JN0-1332 Online Practice Questions and Answers
Policy Enforcer provides which benefit?
A. log management
B. command and control protection
C. centralized management of security devices
D. IPsec encryption
You have multiple SRX chassis clusters on a single broadcast domain. Why must you assign different cluster IDs in this scenario?
A. to avoid MAC address conflicts
B. to avoid control link conflicts
C. to avoid node numbering conflicts
D. to avoid redundancy group conflicts
You are deploying Security Director with the logging and reporting functionality for VMs that use SSDs. You expect to have approximately 20,000 events per second of logging in your network.
In this scenario, what is the minimum number of log receiver devices that you should use?
A. 4
B. 3
C. 2
D. 1
Your customer needs help designing a single solution to protect their combination of various Junos network devices from unauthorized management access.
Which Junos OS feature will provide this protection?
A. Use a firewall filter applied to the fxp0 interface
B. Use a security policy with the destination of the junos-host zone
C. Use the management zone host-inbound-traffic feature
D. Use a firewall filter applied to the lo0 interface
Which two protocols are supported natively by the Junos automation stack? (Choose two.)
A. NETCONF
B. PyEZ
C. Jenkins
D. CIP
Which two steps should be included in your security design process? (Choose two.)
A. Identify external attackers
B. Define safety requirements for the customer's organization
C. Identify the firewall enforcement points
D. Define overall security policies
You are asked to design a VPN solution between 25 branches of a company. The company wants to have the sites talk directly to each other in the event of a hub device failure. The solution should follow industry standards.
Which solution would you choose in this scenario?
A. AutoVPN
B. Auto Discovery VPN
C. Group VPN
D. full mesh VPN
You are designing a network management solution that provides automation for Junos devices. Your customer wants to know which solutions would require additional software to be deployed to existing Junos devices.
Which two solutions satisfy this scenario? (Choose two.)
A. SaltStack
B. Ansible
C. Puppet
D. Chef
You are designing an enterprise WAN network that must connect multiple sites. You must provide a design proposal for the security elements needed to encrypt traffic between the remote sites.
Which feature will secure the traffic?
A. BFD
B. OSPF
C. GRE
D. IPsec
Click the Exhibit button.
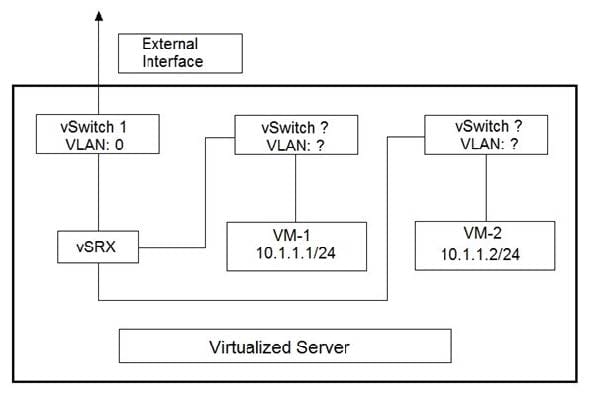
You are designing the virtualized server deployment shown in the exhibit in your data center. The vSRX device is acting as a Layer 2 firewall and the two VMs must communicate through the vSRX device.
Which two actions must you perform to accomplish this task? (Choose two.)
A. Place both VMs in the same vSwitch
B. Place both VMs in the same VLAN
C. Place both VMs in different vSwitches
D. Place both VMs in different VLANs