JN0-1101 Online Practice Questions and Answers
When discussing network reliability, what does the term "five nines" mean?
A. The network is up 99.999% of the time.
B. The network is up .99999% of the time.
C. The network is up 9.9999% of the time.
D. The network is up .09999% of the time.
You are asked to provide a design proposal for an enterprise customer that currently has a three-tier
switching infrastructure. The customer wants your design to collapse their Layer 2 infrastructure into two
distinct layers.
In this scenario, what are two benefits of moving to the new infrastructure? (Choose two.)
A. The total number of devices is increased.
B. The overall network performance is increased.
C. The number of connections between devices is decreased.
D. The number of protocols used is decreased.
Click the Exhibit button.
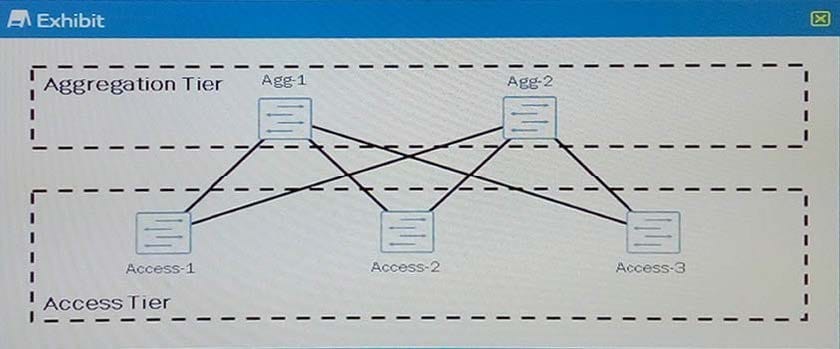
Referring to the exhibit, you are designing a Layer 2 data center and you want to make sure that all the
links between the access tier and the aggregation tier are used.
What should you do to accomplish this task?
A. Use VRRP on Agg-1 and Agg-2.
B. Place Agg-1 and Agg-2 in a Virtual Chassis.
C. Use RSTP on all devices.
D. Use BGP load balancing on all devices.
What are three environmental characteristics that affect the campus network design? (Choose three.)
A. transmission media characteristics
B. distribution of users
C. locations of wiring closets
D. PC operating system
E. remote site connectivity
What are two valid reasons to enable route summarization? (Choose two.)
A. to reduce routing overhead
B. to reduce the coexistence of BGP with IGPs
C. to benefit from a hierarchical IP addressing plan
D. to enable the use of more than one routing protocol
What are two reasons why you would send an RFP to multiple vendors (Choose two.)
A. to eliminate vendors who cannot meet the requirements
B. to warranty the process against fraud
C. to satisfy international law requiring a minimum of three vendors
D. to compare competing proposals
You are asked to provide a WAN design proposal for connecting together multiple customer sites. As part of your design, you want to use IPsec tunnels to ensure that traffic is private and secure. Which statement is true about the proposed solution?
A. IPsec packets can be fragmented once encrypted.
B. IPsec tunnels will require an MPLS infrastructure through the WAN.
C. IPsec can require MTU modifications to accommodate the additional overhead.
D. Packets that are passed through an IPsec tunnel are not encrypted.
You have multiple virtual machines in a hypervisor deployment within a data center. Your client wants to
enforce security measures on east-west traffic between virtual machines.
Which solution should you recommend in this situation?
A. JATP
B. Sky ATP
C. Virtual Chassis
D. vSRX
What are two tiers used in a traditional data center design? (Choose two.)
A. core
B. aggregation
C. compute
D. user
You are designing a network management strategy for a new network. The requirements for the
management of network devices are shown below:
Administrator passwords must have an expiration date.
Administrators must be assigned role-specific privileges on each device.
In this scenario, which statement is true?
A. Local authentication must be used on each device.
B. A centralized AAA system must be used for authentication.
C. All devices must be configured with the same privilege levels.
D. Each user must have a unique login account.