JN0-334 Online Practice Questions and Answers
You are asked to improve resiliency for individual redundancy groups in an SRX4600 chassis cluster. Which two features would accomplish this task? (Choose two.)
A. IP address monitoring
B. control link recovery
C. interface monitoring
D. dual fabric links
Your network uses a remote e-mail server that is used to send and receive e-mails for your users. In this scenario, what should you do to protect users from receiving malicious files through e-mail?
A. Deploy Sky ATP IMAP e-mail protection
B. Deploy Sky ATP MAPI e-mail protection
C. Deploy Sky ATP SMTP e-mail protection
D. Deploy Sky ATP POP3 e-mail protection
Which statement describes the AppTrack module in AppSecure?
A. The AppTrack module provides enforcement with the ability to block traffic, based on specific applications.
B. The AppTrack module provides control by the routing of traffic, based on the application.
C. The AppTrack module identifies the applications that are present in network traffic.
D. The AppTrack module provides visibility and volumetric reporting of application usage on the network.
What is the default session timeout value for ICMP and UDP traffic?
A. 30 seconds
B. 30 minutes
C. 60 seconds
D. 5 minutes
Click the Exhibit button.
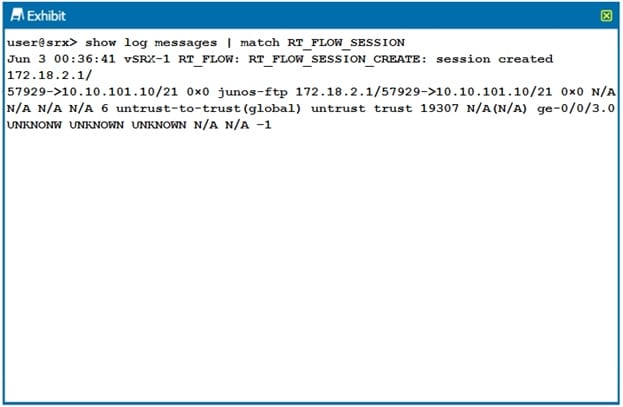
The output shown in the exhibit is displayed in which format?
A. syslog
B. sd-syslog
C. binary
D. WELF
Which feature is used when you want to permit traffic on an SRX Series device only at specific times?
A. scheduler
B. pass-through authentication
C. ALGs
D. counters
You must fine tune an IPS security policy to eliminate false positives. You want to create exemptions to the normal traffic examination for specific traffic.
Which two parameters are required to accomplish this task? (Choose two.)
A. source IP address
B. destination IP address
C. destination port
D. source port
Which two statements describe JSA? (Choose two.)
A. Security Director must be used to view third-party events rom JSA flow collectors.
B. JSA supports events and flows from Junos devices, including third-party devices.
C. JSA events must be manually imported into Security Directory using an SSH connection.
D. JSA can be used as a log node with Security Director or as a standalone solution.
Which two protocols are supported for Sky ATP advanced anti-malware scanning? (Choose two.)
A. POP3
B. MAPI
C. IMAP
D. SMTP
Click the Exhibit button.
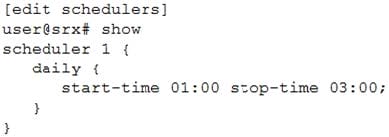
You have configured the scheduler shown in the exhibit to prevent users from accessing certain websites from 1:00 PM to 3:00 PM Monday through Friday. This policy will remain in place until further notice. When testing the policy, you determine that the websites are still accessible during the restricted times.
In this scenario, which two actions should you perform to solve the problem? (Choose two.)
A. Add the saturday excludeparameter and the sunday excludeparameter to ensure weekends are excluded from the schedule.
B. Use the 13:00 parameter and the 15:00 parameter when specifying the time.
C. Use the start-dateparameter to specify the date for each Monday and use the stop-dateparameter to specify the date for each Friday.
D. Use the PM parameter when specifying the time in the schedule.