MS-101 Online Practice Questions and Answers
HOTSPOT
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
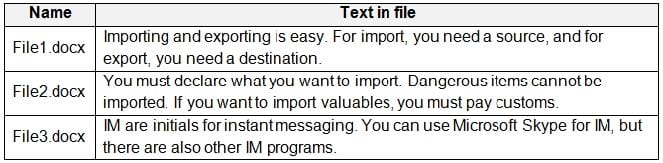
A user named User1 has files on a Windows 10 device as shown in the following table.
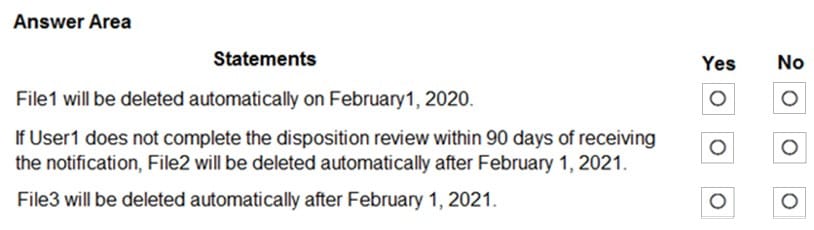
In Azure Information Protection, you create a label named Label1 that is configured to apply automatically. Label1 is configured as shown in the following exhibit.
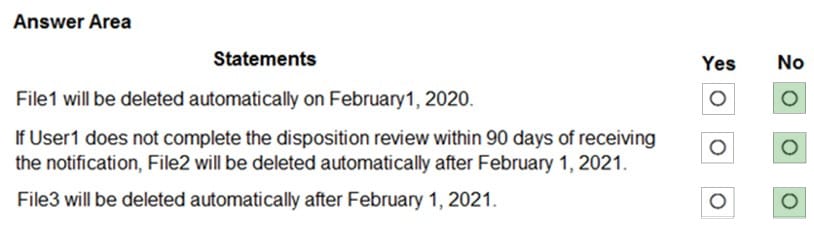
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
You have a Microsoft 365 subscription.
You need to create a data loss prevention (DLP) policy that is configured to use the Set headers action.
To which location can the policy be applied?
A. OneDrive accounts
B. Exchange email
C. Teams chat and channel messages
D. SharePoint sites
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Company users store documents using Dropbox Business, which they access Dropbox Business via the MyApps portal.
You want to make sure that Microsoft 365 identity is used to authenticate user access to Dropbox Business. Also, in the event that information is downloaded to an untrusted device, the information needs to be protected. Which of the following actions should you take via the Azure Active Directory admin center?
A. You should configure an app protection policy.
B. You should configure the device settings.
C. You should configure application proxy settings.
D. You should configure device configuration policy.
Your company has a Microsoft 365 subscription.
User email is stored in Microsoft Exchange Online.
You have been instructed to keep a copy of all email messages that includes a specific word in the mailbox of a specified user.
Which of the following actions should you take from the Security and Compliance admin center?
A. You should create a label and a label policy.
B. You should create a mail flow rule.
C. You should configure an in-place hold.
D. You should configure a retention policy.
Your company has recently acquired a Microsoft 365 subscription.
You have been tasked with logging all mailbox folder permission modifications a user who has a mailbox in Microsoft Exchange Online.
You are making use of the Set-Mailbox cmdlet.
Which of the following is the parameter you should use?
A. -AuditAdmin
B. -AuditDelegate
C. -AuditEnabled
D. -AuditLog
You have a Microsoft 365 tenant that contains two groups named Group1 and Group2.
You need to prevent the members or Group1 from communicating with the members of Group2 by using Microsoft Teams. The solution must comply with regulatory requirements and must not affect other user in the tenant.
What should you use?
A. information barriers
B. communication compliance policies
C. moderated distribution groups
D. administrator units in Azure Active Directory (Azure AD)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer that runs Windows 10.
You need to verify which version of Windows 10 is installed.
Solution: From the Settings app, you select System, and then you select About to view information about the system.
Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 E5 tenant that contains the devices shown in the following table.
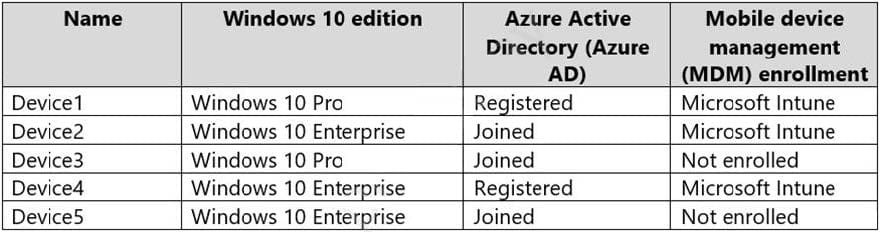
You add custom apps to the private store in Microsoft Store Business.
You plan to create a policy to show only the private store in Microsoft Store for Business.
To which devices can the policy be applied?
A. Device2 only
B. Device1 and Device3 only
C. Device1 and Device3 only
D. Device2, Device3, and Device5 only
E. Device1, Device2, Device3, Device4, and Device5
You have a Microsoft 365 tenant.
You plan to implement Endpoint Protection device configuration profiles.
Which platform can you manage by using the profiles?
A. Ubuntu Linux
B. macOS
C. iOS
D. Android
You have a Microsoft 365 tenant that contains two users named User1 and User2. You create the alert policy shown in the following exhibit.
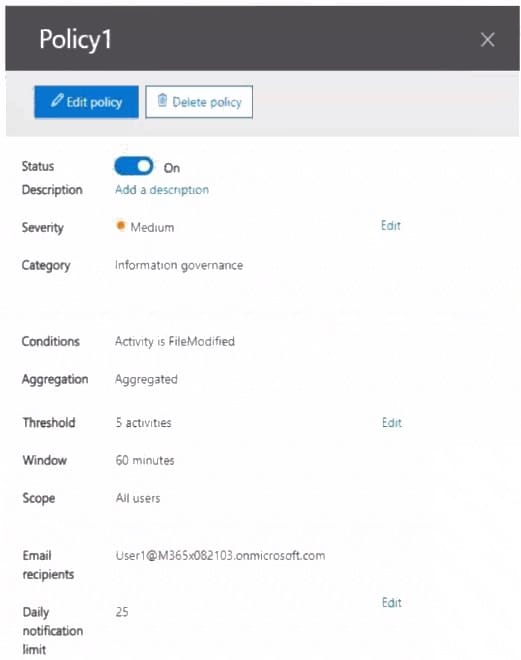
User2 runs a script that modifies a file in a Microsoft SharePoint Online library once every four minutes and runs for a period of two hours. How many alerts will User1 receive?
A. 2
B. 5
C. 10
D. 25