HPE6-A67 Online Practice Questions and Answers
Your boss suggests that you configure a guest self-registration page in ClearPass for the Conference
Events SSID.
Which advantages will this give? (Choose two.)
A. It will allow guest users to create a login account for the web login page.
B. It will stop employees from putting their corporate devices on the event network.
C. It will allow employees to get their own devices securely connected to the network.
D. It will allow the Conference center to collect extra information about the guest.
E. It can be pre-located with guest information from the conference registration.
You have Guest Self-Registration with Internal Sponsorship configured and wish to send users their
credentials automatically.
Which options need to be enabled? (Choose two.)
A. Configure the receipt page actions to send a receipt.
B. Configure the receipt page form to include the Guest Username and password.
C. Configure an Email Server in ClearPass Guest Administration.
D. Configure the Sponsor Confirmation Settings to send an email receipt to the Guest.
E. Configure an Email Server in ClearPass Policy Manager Administration.
What are two ways that devices can download the Onboard provisioning profile and credentials from ClearPass? (Choose two.)
A. from the Android market
B. Over-the-Air API
C. download from iTunes
D. Bonjour
What happens when a client successfully authenticates but does not match any Enforcement Policy rules?
A. no role is applied to the device
B. logon profile is applied to the device
C. default Enforcement profile is applied
D. guest rule is applied to the device
E. default rule is applied to the device
When Active Directory is added as an authentication source, what should the format be for the Active Directory bin DN?
A. admin.domain.com
B. domain.com\admin
C. domain.com
E. admin\domain.com
Refer to the exhibit.
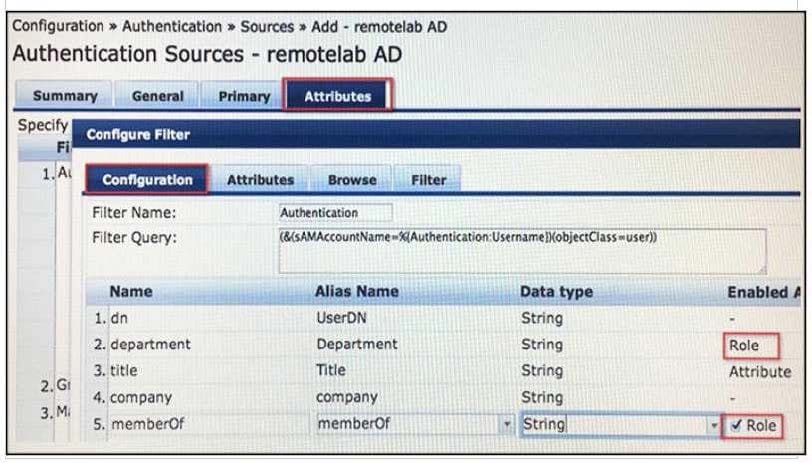
A user has enabled `department' and `memberOf' as roles. What is the direct effect of the user's action?
A. The user's authentication will be rejected if the user does not have an admin user group membership in AD.
B. The user's memberOf attribute is sent back to the controller as a firewall role.
C. The user's department and group membership will be seen in the Access tracker roles section.
D. The user's authentication will be rejected if the user does nothave a department attribute in AD.
E. The user's department is sent back to the controller as a firewall role.
When enforcement action is used in ClearPass to bounce a client?
A. Webpage redirect
B. ACL
C. VLAN attribute
D. RADIUS VSA
E. RADIUS CoA
Refer to the exhibit.
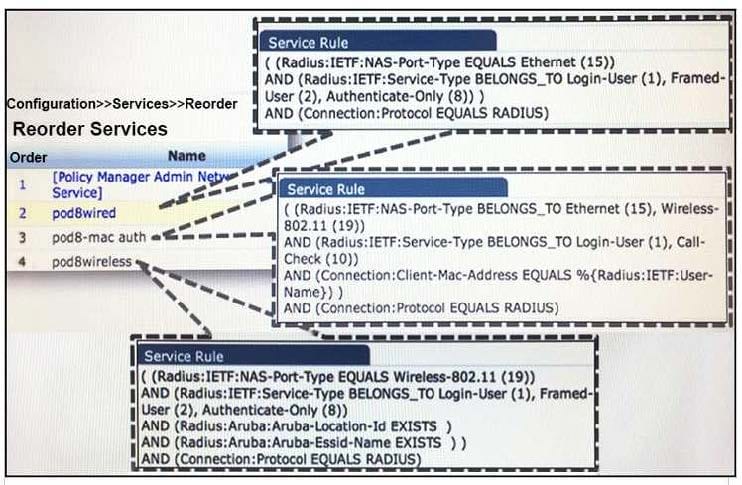
A user connects to an Aruba Access Point wireless SSID named "secure-corporate" and performs an 802.1X authentication with ClearPass as the authentication server. Based on this service configuration, which service will be triggered?
A. pod8-mac auth
B. Noservice will be triggered
C. pod8wireless
D. [Policy Manager Admin Network Service]
E. pod8wired
What is the purpose of a RADIUS IETP Session Timeout attribute being sent to an Aruba Controller when a guest authenticates successfully?
A. For the controller to initiate a RADIUS re-authentication automatically when the time limit is reached.
B. For ClearPass to send a RADIUS CoA message to the client when the time limit is reached.
C. For the user to initiate a RADIUS re-authentication when the time limit is reached.
D. For ClearPass to send a RADIUS CoA message when the time limit is reached.
E. For the Controller to end the user's authenticated session when the time limit is reached.
Which authentication type allows a device to authenticate with a client certificate?
A. 802.1X/EAP
B. WEP Authentication
C. MAC Authentication
D. Captive Portal Authentication
E. Open System Authentication