HPE6-A79 Online Practice Questions and Answers
An Aruba Mobility Master (MM) - Mobility Controller (MC) solution is connected to a wired network that is ready to prioritize DSCP marked traffic. A group of WMM-enabled clients sends traffic marked at L2 only.
What must the network administrator do to map those markings to DSCP equivalent values when traffic is received by the APs?
A. Enable WMM in the SSID profile.
B. Enable WMM in the VAP profile.
C. Enable Skype4Business ALG Support.
D. Enable traffic to be marked with session ACLs.
Refer to the exhibit.
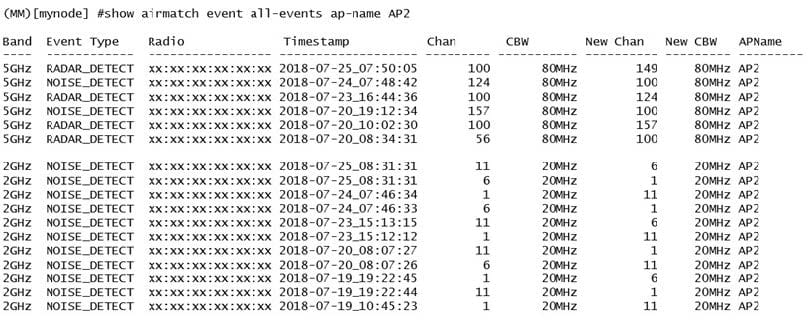
A network administrator deploys a Mobility Master (MM) - Mobility Controller (MC) network with Aps in different locations. Users in one of the locations report that the WiFi network works fine for several hours, and then they are suddenly
disconnected. This symptom may happen at any time, up to three times every day, and lasts no more than two minutes.
After some research, the network administrator logs into the MM and reviews the output shown in the exhibit.
Based on this information, what is the most likely reason users get disconnected?
A. Adaptive Radio Management is reacting to RF events.
B. AirMatch is applying a scheduled optimization solution.
C. Users in the 2.4 GHz band are being affected by high interference.
D. AirMatch is reacting to non-scheduled RF events.
An Aruba WiFi solution for a football stadium includes 2500 APs, two Mobility Masters (MM), and eight Mobility Controllers (MCs). Key requirements are seamless roaming and even distribution of APs and clients, even during a MC failure. Which MC's deployment option offers seamless roaming, and even AP client distribution among all MCs before and after a MC failure?
A. a two-member HA group in dual mode
B. an eight-member L2-connected cluster
C. two four-member L2-connected clusters
D. an eight-member HA group in dual mode
Refer to the exhibit.
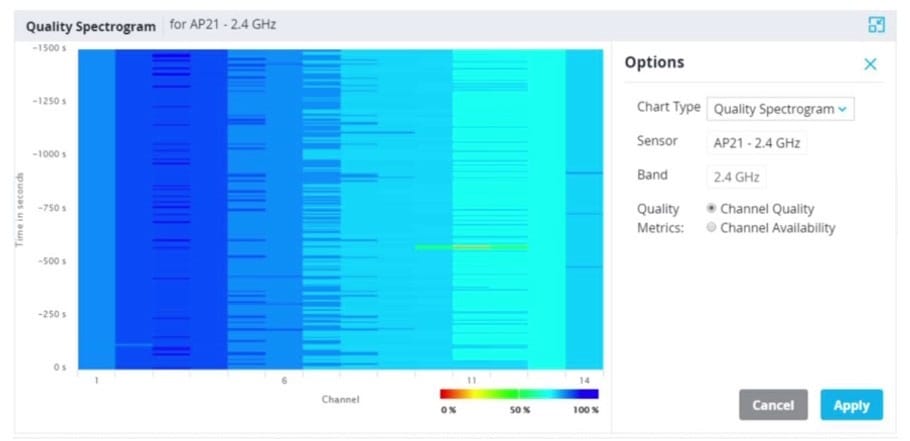
Based on the output shown in the exhibit, which channel offers the highest quality?
A. Channel 1
B. Channel 6
C. Channel 11
D. Channel 14
A fully functional WLAN is deployed in a campus network using the following script.
