HPE6-A84 Online Practice Questions and Answers
Refer to the scenario.
A customer requires these rights for clients in the "medical-mobile" AOS firewall role on Aruba Mobility Controllers (MCs):
1.
Permitted to receive IP addresses with DHCP
2.
Permitted access to DNS services from 10.8.9.7 and no other server
3.
Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
4.
Denied access to other 10.0.0.0/8 subnets
5.
Permitted access to the Internet
6.
Denied access to the WLAN for a period of time if they send any SSH traffic
7.
Denied access to the WLAN for a period of time if they send any Telnet traffic
8.
Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with "medical-mobile" clients, only send return traffic.
The exhibits below show the configuration for the role.
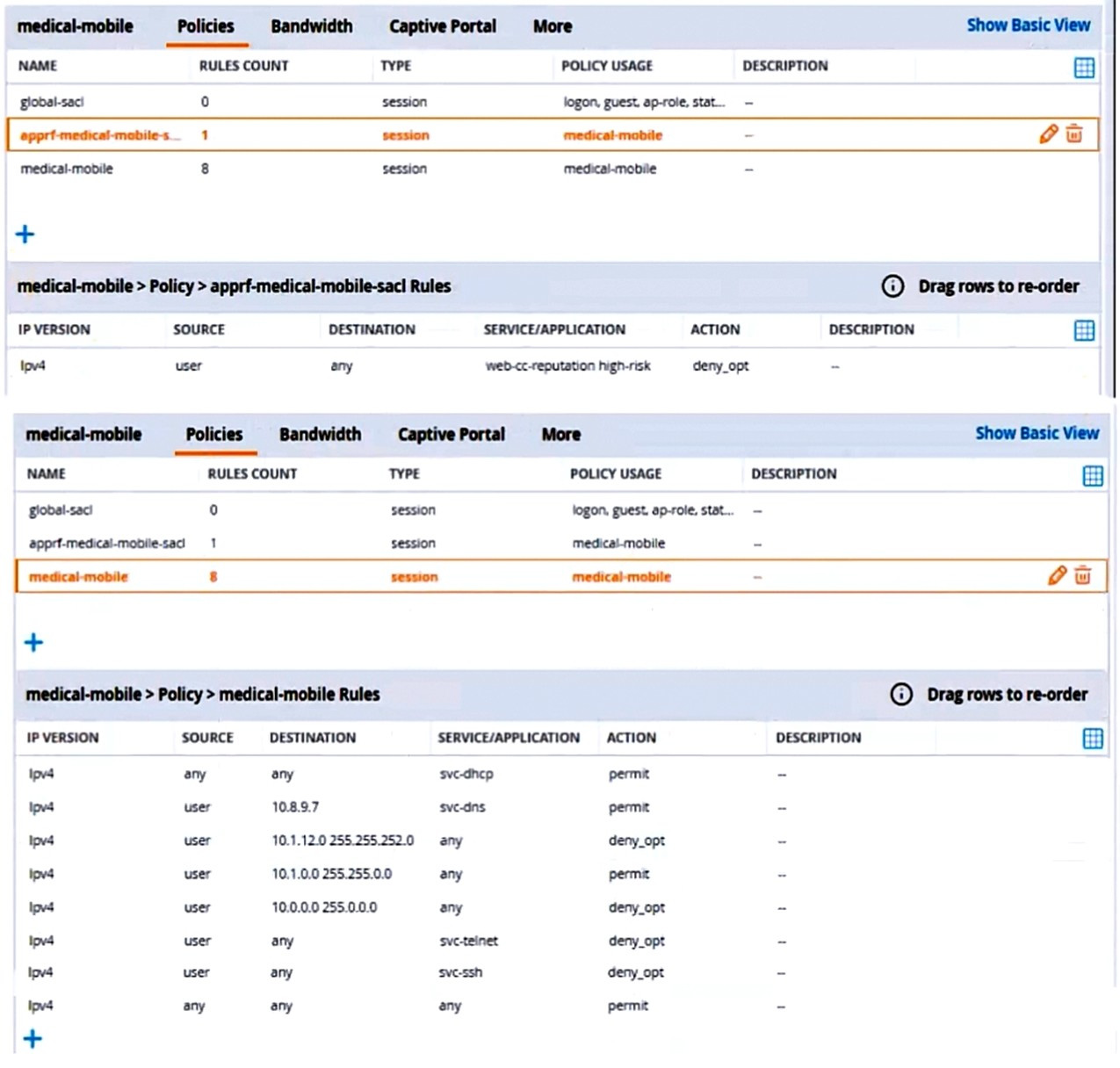
There are multiple issues with this configuration. What is one change you must make to meet the scenario requirements? (In the options, rules in a policy are referenced from top to bottom. For example, "medical-mobile" rule 1 is "ipv4 any any svc-dhcp permit," and rule 8 is "ipv4 any any any permit".)
