JN0-663 Online Practice Questions and Answers
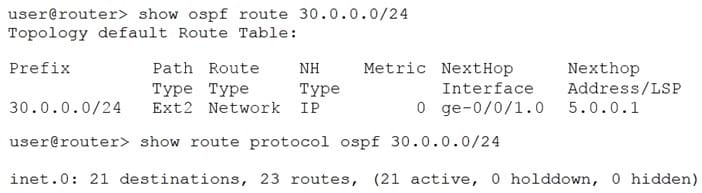
You notice an inconsistency between the routing table and the OSPF database, as shown in the exhibit. What are two reasons for this behavior? (Choose two.)
A. The LSA is a Type 4 LSA.
B. An OSPF export policy is being applied to the route.
C. An OSPF import policy is being applied to the route.
D. The LSA is a Type 5 LSA.
What information is stored in a VRF table for a BGP Layer 2 VPN? (Choose three.)
A. Layer 2 encapsulation
B. local site ID
C. remote interface of local CE device
D. logical interlace provisioned to local CE device
E. label-switched path
You are asked to configure a series of interface policers and firewall filters, which include policers, on the same device. You must ensure that the two configuration methods do not conflict.
What are two considerations when performing this task? (Choose two.)
A. On inbound traffic, firewall filters are applied before interface policers.
B. On outbound traffic, interface policers are applied before firewall filters.
C. On outbound traffic, firewall filters are applied before interface policers.
D. On inbound traffic, interface policers are applied before firewall filters.
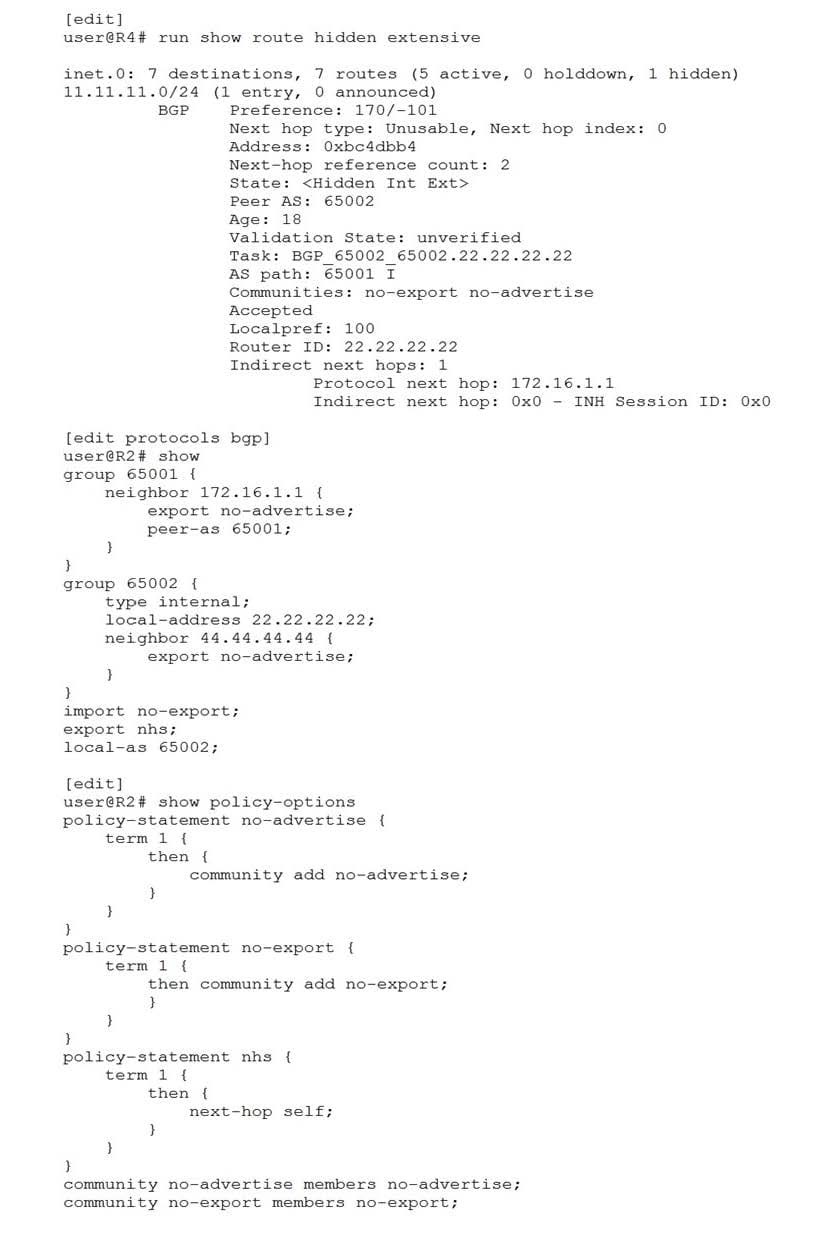
R2 is receiving a route from an EBGP neighbor and is advertising the route to R4.
