HPE6-A75 Online Practice Questions and Answers
Refer to the exhibit.
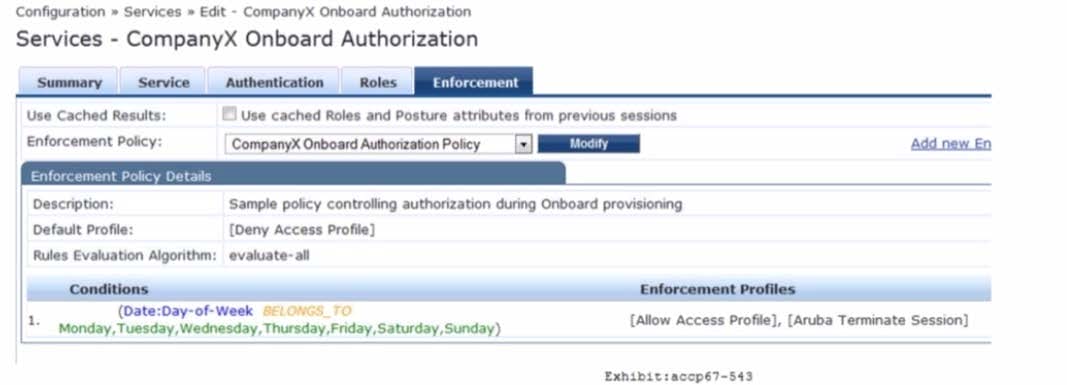
Based on the configuration of the Enforcement Profiles In the Onboard Authorization service shown, which Onboarding action will occur?
A. The device will be disconnected from the network after Onboarding so that an EAP-TLS authentication is not performed.
B. The device will be disconnected from and reconnected to the network after Onboarding is completed.
C. The device's onboard authorization request will be denied.
D. The device will be disconnected after post-Onboarding EAP-TLS authentication, so a second EAP-TLS authentication is performed.
E. After logging in on the Onboard web login page, the device will be disconnected form and reconnected to the network before Onboard begins.
An administrator supports a RAP to a branch office. Employees at the branch office connect to an employee SSID that allows for split tunneling of the employee traffic. The RAP initially connects to the corporate office controller, but later loses connectivity to it.
Which operating mode should the administrator configure for a secondary SSID to be advertised during the loss of connectivity?
A. Standard
B. Persistent
C. Always
D. Backup
Refer to the exhibit.
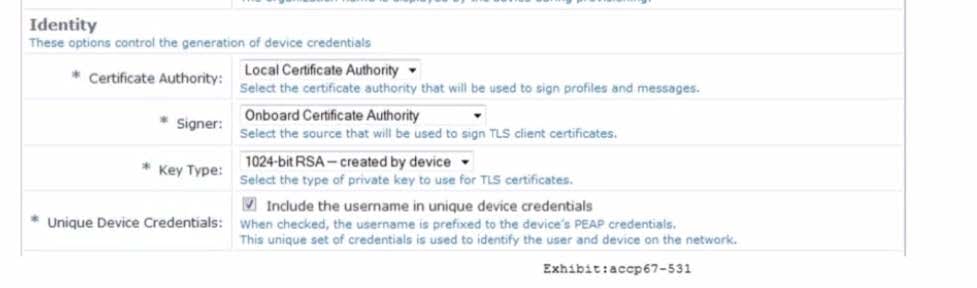
Based on the configuration for the client's certificate private key as shown, which statements accurately describe the settings? (Select two.)
A. More bits in the private key will increase security.
B. The private key for TLS client certificates is not created.
C. The private key is stored in the ClearPass server.
D. More bits in the private key will reduce security.
E. The private key is stored in the user device.
Which statement is true about the Endpoint Profiler? (Select two.)
A. The Endpoint Profiler uses DHCP fingerprinting for device categorization.
B. Data obtained from the Endpoint Profiler can be used in Enforcement Policy.
C. Endpoint Profiler requires a profiling license.
D. The Endpoint Profiler requires the Onboard license to be enabled.
E. The Endpoint Profiler can only categorize laptops and desktops.
Refer to the exhibit.