A. In the "medical-mobile" policy, move rules 2 and 3 between rules 7 and 8.
B. In the "medical-mobile" policy, change the subnet mask in rule 3 to 255.255.248.0.
C. Move the rule in the "apprf-medical-mobile-sacl" policy between rules 7 and 8 in the "medical-mobile" policy.
D. In the "medical-mobile" policy, change the source in rule 8 to "user."
Refer to the scenario.
A customer requires these rights for clients in the "medical-mobile" AOS firewall role on Aruba Mobility Controllers (MCs):
1.
Permitted to receive IP addresses with DHCP
2.
Permitted access to DNS services from 10.8.9.7 and no other server
3.
Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
4.
Denied access to other 10.0.0.0/8 subnets
5.
Permitted access to the Internet
6.
Denied access to the WLAN for a period of time if they send any SSH traffic
7.
Denied access to the WLAN for a period of time if they send any Telnet traffic
8.
Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with "medical-mobile" clients, only send return traffic.
The exhibits below show the configuration for the role.
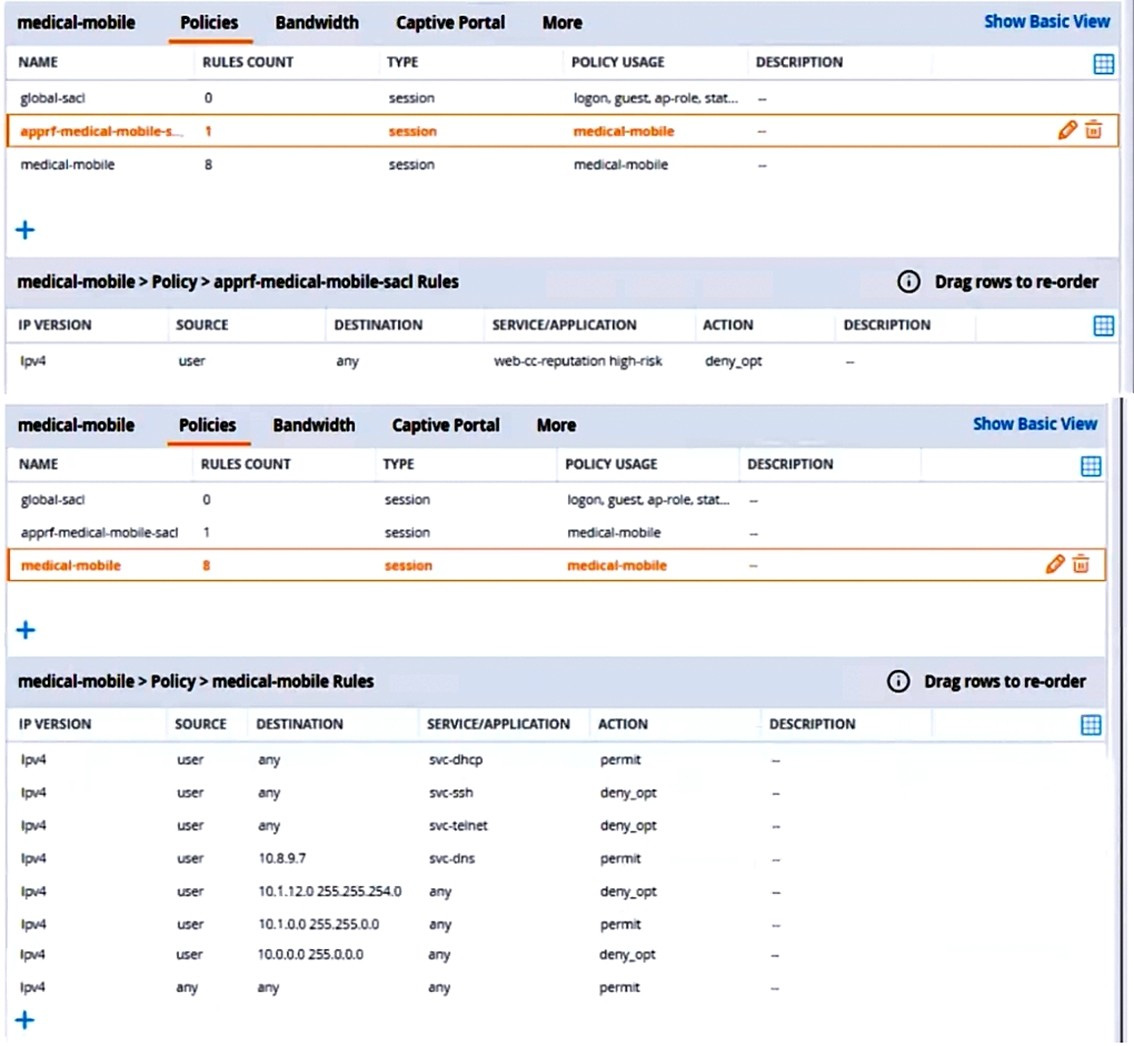
