JN0-636 Online Practice Questions and Answers
Exhibit
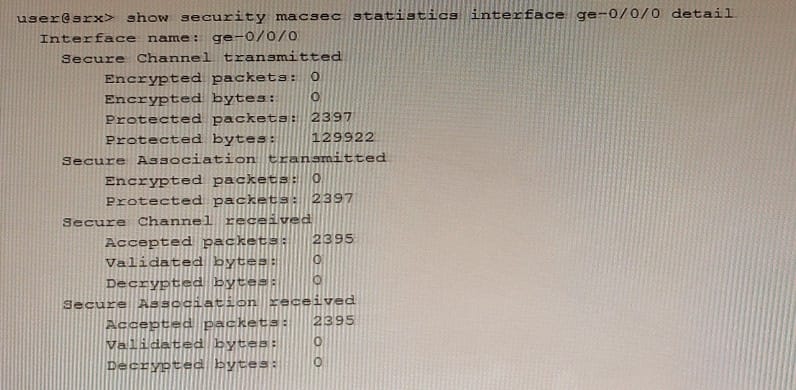
Referring to the exhibit, which two statements are true? (Choose two.)
A. The data that traverses the ge-0/070 interface is secured by a secure association key.
B. The data that traverses the ge-070/0 interface can be intercepted and read by anyone.
C. The data that traverses the ge-070/0 interface cannot be intercepted and read by anyone.
D. The data that traverses the ge-O/0/0 interface is secured by a connectivity association key.
The monitor traffic interface command is being used to capture the packets destined to and the from the SRX Series device. In this scenario, which two statements related to the feature are true? (Choose two.)
A. This feature does not capture transit traffic.
B. This feature captures ICMP traffic to and from the SRX Series device.
C. This feature is supported on high-end SRX Series devices only.
D. This feature is supported on both branch and high-end SRX Series devices.
Exhibit

Referring to the exhibit, which two statements are true about the CAK status for the CAK named "FFFP"? (Choose two.)
A. CAK is not used for encryption and decryption of the MACsec session.
B. SAK is successfully generated using this key.
C. CAK is used for encryption and decryption of the MACsec session.
D. SAK is not generated using this key.
What are two important function of the Juniper Networks ATP appliance solution? (Choose two.).
A. Statistics
B. Analysis
C. Detection
D. Filtration
You have noticed a high number of TCP-based attacks directed toward your primary edge device. You are asked to configure the IDP feature on your SRX Series device to block this attack. Which two IDP attack objects would you configure to solve this problem? (Choose two.)
A. Network
B. Signature
C. Protocol anomaly
D. host
Exhibit You are using trace options to verity NAT session information on your SRX Series device Referring to the exhibit, which two statements are correct? (Choose two.)

A. This packet is part of an existing session.
B. The SRX device is changing the source address on this packet from
C. This is the first packet in the session
D. The SRX device is changing the destination address on this packet 10.0.1 1 to 172 20.101.10.
You are connecting two remote sites to your corporate headquarters site; you must ensure that all traffic is secured and only uses a single Phase 2 SA for both sites.
In this scenario, which VPN should be used?
A. An IPsec group VPN with the corporate firewall acting as the hub device.
B. Full mesh IPsec VPNs with tunnels between all sites.
C. A hub-and-spoke IPsec VPN with the corporate firewall acting as the hub device.
D. A full mesh Layer 3 VPN with the corporate firewall acting as the hub device.
Which method does an SRX Series device in transparent mode use to learn about unknown devices in a network?
A. LLDP-MED
B. IGMP snooping
C. RSTP
D. packet flooding
You configured a chassis cluster for high availability on an SRX Series device and enrolled this HA cluster with the Juniper ATP Cloud. Which two statements are correct in this scenario? (Choose two.)
A. You must use different license keys on both cluster nodes.
B. When enrolling your devices, you only need to enroll one node.
C. You must set up your HA cluster after enrolling your devices with Juniper ATP Cloud
D. You must use the same license key on both cluster nodes.
You are configuring transparent mode on an SRX Series device. You must permit IP-based traffic only, and BPDUs must be restricted to the VLANs from which they originate.
Which configuration accomplishes these objectives?

A. Option A
B. Option B
C. Option C
D. Option D