JN0-634 Online Practice Questions and Answers
Which Junos security feature is used for signature-based attack prevention?
A. RADIUS
B. AppQoS
C. IPS
D. PIM
Click the Exhibit button.

Referring to the configuration shown in the exhibit, which statement explains why traffic matching the IDP signature DNS:OVERFLOW:TOO-LONG-TCP-MSG is not being stopped by the SRX Series device?
A. The security policy dmz-pol1 has an action of permit.
B. The IDP policy idp-pol1 is not configured as active.
C. The IDP rule r2 has an ip-action value of notify.
D. The IDP rule r1 has an action of ignore-connection.
Click the Exhibit button.
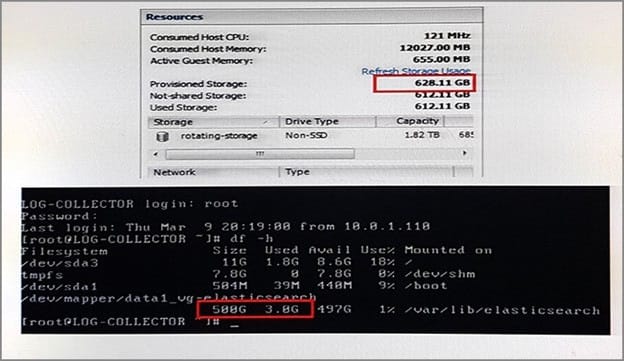
Referring to the exhibit, you have expanded the disk storage size in ESXi for your log collector from 500 GB to 600 GB. However, your log collector's disk size has not changed.
Given the scenario, which two statements are true? (Choose two.)
A. You must run a script from the console to expand the disk size.
B. The ESXi storage parameter is not associated with the Elasticsearch disk size parameter.
C. You must reboot the log collector for storage settings to be updated
D. You must re-run the log collector setup script to update the storage settings.
Which two parameters are required to match in an IDP rule for the terminal option to take effect? (Choose two.)
A. attacks custom-attacks
B. attacks predefined-attacks
C. application
D. source-address
Which three components are part of the AppSecure services suite? (Choose three.)
A. IDP
B. Sky ATP
C. AppQoS
D. AppFW
E. Web filtering
Which feature of Sky ATP is deployed with Software-Defined Secure Networks?
A. zero-day threat mitigation
B. software image snapshot support
C. device inventory management
D. service redundancy daemon configuration support
After downloading the new IPS attack database, the installation of the new database fails. What caused this condition?
A. The new attack database no longer contained an attack entry that was in use.
B. The new attack database was revoked between the time it was downloaded and installed.
C. The new attack database was too large for the device on which it was being installed.
D. Some of the new attack entries were already in use and had to be deactivated before installation.
Click the Exhibit button.

Referring to the exhibit, a user with IP address 10.1.1.85 generates a request that triggers the HTTP:EXT:DOT-LNK IDP signature that is a member of the "HTTP ?All" predefined attack group.
In this scenario, which statement is true?
A. The session will be closed and a reset sent to the client and server.
B. A Differentiated Services code point value of 8 will be applied.
C. No action will be taken and the attack information will be logged.
D. The session will be dropped with no reset sent to the client or server.
Click the Exhibit button.
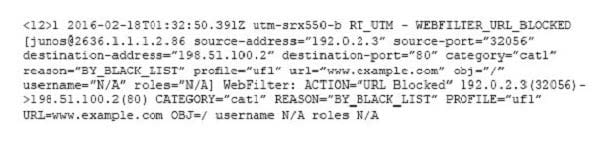
A customer submits a service ticket complaining that access to http://www.example.com/ has been blocked.
Referring to the log message shown in the exhibit, why was access blocked?
A. All illegal source port was utilized.
B. The URI matched a profile entry.
C. The user/role permissions were exceeded.
D. There was a website category infraction.
Your network includes SRX Series devices at all headquarter, data center, and branch locations. The headquarter and data center locations use high-end SRX Series devices, and the branch locations use branch SRX Series devices. You are asked to deploy IPS on the SRX Series devices using one of the available IPS deployment modes.
In this scenario, which two statements are true? (Choose two.)
A. Inline tap mode provides enforcement.
B. Inline tap mode can be used at all locations.
C. Integrated mode can be used at all locations.
D. Integrated mode provides enforcement.