NSE4_FGT-6.0 Online Practice Questions and Answers
Which statement about FortiGuard services for FortiGate is true?
A. The web filtering database is downloaded locally on FortiGate.
B. Antivirus signatures are downloaded locally on FortiGate.
C. FortiGate downloads IPS updates using UDP port 53 or 8888.
D. FortiAnalyzer can be configured as a local FDN to provide antivirus and IPS updates.
What FortiGate components are tested during the hardware test? (Choose three.)
A. Administrative access
B. HA heartbeat
C. CPU
D. Hard disk
E. Network interfaces
Examine the exhibit, which shows the output of a web filtering real time debug.
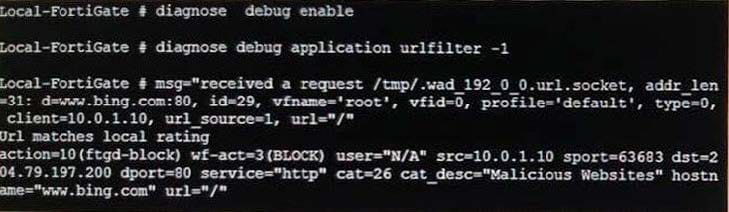
Why is the site www.bing.com being blocked?
A. The web site www.bing.com is categorized by FortiGuard as Malicious Websites.
B. The user has not authenticated with the FortiGate yet.
C. The web server IP address 204.79.197.200 is categorized by FortiGuard as Malicious Websites.
D. The rating for the web site www.bing.com has been locally overridden to a category that is being blocked.
Which of the following statements about the FSSO collector agent timers is true?
A. The workstation verify interval is used to periodically check if a workstation is still a domain member.
B. The IP address change verify interval monitors the server IP address where the collector agent is installed, and the updates the collector agent configuration if it changes.
C. The user group cache expiry is used to age out the monitored groups.
D. The dead entry timeout interval is used to age out entries with an unverified status.
Which of the following features is supported by web filter in flow-based inspection mode with NGFW mode set to profile-based?
A. FortiGuard Quotas
B. Static URL
C. Search engines
D. Rating option
In a high availability (HA) cluster operating in active-active mode, which of the following correctly describes the path taken by the SYN packet of an HTTP session that is offloaded to a secondary FortiGate?
A. Client > primary FortiGate> secondary FortiGate> primary FortiGate> web server.
B. Client > secondary FortiGate> web server.
C. Clinet >secondary FortiGate> primary FortiGate> web server.
D. Client> primary FortiGate> secondary FortiGate> web server.
An administrator has configured the following settings:
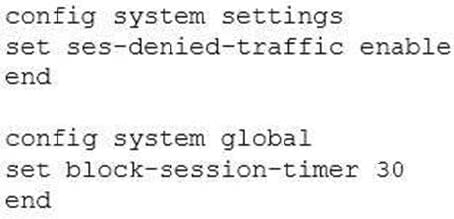
What does the configuration do? (Choose two.)
A. Reduces the amount of logs generated by denied traffic.
B. Enforces device detection on all interfaces for 30 minutes.
C. Blocks denied users for 30 minutes.
D. Creates a session for traffic being denied.
Which Statements about virtual domains (VDOMs) arc true? (Choose two.)
A. Transparent mode and NAT/Route mode VDOMs cannot be combined on the same FortiGate.
B. Each VDOM can be configured with different system hostnames.
C. Different VLAN sub-interface of the same physical interface can be assigned to different VDOMs.
D. Each VDOM has its own routing table.
When using WPAD DNS method, which FQDN format do browsers use to query the DNS server?
A. srv_proxy.
B. srv_tcp.wpad.
C. wpad.
D. proxy.
Which of the following statements about central NAT are true? (Choose two.)
A. IP tool references must be removed from existing firewall policies before enabling central NAT.
B. Central NAT can be enabled or disabled from the CLI only.
C. Source NAT, using central NAT does not require a central SNAT policy.
D. Destination NAT, using central NAT, requires a VIP object as the destination address in a firewall.