Referring to the exhibit, which configuration on R2 will solve the issue with the route on R4?
A. Move the no-advertise export policy from group 65002 to a global BGP policy.
B. Move the nhs policy from a global BGP export policy to an export policy under group 65002.
C. Move the no-export policy from a global BGP import policy to an import policy under group 65001.
D. Move the no-advertise export policy from group 65001 to a global BGP policy.
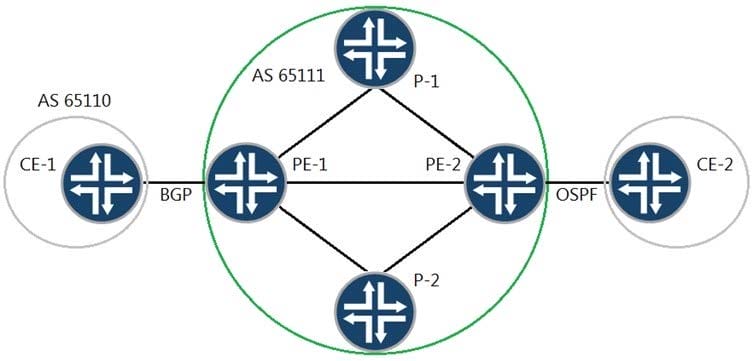
You have a Layer 3 VPN established between PE-1 and PE-2 to allow communication between CE-1 and CE-2. You want to establish communication between CE-1 and CE-2.
Referring to the exhibit, which statement is correct?
A. You will need a BGP export policy on PE-1 to redistribute the OSPF routes, learned from PE-2, to the CE1 BGP neighbor.
B. You will need a VRF import policy on PE-2 to advertise the OSPF routes, learned from CE-2, through the Layer 3 VPN.
C. You will need a VRF export policy on PE-2 to redistribute the OSPF routes, learned from CE-2, through the Layer 3 VPN.
D. You will need a VRF import policy on PE-1 to receive the OSPF routes, learned from PE-2, through the Layer 3 VPN.
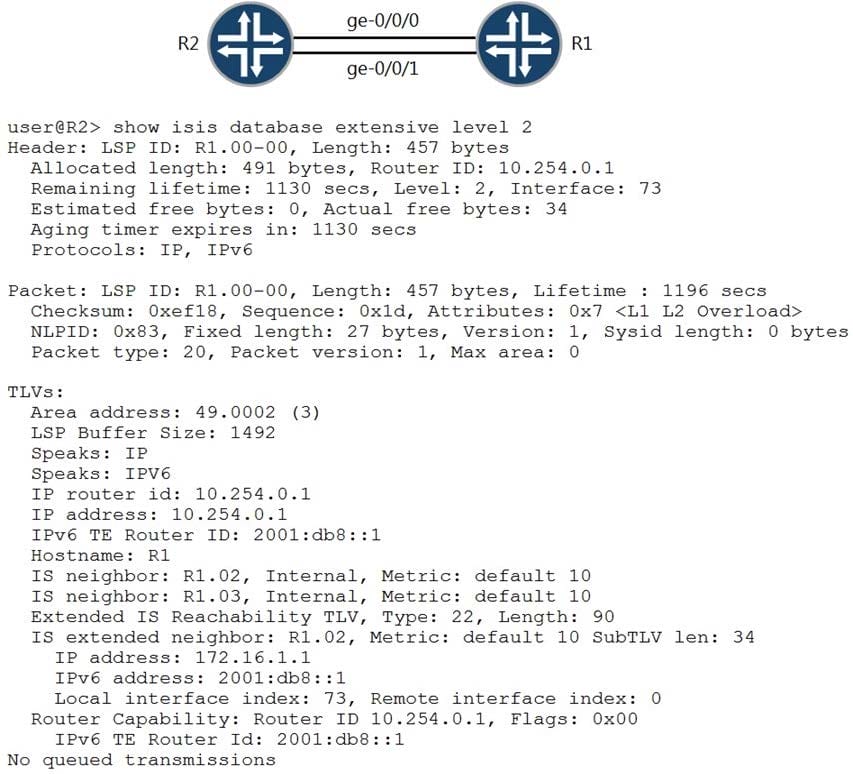
A network administrator is investigating why traffic from R2 is not being forwarded to R1.
Referring to the show isis database command output shown in the exhibit, what is causing this problem on the network?
