ISSMP Online Practice Questions and Answers
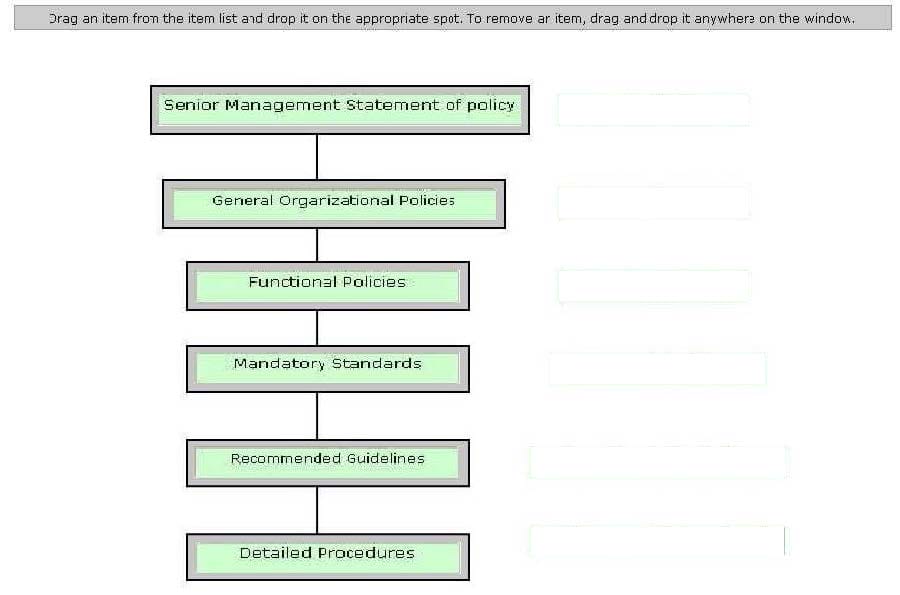
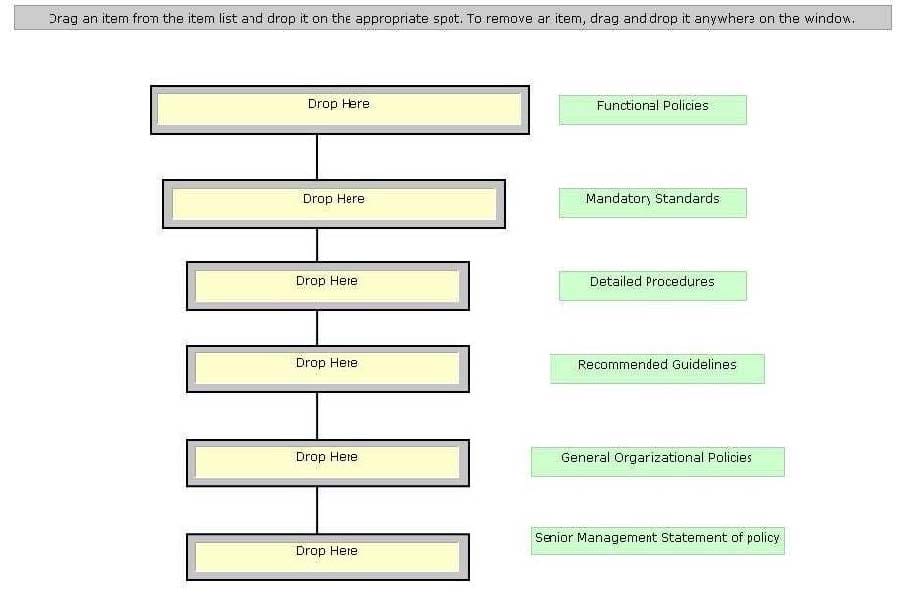
Policies are considered the first and highest level of documentation, from which the lower-level elements of standards, procedures, and guidelines flow. Drag and drop each policy statement according to its hierarchy level (i.e. from top to bottom).
Select and Place:
SIMULATION Fill in the blank with an appropriate phrase.___________ is the process of using a strategy and plan of what patches should be applied to which systems at a specified time. Correct
Which of the following terms describes a repudiation of a contract that occurs before the time when performance is due?
A. Expected breach
B. Actual breach
C. Anticipatory breach
D. Nonperforming breach
You work as a Product manager for Marioiss Inc. You have been tasked to start a project for securing the network of your company. You want to employ configuration management to efficiently manage the procedures of the project. What will be the benefits of employing configuration management for completing this project? Each correct answer represents a complete solution. Choose all that apply.
A. It provides object, orient, decide and act strategy.
B. It provides a live documentation of the project.
C. It provides the risk analysis of project configurations.
D. It provides the versions for network devices.
Which of the following methods can be helpful to eliminate social engineering threat? Each correct answer represents a complete solution. Choose three.
A. Password policies
B. Vulnerability assessments
C. Data encryption
D. Data classification
Which of the following measurements of an enterprise's security state is the process whereby an organization establishes the parameters within which programs, investments, and acquisitions reach the desired results?
A. Information sharing
B. Ethics
C. Performance measurement
D. Risk management
Which of the following subphases are defined in the maintenance phase of the life cycle models?
A. Change control
B. Configuration control
C. Request control
D. Release control
Which of the following is the best method to stop vulnerability attacks on a Web server?
A. Using strong passwords
B. Configuring a firewall
C. Implementing the latest virus scanner
D. Installing service packs and updates
Which of the following laws is the first to implement penalties for the creator of viruses, worms, and other types of malicious code that causes harm to the computer systems?
A. Gramm-Leach-Bliley Act
B. Computer Fraud and Abuse Act
C. Computer Security Act
D. Digital Millennium Copyright Act
Which of the following statements reflect the 'Code of Ethics Canons' in the '(ISC)2 Code of Ethics'? Each correct answer represents a complete solution. Choose all that apply.
A. Provide diligent and competent service to principals.
B. Protect society, the commonwealth, and the infrastructure.
C. Give guidance for resolving good versus good and bad versus bad dilemmas.
D. Act honorably, honestly, justly, responsibly, and legally.