What setting not shown in the exhibit must you check to ensure that the requirements of the scenario are met?
A. That denylisting is enabled globally on the MCs' firewalls
B. That stateful handling of traffic is enabled globally on the MCs' firewalls and on the medical-mobile role.
C. That AppRF and WebCC are enabled globally and on the medical-mobile role
D. That the MCs are assigned RF Protect licenses
Refer to the exhibit.
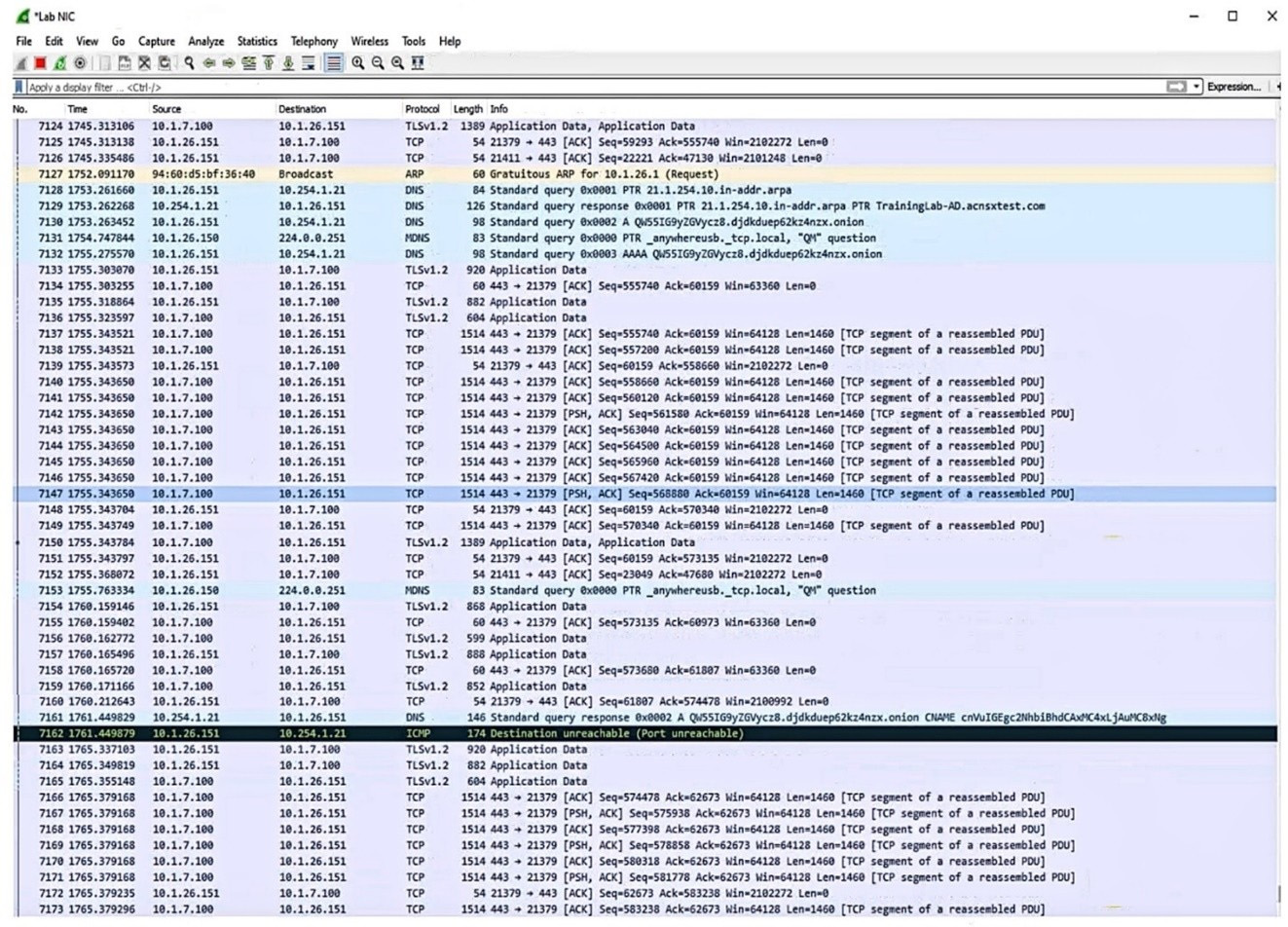
Which security issue is possibly indicated by this traffic capture?
A. An attempt at a DoS attack by a device acting as an unauthorized DNS server
B. A port scan being run on the 10.1.7.0/24 subnet
C. A command and control channel established with DNS tunneling
D. An ARP poisoning or man-in-the-middle attempt by the device at 94:60:d5:bf:36:40
Refer to the scenario.
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement 802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba gateway cluster. The gateway cluster should assign these clients to the "eth- internet" role. The gateway should also handle assigning clients
to their VLAN, which is VLAN 20.
The plan for the enforcement policy and profiles is shown below:

The gateway cluster has two gateways with these IP addresses:
Gateway 1
1.
VLAN 4085 (system IP) = 10.20.4.21
2.
VLAN 20 (users) = 10.20.20.1
3.
VLAN 4094 (WAN) = 198.51.100.14
Gateway 2
1.
VLAN 4085 (system IP) = 10.20.4.22
2.
VLAN 20 (users) = 10.20.20.2
3.
VLAN 4094 (WAN) = 198.51.100.12
VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster. If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
What is one change that you should make to the solution?
A. Change the ubt-client-vlan to VLAN 13.
B. Configure edge ports in VLAN trunk mode.
C. Remove VLAN assignments from role configurations on the gateways.
D. Configure the UBT solution to use VLAN extend mode.
You are configuring gateway IDS/IPS settings in Aruba Central.
For which reason would you set the Fail Strategy to Bypass?
A. To permit traffic if the IPS engine falls to inspect It
B. To enable the gateway to honor the allowlist settings configured in IDS/IPS policies
C. To tell gateways to stop enforcing IDS/IPS policies if they lose connectivity to the Internet
D. To avoid wasting IPS engine resources on filtering traffic for unauthenticated clients
Refer to the scenario.