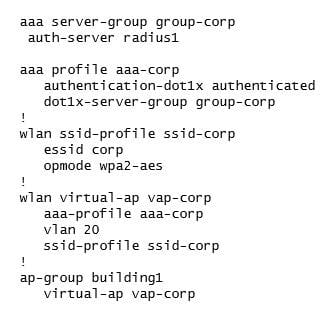
Which part of the script can a network administrator re-use to assign a different default role to users when they connect to the same SSID in a second building?
A. server group and ssid profile
B. server group and VAP profile
C. server group, aaa profile, and ssid profile
D. server group and VAP
An organization wants to deploy a WLAN infrastructure that provides connectivity to these client categories:
Employees Contractors Guest users Corporate IoT legacy devices that support no authentication or encryption Employees and contractors must authenticate with company credentials and get network access based on AD group membership. Guest users are required to authenticate with captive portal using predefined credentials. Only employees will run L2 encryption.
Which implementation plan fulfills the requirements while maximizing the channel usage?
A. Create VAP1 to run WPA2-AES and 802.1x authentication, VAP2 to run opensystem encryption with MAC authentication, and VAP3 to run opensystem with captive portal and L2 fail through.
B. Create a single VAP to run WPA2-AES and 802.1x authentication, MAC authentication L2 fail through, captive portal, and VIA support.
C. Create VAP1 to run WPA2-AES and 802.1x authentication, VAP2 to run opensystem encryption with MAC authentication, and VAP3 to run opensystem with captive portal.
D. Create VAP1 to run WPA2-AES and 802.1x authentication, and VAP2 to run opensystem encryption with MAC authentication and captive portal.
Refer to the exhibit.
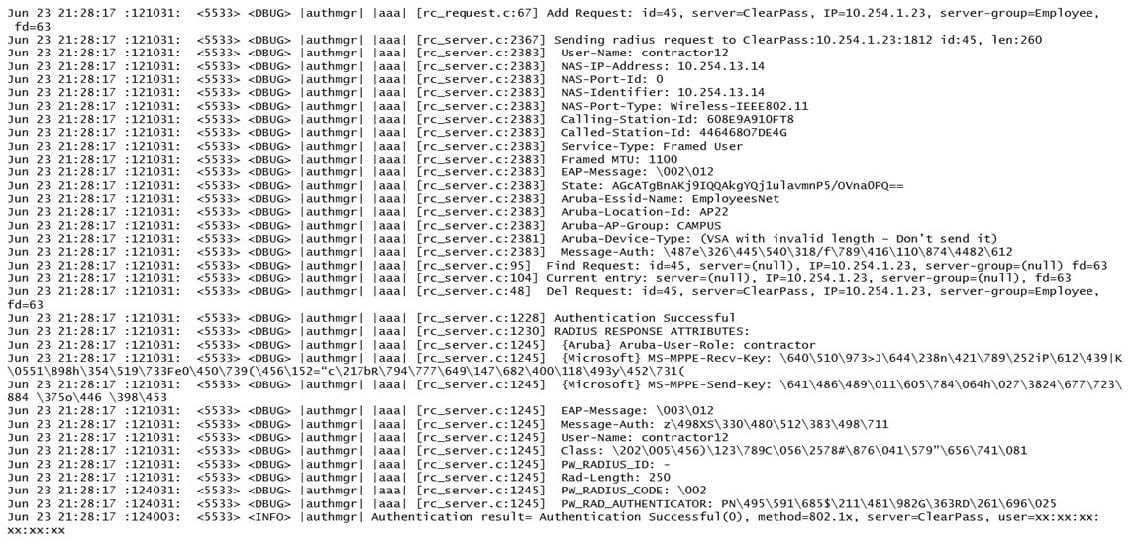
A network administrator wants to allow contractors to access the WLAN named EmployeesNet. In order to restrict network access, the network administrator wants to assign this category of users to the contractor user role. To do this, the
network administrator configures ClearPass in a way that it returns the Aruba-User-Role with the contractor value.
When testing the solution, the network administrator receives the wrong role.
What should the network administrator do to assign the contractor role to contractor users without affecting any other role assignment?
