NSE4-5.4 Online Practice Questions and Answers
Which statement concerning IPS is false?
A. IPS packages contain an engine and signatures used by both IPS and other flow-based scans.
B. One-arm topology with sniffer mode improves performance of IPS blocking.
C. IPS can detect zero-day attacks.
D. The status of the last service update attempt from FortiGuard IPS is shown on System>Config>FortiGuard and in output from 'diag autoupdate version'
FortiGate units are preconfigured with four default protection profiles. These protection profiles are used to control the type of content inspection to be performed. What action must be taken for one of these profiles to become active?
A. The protection profile must be assigned to a firewall policy.
B. The "Use Protection Profile" option must be selected in the Web Config tool under the sections for AntiVirus, IPS, WebFilter, and AntiSpam.
C. The protection profile must be set as the Active Protection Profile.
D. All of the above.
Review to the network topology in the exhibit. The workstation, 172.16.1.1/24, connects to port2 of the FortiGate device, and the ISP router, 172.16.1.2, connects to port1. Without changing IP addressing, which configuration changes are required to properly forward users traffic to the Internet? (Choose two)
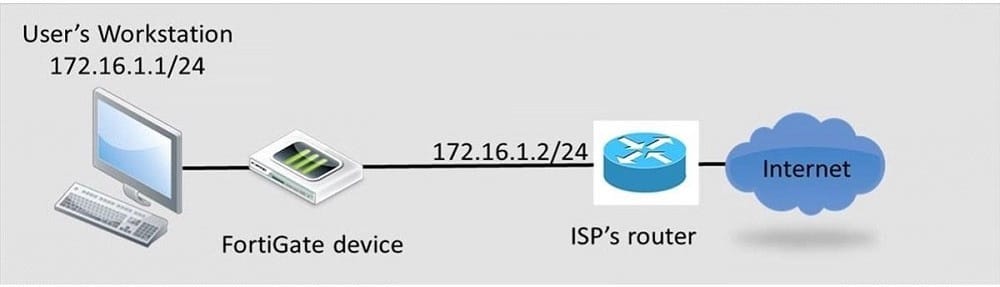
A. At least one firewall policy from port2 to port1 to allow outgoing traffic.
B. A default route configured in the FortiGuard devices pointing to the ISP's router.
C. Static or dynamic IP addresses in both ForitGate interfaces port1 and port2.
D. The FortiGate devices configured in transparent mode.
When firewall policy authentication is enabled, which protocols can trigger an authentication challenge? (Choose two.)
A. SMTP
B. POP3
C. HTTP
D. FTP
A FortiGate unit is configured to receive push updates from the FortiGuard Distribution Network, however, updates are not being received. Which of the following statements are possible reasons for this? (Select all that apply.)
A. The external facing interface of the FortiGate unit is configured to use DHCP.
B. The FortiGate unit has not been registered.
C. There is a NAT device between the FortiGate unit and the FortiGuard Distribution Network and no override push IP is configured.
D. The FortiGate unit is in Transparent mode which does not support push updates.
Which of the following antivirus and attack definition update features are supported by FortiGate units? (Select all that apply.)
A. Manual, user-initiated updates from the FortiGuard Distribution Network.
B. Hourly, daily, or weekly scheduled antivirus and attack definition and antivirus engine updates from the FortiGuard Distribution Network.
C. Push updates from the FortiGuard Distribution Network.
D. Update status including version numbers, expiry dates, and most recent update dates and times.
Which statements are correct regarding application control? (Choose two.)
A. It is based on the IPS engine.
B. It is based on the AV engine.
C. It can be applied to SSL encrypted traffic.
D. Application control cannot be applied to SSL encrypted traffic.
A FortiGate is operating in NAT/Route mode and configured with two virtual LAN (VLAN) sub- interfaces added to the same physical interface. Which one of the following statements is correct regarding the VLAN IDs in this scenario?
A. The two VLAN sub-interfaces can have the same VLAN ID only if they have IP addresses in different subnets.
B. The two VLAN sub-interfaces must have different VLAN IDs.
C. The two VLAN sub-interfaces can have the same VLAN ID only if they belong to different VDOMs.
D. The two VLAN sub-interfaces can have the same VLAN ID if they are connected to different L2 IEEE 802.1Q compliant switches.
Which component of FortiOS performs application control inspection?
A. Kernel
B. Antivirus engine
C. IPS engine
D. Application control engine
What FortiGate feature can be used to prevent a cross-site scripting (XSS) attack?
A. Web application firewall (WAF)
B. DoS policies
C. Rate based IPS signatures
D. One-arm sniffer