HPE6-A78 Online Practice Questions and Answers
A company is deploying ArubaOS-CX switches to support 135 employees, which will tunnel client traffic to an Aruba Mobility Controller (MC) for the MC to apply firewall policies and deep packet inspection (DPI). This MC will be dedicated to receiving traffic from the ArubaOS-CX switches.
What are the licensing requirements for the MC?
A. one AP license per-switch
B. one PEF license per-switch
C. one PEF license per-switch. and one WCC license per-switch
D. one AP license per-switch. and one PEF license per-switch
You have been asked to rind logs related to port authentication on an ArubaOS-CX switch for events logged in the past several hours But. you are having trouble searching through the logs. What is one approach that you can take to find the relevant logs?
A. Add the "-C and *-c port-access" options to the "show logging" command.
B. Configure a logging Tiller for the "port-access" category, and apply that filter globally.
C. Enable debugging for "portaccess" to move the relevant logs to a buffer.
D. Specify a logging facility that selects for "port-access" messages.
What is an Authorized client as defined by ArubaOS Wireless Intrusion Prevention System (WIP)?
A. a client that has a certificate issued by a trusted Certification Authority (CA)
B. a client that is not on the WIP blacklist
C. a client that has successfully authenticated to an authorized AP and passed encrypted traffic
D. a client that is on the WIP whitelist.
What is a reason to set up a packet capture on an Aruba Mobility Controller (MC)?
A. The company wants to use ClearPass Policy Manager (CPPM) to profile devices and needs to receive HTTP User-Agent strings from the MC.
B. The security team believes that a wireless endpoint connected to the MC is launching an attack and wants to examine the traffic more closely.
C. You want the MC to analyze wireless clients' traffic at a lower level, so that the ArubaOS firewall can control the traffic I based on application.
D. You want the MC to analyze wireless clients' traffic at a lower level, so that the ArubaOS firewall can control Web traffic based on the destination URL.
What correctly describes the Pairwise Master Key (PMK) in thee specified wireless security protocol?
A. In WPA3-Enterprise, the PMK is unique per session and derived using Simultaneous Authentication of Equals.
B. In WPA3-Personal, the PMK is unique per session and derived using Simultaneous Authentication of Equals.
C. In WPA3-Personal, the PMK is derived directly from the passphrase and is the same tor every session.
D. In WPA3-Personal, the PMK is the same for each session and is communicated to clients that authenticate
What is one practice that can help you to maintain a digital chain or custody In your network?
A. Enable packet capturing on Instant AP or Moodily Controller (MC) datepath on an ongoing basis
B. Enable packet capturing on Instant AP or Mobility Controller (MC) control path on an ongoing basis.
C. Ensure that all network infrastructure devices receive a valid clock using authenticated NTP
D. Ensure that all network Infrastructure devices use RADIUS rather than TACACS+ to authenticate managers
What role does the Aruba ClearPass Device Insight Analyzer play in the Device Insight architecture?
A. It resides in the cloud and manages licensing and configuration for Collectors
B. It resides on-prem and provides the span port to which traffic is mirrored for deep analytics.
C. It resides on-prem and is responsible for running active SNMP and Nmap scans
D. It resides In the cloud and applies machine learning and supervised crowdsourcing to metadata sent by Collectors
An ArubaOS-CX switch enforces 802.1X on a port. No fan-through options or port-access roles are configured on the port The 802 1X supplicant on a connected client has not yet completed authentication.
Which type of traffic does the authenticator accept from the client?
A. EAP only
B. DHCP, DNS and RADIUS only
C. RADIUS only
D. DHCP, DNS, and EAP only
Refer to the exhibit, which shows the current network topology.
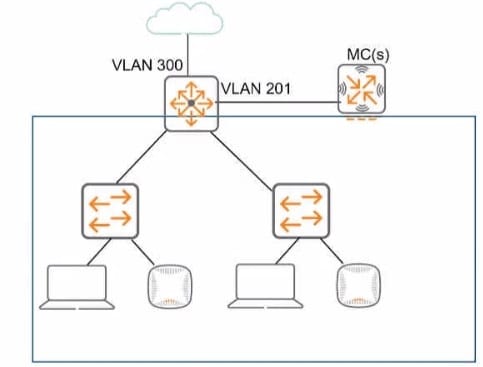
You are deploying a new wireless solution with an Aruba Mobility Master (MM). Aruba Mobility Controllers (MCs). and campus APs (CAPs). The solution will Include a WLAN that uses Tunnel for the forwarding mode and Implements WPA3-Enterprise security.
What is a guideline for setting up the vlan for wireless devices connected to the WLAN?
A. Assign the WLAN to a single new VLAN which is dedicated to wireless users
B. Use wireless user roles to assign the devices to different VLANs in the 100-150 range
C. Assign the WLAN to a named VLAN which specified 100-150 as the range of IDs.
D. Use wireless user roles to assign the devices to a range of new vlan IDs.
What is one way a noneypot can be used to launch a man-in-the-middle (MITM) attack to wireless clients?
A. it uses a combination or software and hardware to jam the RF band and prevent the client from connecting to any wireless networks
B. it runs an NMap scan on the wireless client to And the clients MAC and IP address. The hacker then connects to another network and spoofs those addresses.
C. it examines wireless clients' probes and broadcasts the SSlDs in the probes, so that wireless clients will connect to it automatically.
D. it uses ARP poisoning to disconnect wireless clients from the legitimate wireless network and force clients to connect to the hacker's wireless network instead.