JN0-541 Online Practice Questions and Answers
When connecting to a sensor using SSH, which account do you use to login?
A. admin
B. super
C. netscreen
D. root
A newly re-imaged sensor is running IDP 4.0 code. You want to assign IP address 10.1.1.1 to the sensor. Which method do you use to do this?
A. Connect to the sensor's console port, login as root, and answer theEasyConfig
B. Use SSH to connect to the sensor at IP 192.168.1.1.Login as root, and run ipconfig.
C. Connect to the sensor's console port, login as admin, and answer theEasyConfig
D. Use SSH to connect to the sensor at IP 192.168.1.1.Login as admin, and run ipconfig.
Exhibit:
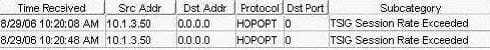
You work as an administrator at Certkiller .com. Study the exhibit carefully. In the exhibit, which rule base would have generated the log message?
A. traffic anomaly
B. backdoor
C. networkhoneypot
D. SYN protector
On a newly re-imaged sensor, which three TCP ports are open on its eth0 interface? (Choose three.)
A. 7801
B. 7803
C. 22
D. 443
E. 80
Which two statements are true about packet logging? (Choose two.)
A. Packets captured are stored inpcap format.
B. IDP senor will tag all replayed packets are offline.
C. Packets logged can be replayed back into the IDP Sensor.
D. Packets captured cannot be replayed back into the IDP Sensor
What are two ways to verify that your rules in the Security Policies are not being shadowed? (Choose two.)
A. You can verify your security policy from the CLI of the Sensor.
B. You can verify your security policy from the IDP User Interface.
C. IDP Management Server can verify your Security policy automatically from the CLI of the Management Server.
D. You must manually verify your rules by hand to ensure they do not shadow each other.
Which three statements are true about custom reports? (Choose three.)
A. Creating reports using indexed columns is significantly faster.
B. All custom reports are stored on per user basis.
C. Log filters can be applied to custom reports.
D. You can export custom reports topdf format.
Exhibit:
You work as an administrator at Certkiller .com. Study the exhibit carefully. In the mode shown in the exhibit, IDP Sensor can protect Server A against attacks being initiated from which three hosts? (Choose three.)
Exhibit:
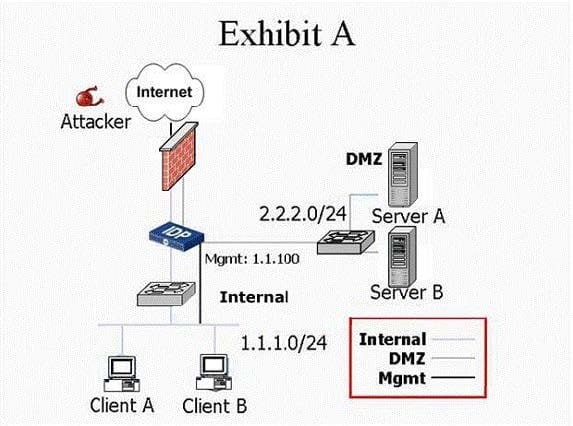
A. Attacker
B. Server B
C. Client B
D. Client A
Which two statements are true about the packet data in Log Viewer? (Choose two.)
A. Packet data can only be viewed from the Log Viewer using internal packet viewer.
B. Packet data can be viewed from an external and internal packet viewer.
C. Packet data captured cannot be disabled per rule.
D. Packet data can be captured by rules in the MainRulebase.
What two statements are true about the Attack Object update process? (Choose two.)
A. The Attack Update must be manually downloaded by the administrator from the Juniper site and installed on each IDP S ensor.
B. The administrator is given the choice of which Dynamic Groups to update.
C. Attacks objects are downloaded from the Juniper site over TCP/443 (SSL) from the IDP User Interface.
D. A list of new, updated and removed attacks objects are displayed to the administrator.