JN0-1361 Online Practice Questions and Answers
Your company is designing a new data center in a remote location that must be connected to your local data center. You have a service provider connection between the CE devices at each site. You want to implement EVPN with VXLAN services between sites, but the service provider does not offer EVPN services. Which two statements are true in this scenario? (Choose two )
A. The provider's edge devices must map your VXLAN VNIs to MPLS LSPs within the provider network at each site
B. The customer's edge devices within your data center can act as VXLAN Layer 2 gateways
C. You can still implement EVPN service across the service provider as long as there is IP reachability between the sites.
D. The service provider must provide an MPLS-based VPN connection between sites
Which two statements about BFD are correct? (Choose two)
A. BFD provides link failure detection for static routes.
B. BFD modifies each protocol timer to improve link failure detection.
C. NSR maintains BFD sessions during Routing Engine switchover.
D. GRES is required for BFD sessions to be established.
Which Juniper Networks platform automates the orchestration of compute, storage, and networking resources to create and manipulate OpenStack clouds?
A. NorthStar
B. Contrail
C. WANDL
D. RingMaster
Your customer wants an MPLS-based L3VPN service between multiple remote locations. Which two statements are true regarding the customer's WAN edge devices? (Choose two )
A. They must have EBGP configured.
B. They require routes for all remote sites.
C. They must have MPLS configured.
D. They require IP connectivity with the PEs.
You are asked to design a DDoS prevention system to help mitigate denial-of-service attacks that target your customers. The management group wants to know the effect FlowSpec may have on current network operations if it is implemented as a solution. In this scenario which two statements are correct? (Choose two )
A. FlowSpec can block traffic based on stateful flow information.
B. FlowSpec can block traffic based on the source address.
C. FlowSpec requires Jflow implementation and licensing.
D. FlowSpec can block traffic based on the destination address.
What are two considerations for all WAN designs that use best industry practices? (Choose two )
A. to provide a dynamic routing protocol internally in the LAN
B. to provide scalability
C. to provide ease of deployment
D. to provide VXLAN and EVPN solutions
Your customer is deploying a data center with redundant connections for WAN services through ISP-1 and ISP-2. Your customer has decided to deploy an active/passive Internet connection uplink model and pay-per-use for a passive connection associated with ISP-2. The customer wants to ensure limited use of the connection through ISP-2. Which two actions would you perform to meet the objective? (Choose two )
A. Extend the AS Path length on the prefix advertised to ISP-1 to influence ingress traffic to enter through ISP-1.
B. Use MED and Origin to direct northbound traffic flows out ISP-1
C. Extend the AS Path length on the prefix advertised to ISP-2 to influence ingress traffic to enter through ISP-1.
D. Use Local Preference to direct northbound traffic flows out ISP-1
You have a customer that operates multiple branch offices and they want a low cost access solution. The WAN must be secure What would satisfy their requirement?
A. an encrypted MPLS service
B. an IPsec VPN using broadband connections
C. a private WAN
D. a managed MPLS service
Exhibit: Within ISP E, R1 is load-balancing traffic destined to ISP D over the R1-R2-R5 and R1-R4-R5 paths. At some point, a link degradation event occurs in the network as shown in the exhibit. You want R1 to rapidly learn of the path failure.
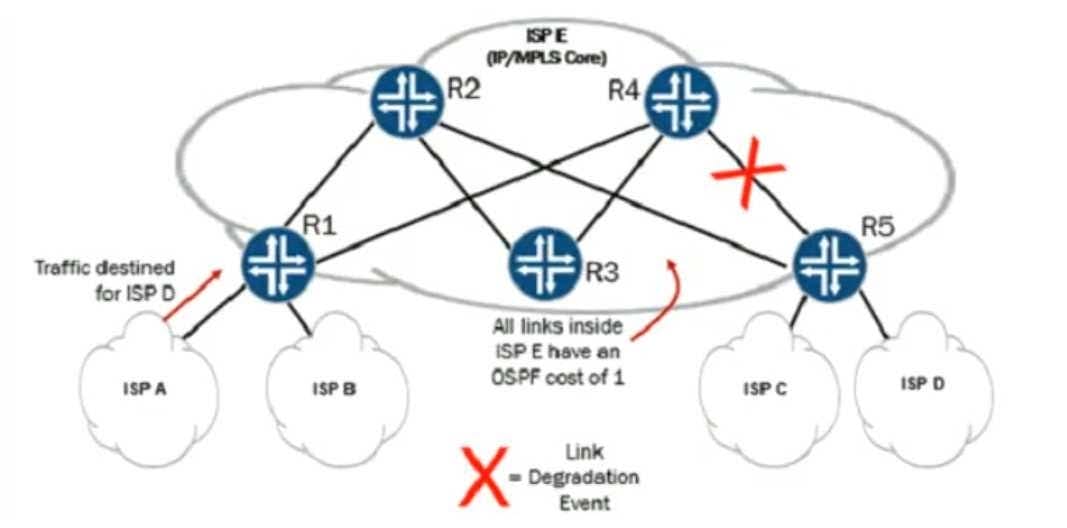
A. Adjust the OSPF hello timer to a subsecond value between R1 and R4.
B. Enable Bidirectional Forwarding Detection between R1 and R4.
C. Enable Bidirectional Forwarding Detection between R4 and R5.
D. Adjust the OSPF hello timer to a subsecond value between R4 and R5.
You are designing a solution for an energy trading organization that allows them to stream natural gas prices to trading partners. Prices will be streamed to trading partners using the Internet. Trading regulations require that any trading data streamed over a public network must be encrypted and authenticated. Which connectivity solution meets these requirements?
A. L2VPN
B. IPsec
C. VPLS
D. L3VPN