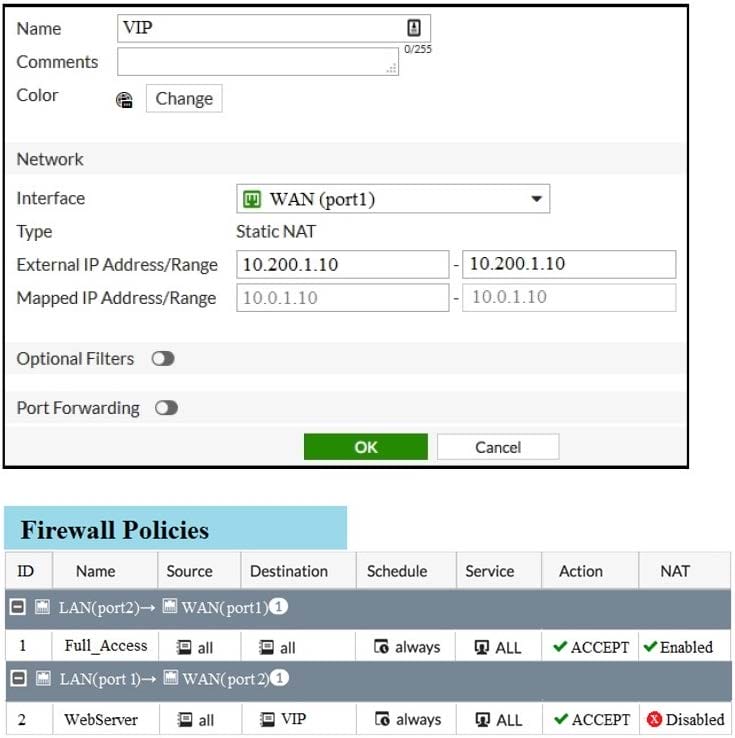
Examine the exhibit, which contains a virtual IP and firewall policy configuration.
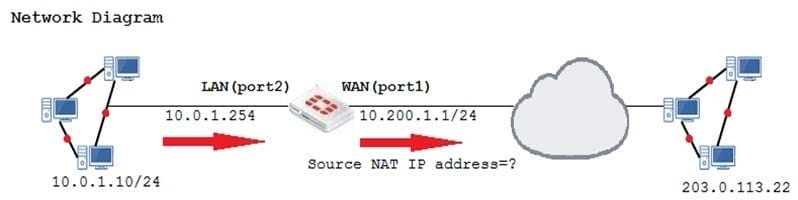
The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port2) interface has the IP address
10.0.1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is
configured with a VIP as the destination address.
Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP
address 10.0.1.10/24?
A. 10.200.1.10
B. Any available IP address in the WAN (port1) subnet 10.200.1.0/24
C. 10.200.1.1
D. 10.0.1.254
Examine this output from a debug flow: Which statements about the output are correct? (Choose two.)
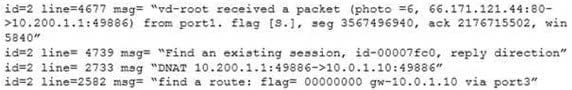
A. FortiGate received a TCP SYN/ACK packet.
B. The source IP address of the packet was translated to 10.0.1.10.
C. FortiGate routed the packet through port 3.
D. The packet was allowed by the firewall policy with the ID 00007fc0.
In a high availability (HA) cluster operating in active-active mode, which of the following correctly describes the path taken by the SYN packet of an HTTP session that is offloaded to a secondary FortiGate?
A. Client > primary FortiGate> secondary FortiGate> primary FortiGate> web server.
B. Client > secondary FortiGate> web server.
C. Clinet >secondary FortiGate> primary FortiGate> web server.
D. Client> primary FortiGate> secondary FortiGate> web server.
Which of the following are purposes of NAT traversal in IPsec? (Choose two.)
A. To detect intermediary NAT devices in the tunnel path.
B. To dynamically change phase 1 negotiation mode aggressive mode.
C. To encapsulation ESP packets in UDP packets using port 4500.
D. To force a new DH exchange with each phase 2 rekey.
Examine the network diagram shown in the exhibit, and then answer the following question:
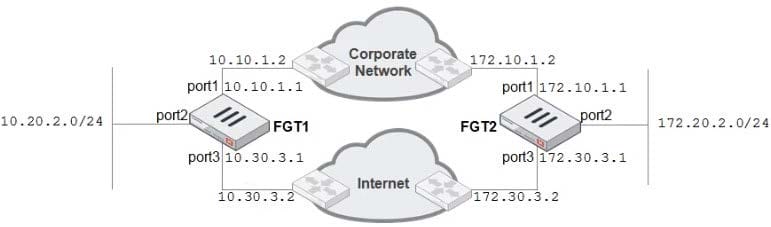
A firewall administrator must configure equal cost multipath (ECMP) routing on FGT1 to ensure both port1 and port3 links are used at the same time for all traffic destined for 172.20.2.0/24. Which of the following static routes will satisfy this requirement on FGT1? (Choose two.)
A. 172.20.2.0/24 (1/0) via 10.10.1.2, port1 [0/0]
B. 172.20.2.0/24 (25/0) via 10.30.3.2, port3 [5/0]
C. 172.20.2.0/24 (25/0) via 10.10.1.2, port1 [5/0]
D. 172.20.2.0/24 (1/150) via 10.30.3.2, port3 [10/0]