JN0-1331 Online Practice Questions and Answers
You are designing a data center security solution for a customer. The customer asks that you provide a DDoS solution. Several IPsec tunnels will be terminated at the data center gateway.
Which type of security is your customer asking you to implement?
A. segmentation
B. intra-data center policy enforcement
C. perimeter protection
D. compliance
You are designing an SDSN security solution for a new campus network. The network will consist of Juniper Networks Policy Enforcer, Juniper Networks switches, third-party switches, and SRX Series devices. The switches and the SRX Series devices will be used as security enforcement points. The design must be able to change the VLAN mapping of the switch port of a user that is already authenticated to the network in the event that the end user device becomes compromised.
Which component satisfies this requirement?
A. certificate server
B. RADIUS server
C. Security Director
D. DHCP server
You want to deploy JATP in your network that uses SRX Series devices.
In this scenario, which feature must you enable on the SRX Series devices?
A. SSL forward proxy
B. AppSecure
C. UTM antivirus
D. IPS
You have multiple SRX chassis clusters on a single broadcast domain. Why must you assign different cluster IDs in this scenario?
A. to avoid MAC address conflicts
B. to avoid control link conflicts
C. to avoid node numbering conflicts
D. to avoid redundancy group conflicts
A hosting company is migrating to cloud-based solutions. Their customers share a physical firewall cluster, subdivided into individual logical firewalls for each customer. Projection data shows that the cloud service will soon deplete all the resources within the physical firewall. As a consultant, you must propose a scalable solution that continues to protect all the cloud customers while still securing the existing physical network.
In this scenario, which solution would you propose?
A. Deploy a vSRX cluster in front of each customer's servers while keeping the physical firewall cluster
B. Deploy a software-defined networking solution
C. Remove the physical firewall cluster and deploy vSRX clusters dedicated to each customer's servers
D. Replace the physical firewall cluster with a higher-performance firewall
Your customer needs help designing a single solution to protect their combination of various Junos network devices from unauthorized management access.
Which Junos OS feature will provide this protection?
A. Use a firewall filter applied to the fxp0 interface
B. Use a security policy with the destination of the junos-host zone
C. Use the management zone host-inbound-traffic feature
D. Use a firewall filter applied to the lo0 interface
Your customer is getting ready to deploy a new WAN architecture. It must be simple to set up, address hub scaling concerns, and allow the automatic addition of new sites without requiring changes to the hub site. They want to deploy either AutoVPN or Auto Discovery VPN.
In this scenario, why would you propose Auto Discovery VPN as a solution?
A. Your customer requires direct spoke-to-spoke communication
B. OSPF support is required
C. Only Auto Discovery VPN supports the automatic addition of valid spokes
D. Your customer needs to configure the hub site only once
Click the Exhibit button.
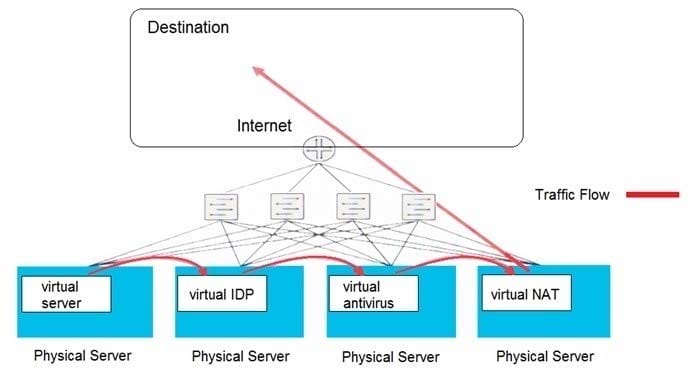
Which type of security solution is shown in this exhibit?
A. service chain model
B. centralized model
C. inline security model
D. de-centralized model
You are implementing Routing Engine protection, and packets are processed in a specific order. In this scenario, which function processed a received packet last?
A. loopback interface input policer
B. loopback interface input firewall filter
C. physical interface input firewall filters
D. physical interface input policer
Which two steps should be included in your security design process? (Choose two.)
A. Identify external attackers
B. Define safety requirements for the customer's organization
C. Identify the firewall enforcement points
D. Define overall security policies