A. Check the Download role from the CPPM option in the AAA profile.
B. Set contractor as the default role in the AAA profile.
C. Create Contractor firewall role in the M.
D. Create server deviation rules in the server group.
Refer to the exhibits. Exhibit 1

Exhibit 2

A network administrator adds a new Mobility Controller (MC) to the production Mobility Master (MM) and deploys APs that start broadcasting the employee SSID in the West wing of the building. Suddenly, the employees report client
disconnects. When accessing the MM the network administrator notices that the MC is unreachable, then proceeds to access the MC's console and obtains the outputs shown in the exhibits.
What should the network administrator do next to solve the current problem?
A. Open a TAC case and send the output of tar crash.
B. Kill two zombie processes then reboot the MC.
C. Verify the license pools in the MM.
D. Decommission the MC from the MM, and add it again.
Refer to the exhibit.
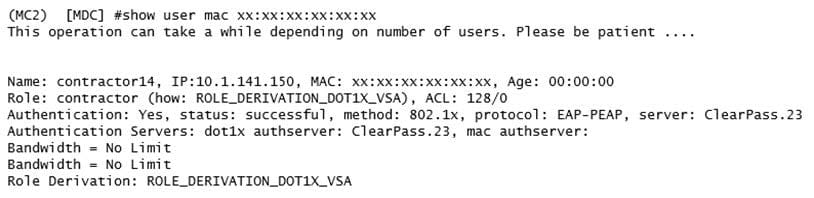
A network administrator is evaluating a deployment to validate that a user is assigned the proper role and reviews the output in the exhibit. How is the role assigned to user?
A. The MC assigned the role based on Aruba VSAs.
B. The MC assigned the machine authentication default user role.
C. The MC assigned the default role based on the authentication method.
D. The MC assigned the role based on server derivation rules.
Refer to the exhibit.
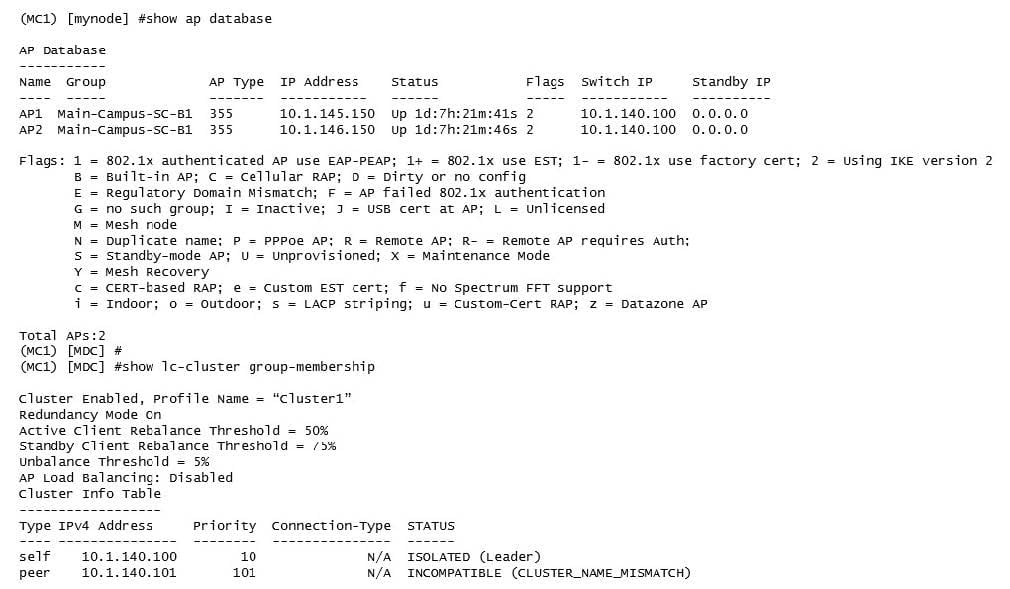
After deploying several cluster pairs, the network administrator notices that all APs assigned to Cluster1 communicate with MC1 instead of being distributed between members of the cluster. Also, no IP addresses are shown under the Standby IP column.
What should the network administrator do to fix this situation?
A. Apply the same cluster profile to both members.
B. Enable Cluster AP load balancing.
C. Rename the cluster profile as "CLUSTER1".
D. Place MCs at the same hierarchical group level.