A customer is migrating from on-prem AD to Azure AD as its sole domain solution. The customer also manages both wired and wireless devices with Microsoft Endpoint Manager (Intune).
The customer wants to improve security for the network edge. You are helping the customer design a ClearPass deployment for this purpose. Aruba network devices will authenticate wireless and wired clients to an Aruba ClearPass Policy Manager (CPPM) cluster (which uses version 6.10).
The customer has several requirements for authentication. The clients should only pass EAP-TLS authentication if a query to Azure AD shows that they have accounts in Azure AD. To further refine the clients' privileges, ClearPass also should use information collected by Intune to make access control decisions.
Assume that the Azure AD deployment has the proper prerequisites established.
You are planning the CPPM authentication source that you will reference as the authentication source in 802.1X services.
How should you set up this authentication source?
A. As Kerberos type
B. As Active Directory type
C. As HTTP type, referencing the Intune extension
D. AS HTTP type, referencing Azure AD's FODN
A customer's admins have added RF Protect licenses and enabled WIDS for a customer's AOS 8-based solution. The customer wants to use the built-in capabilities of APs without deploying dedicated air monitors (AMs). Admins tested rogue AP detection by connecting an unauthorized wireless AP to a switch. The rogue AP was not detected even after several hours.
What is one point about which you should ask?
A. Whether APs' switch ports support all the VLANs that are accessible at the edge
B. Whether admins enabled wireless containment
C. Whether admins set at least one radio on each AP to air monitor mode
D. Whether the customer is using non-standard Wi-Fi channels in the deployment
Refer to the scenario.
A customer has an AOS10 architecture that is managed by Aruba Central. Aruba infrastructure devices authenticate clients to an Aruba ClearPass cluster.
In Aruba Central, you are examining network traffic flows on a wireless IoT device that is categorized as "Raspberry Pi" clients. You see SSH traffic. You then check several more wireless IoT clients and see that they are sending SSH also.
You want a relatively easy way to communicate the information that an IoT client has used SSH to Aruba CPPM.
What is one prerequisite?
A. Enable event processing on subscribers in the ClearPass cluster.
B. In CPPM's CA trust list, add the Aruba Infrastructure usage to the DigiCert certificate.
C. Obtain a data collector token from Central's platform integration settings.
D. Create an API application and token within the REST API settings.
A customer has an AOS 10-based mobility solution, which authenticates clients to Aruba ClearPass Policy Manager (CPPM). The customer has some wireless devices that support WPA2 in personal mode only.
How can you meet these devices' needs but improve security?
A. Use MPSK on the WLAN to which the devices connect.
B. Configure WIDS policies that apply extra monitoring to these particular devices.
C. Connect these devices to the same WLAN to which 802.1X-capable clients connect, using MAC-Auth fallback.
D. Enable dynamic authorization (RFC 3576) in the AAA profile for the devices.
Refer to the scenario.
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement 802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba gateway cluster. The gateway cluster should assign these clients to the "eth- internet" role. The gateway should also handle assigning clients to their VLAN, which is VLAN 20.