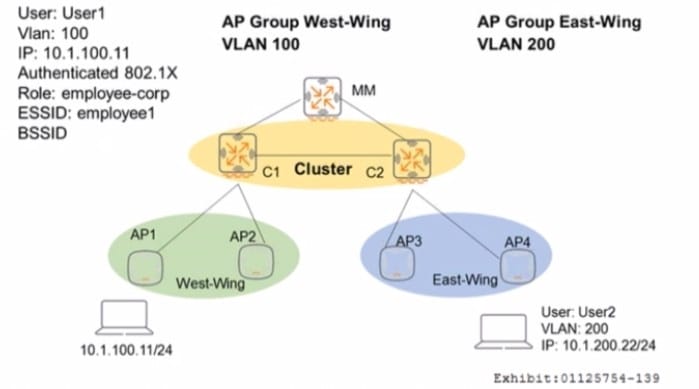
Controllers are configured m a cluster as shown in the exhibit. These are the network details.
A Mobility Master (MM) manages the cluster.
The cluster contains two controllers: C l and C2.
API and AP2 use CI as their Active AP Anchor Controller (A-AAC). with C2 as their Standby AAC (S-AAC).
AP3 and AP4 use C2 as their A-AAC, with CI as their S-AAC.
User1 establishes a wireless connection via API, where the Active User Anchor Controller (A-UAC)
assigned is CI. with C2 as the standby. What happens when User I roams the wireless network and
eventually their session is handled by AP3?
A. The AP3's A-AAC switches to C1, and the user's A-UAC remains on C1.
B. The AP3's A-AAC switches to C2, and the user's A-UAC remains on C2.
C. The AP3's A-AAC switches to C1, and the user's A-UAC remains on C2.
D. The AP3's A-AAC switches to C2, and the user's A-UAC remains on C1.
Refer to the exhibit.
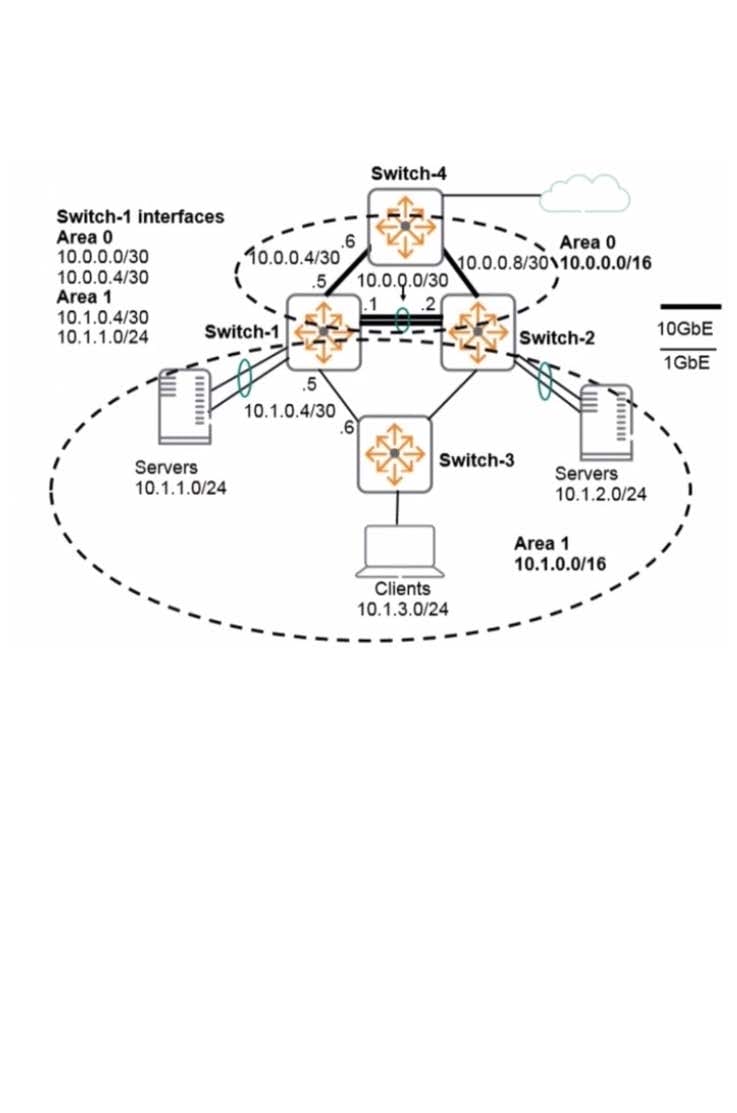
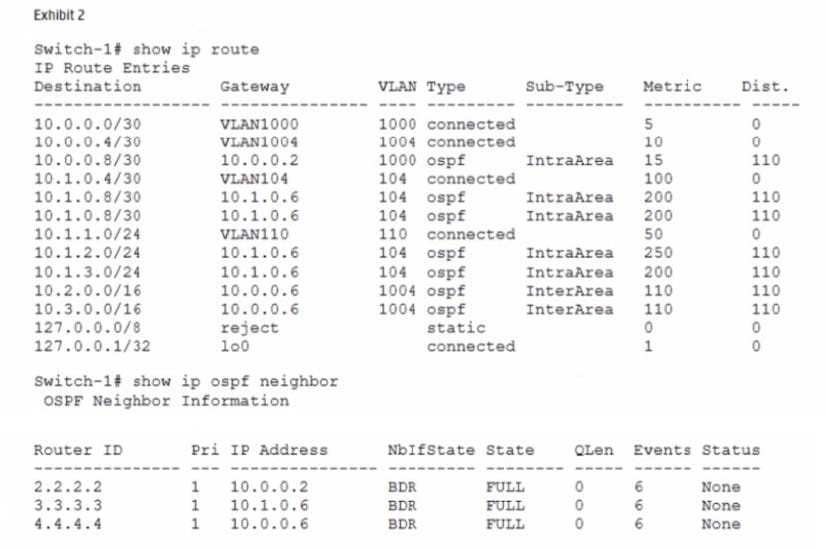
Traffic between the servers m Area l takes a less optimal path rather than the link associated with VLAN l OOO, subnet 10.0.0.0/30. Based on the exhibits, why is this the case?
A. The metric on the VLAN 1000 interface is too low.
B. Switch-1 and Switch-2 cannot achieve adjacency on VLAN 1000 due to mismatches.
C. OSPF routing switches choose the best intra-area routes based on Area 1 links only.
D. The link between Switch-1 and Switch-2 has gone down.
OSPF is configured on an AOS-Switch, and the network administrator sets the router ID to 10.0.0.1. The administrator wants to be able to reach the switch at this ID from any location throughout the OSPF system. The administrator also needs the router ID to De stable and available, even if some links on the switch fail.