A. R1 and R2 are in different IS-IS areas.
B. The preferred interface between R1 and R2 is experiencing errors.
C. R1 is configured to drop all incoming traffic.
D. R2 is ignoring specific LSPs from R1 in its SPF calculations.
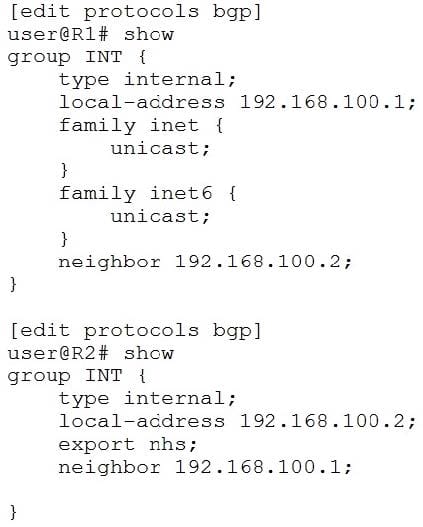
Referring to the exhibit, which statement is true?
A. The BGP session between R1 and R2 will establish correctly and only the inet6 unicast NLRI will pass routing information.
B. The BGP session between R1 and R2 will fail to establish correctly due to an NLRI mismatch.
C. The BGP session between R1 and R2 will establish correctly and the inet unicast and the inet6 unicast NLRIs will pass routing information.
D. The BGP session between R1 and R2 will establish correctly and only the inet unicast NLRI will pass routing information.
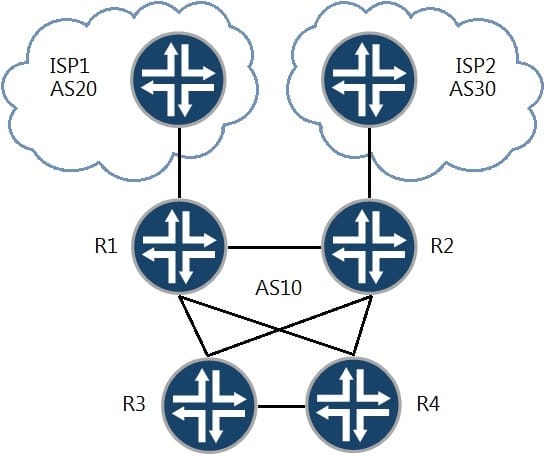
Referring to the exhibit, you want to make ISP1 your preferred connection for inbound and outbound traffic.
Which two steps will accomplish this task? (Choose two.)
A. Create an export policy setting local-preference 200 and next-hop self and apply it to the IBGP peers on R2.
B. Create an export policy to prepend the ASN on advertised routes and apply it to the EBGP peer on R1.
C. Create an export policy to prepend the ASN on advertised routes and apply it to the EBGP peer on R2.
D. Create an export policy setting local-preference 200 and next-hop self and apply it to the IBGP peers on R1.
You are configuring a BGP signaled Layer 2 VPN across your MPLS enabled core network.
In this scenario, which statement is correct?
A. This type of VPN is only supported over LSPs that are using traffic-engineering.
B. You must use a unique route distinguisher value on all PE devices in your environment.
C. You must ensure that all interfaces within the site's configuration are explicitly defined with their remote site identifier values.
D. This type of VPN requires the support of the 12vpn signaling NLRI on all route reflectors and participating PE devices.
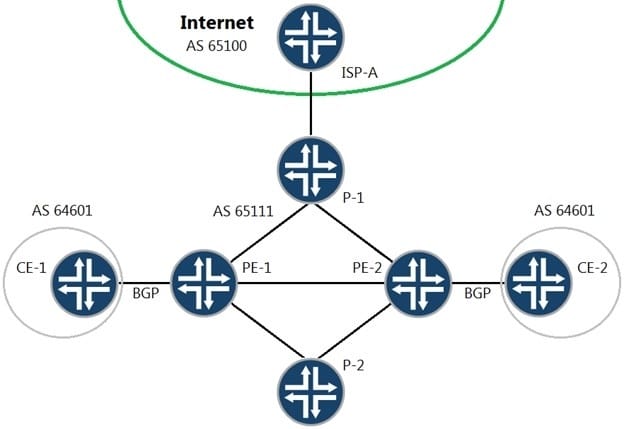
Referring to the exhibit, you have recently established a Layer 3 VPN between PE-1 and PE-2, connecting the two CE sites. Routing information is being shared between sites and the customer has two-way communication. After adding this VPN to your core network, PE-1 and PE-2 are no longer able to forward traffic to the Internet.
In this scenario, what is the problem?
A. You must configure the inet-vpn NLRI for the BGP sessions on both your PE devices.
B. You must configure a multihop external BGP session between your PE devices and the Internet provider's ISP-A device
C. You must configure the inet unicast NLRI for the BGP session on both your PE devices.
D. You must configure a separate internal BGP group on both your PE devices specifically for Internet connectivity.