The plan for the enforcement policy and profiles is shown below: The gateway cluster has two gateways with these IP addresses:
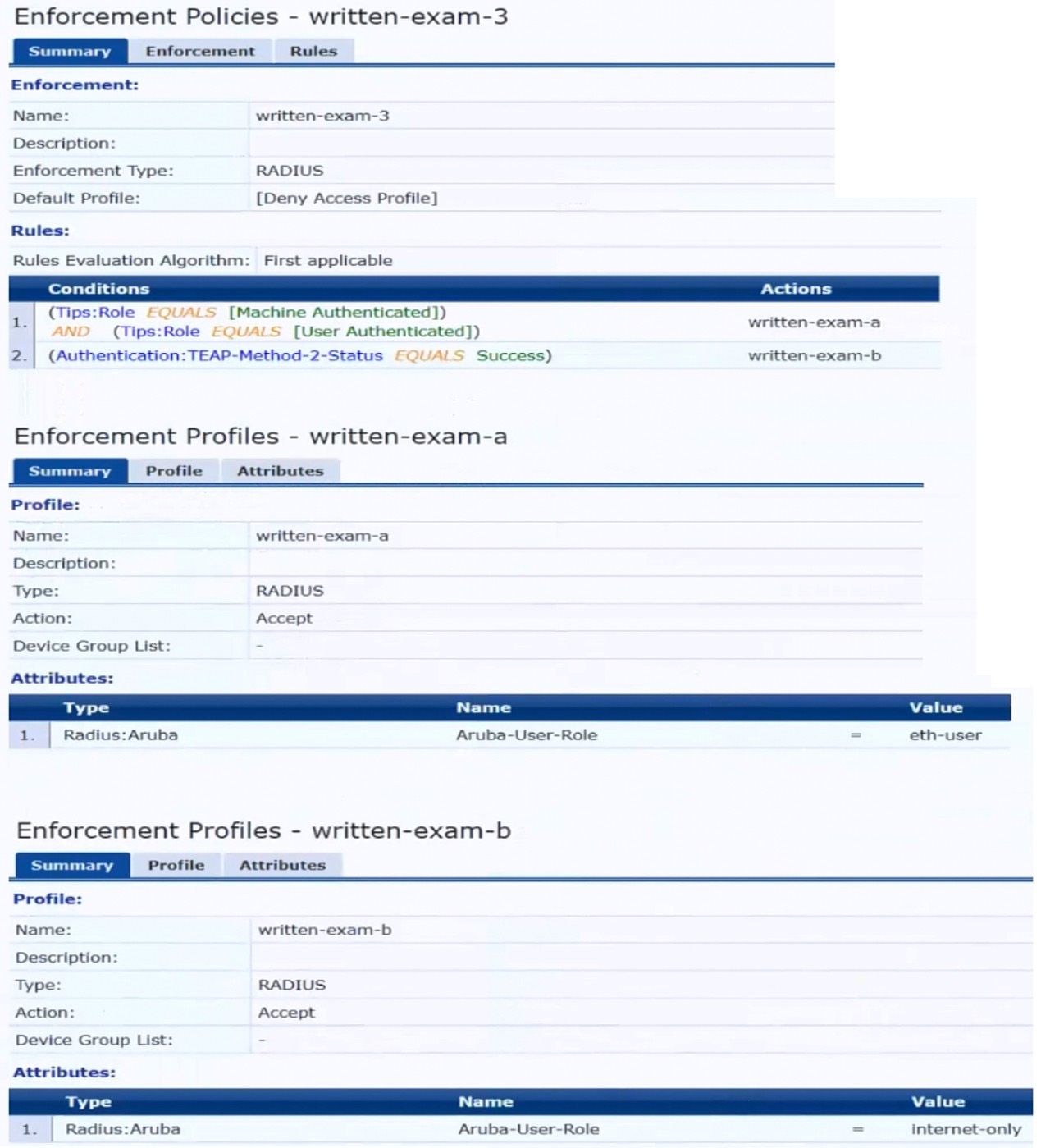
Gateway 1
1.
VLAN 4085 (system IP) = 10.20.4.21
2.
VLAN 20 (users) = 10.20.20.1
3.
VLAN 4094 (WAN) = 198.51.100.14
Gateway 2
1.
VLAN 4085 (system IP) = 10.20.4.22
2.
VLAN 20 (users) = 10.20.20.2
3.
VLAN 4094 (WAN) = 198.51.100.12
VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster. If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
You are setting up the UBT zone on an AOS-CX switch.
Which IP addresses should you define in the zone?
A. Primary controller = 10.20.4.21; backup controller = 10.20.4.22
B. [Primary controller = 198.51.100.14; backup controller = 10.20.4.21
C. Primary controller = 10 20 4 21: backup controller not defined
D. Primary controller = 10.20.20.254; backup controller, not defined