JN0-230 Online Practice Questions and Answers
BY default, revenue interface are placed into which system-defined security zone on an SRX series device?
A. Trust
B. Null
C. Junos-trust
D. untrust
Exhibit.
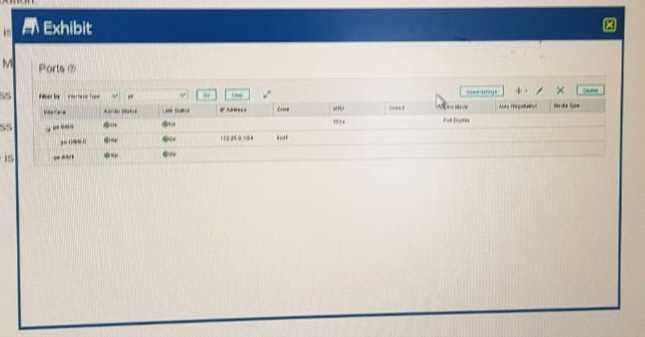
Which statement is correct regarding the interface configuration shown in the exhibit?
A. The interface MTU has been increased.
B. The IP address has an invalid subnet mask.
C. The IP address is assigned to unit 0.
D. The interface is assigned to the trust zone by default.
You have created a zones-based security policy that permits traffic to a specific webserver for the marketing team. Other groups in the company are not permitted to access the webserver. When marketing users attempt to access the server they are unable to do so. What are two reasons for this access failure? (Choose two.)
A. You failed to change the source zone to include any source zone.
B. You failed to position the policy after the policy that denies access to the webserver.
C. You failed to commit the policy change.
D. You failed to position the policy before the policy that denies access the webserver
Which two private cloud solution support vSRX devices? (Choose two.)
A. Microsoft Azure
B. Amazon Web Services (AWS)
C. VMware Web Services (AWS)
D. VMware NSX
E. Contrail Cloud
Which statement about IPsec is correct?
A. IPsec can provide encryption but not data integrity.
B. IPsec support packet fragmentation by intermediary devices.
C. IPsec support both tunnel and transport modes.
D. IPsec must use certificates to provide data encryption
Your company uses SRX Series devices to secure the edge of the network. You are asked protect the
company from ransom ware attacks.
Which solution will satisfy this requirement?
A. Sky ATP
B. AppSecure
C. Unified security policies
D. screens
Which method do VPNs use to prevent outside parties from viewing packet in clear text?
A. Integrity
B. Authentication
C. Encryption
D. NAT_T
Your company has been assigned one public IP address. You want to enable internet traffic to reach multiple servers in your DMZ that are configured with private address. In this scenario, which type of NAT would be used to accomplish this tasks?
A. Static NAT
B. Destination NAT
C. Source NAT
D. NAT without PAT
Which two statements about security policy processing on SRX series devices are true? (choose two)
A. Zone-Based security policies are processed before global policies.
B. Traffic matching a global policy cannot be processed against a firewall filter
C. Zone-Based security policies are processed after global policies
D. Traffic matching a zone-based policy is not processed against global polices.
Which zone is considered a functional zone?
A. Trust
B. Junos host
C. Null
D. Management