What should the administrator do?
A. Make sure that 10.0.0.1 is the IP address on the VLAN with the lowest ID.
B. Configure 10.0.0.1 on a loopback interface, and enable OSPF on that interface.
C. Configure 10.0.0.1 as a manual OSPF neighbor on each switch in the OSPF system.
D. Configure 10.0.0.1 as a secondary IP address on the switch 00BM poet.
A university wants to deploy ClearPass with the Guest module. They have two types of users that need to use web login authentication. The first type of users are students whose accounts are in an Active Directory server. The second type of users are friends of students who need to self-register to access the network.
How should the service be setup in the Policy Manager for this Network?
A. Guest User Repository and Active Directory server both as authentication sources
B. Active Directory server as the authentication source, and Guest User Repository as the authorization source
C. Guest User Repository as the authentication source, and Guest User Repository and Active Directory server as authorization sources
D. Either the Guest User Repository or Active Directory server should be the single authentication source
E. Guest User Repository as the authentication source and the Active Directory server as the authorization source
An administrator configures an ArubaOS-Switch for per -user tunneled node. Which protocols does the switch use to establish and maintain a connection with the Aruba Mobility Controller (MO? (Select two.)
A. GRE
B. SSL
C. PAPI
D. IPSec
Which ArubaOS CLl command can an administrator execute to determine if AP load balancing is enabled in a cluster?
A. show switches
B. show lc-cluster group-membership
C. show aaa cluster essid
D. show ap active