HPE6-A47 Online Practice Questions and Answers
Refer to the exhibit.
Exhibit 1 shows the logical plan, and Exhibit 2 shows the BOM created with IRIS. An architect plans to propose two 5406Rzl switches as a VSF fabric for a campus network core. Which issue with the plan should the architect correct?
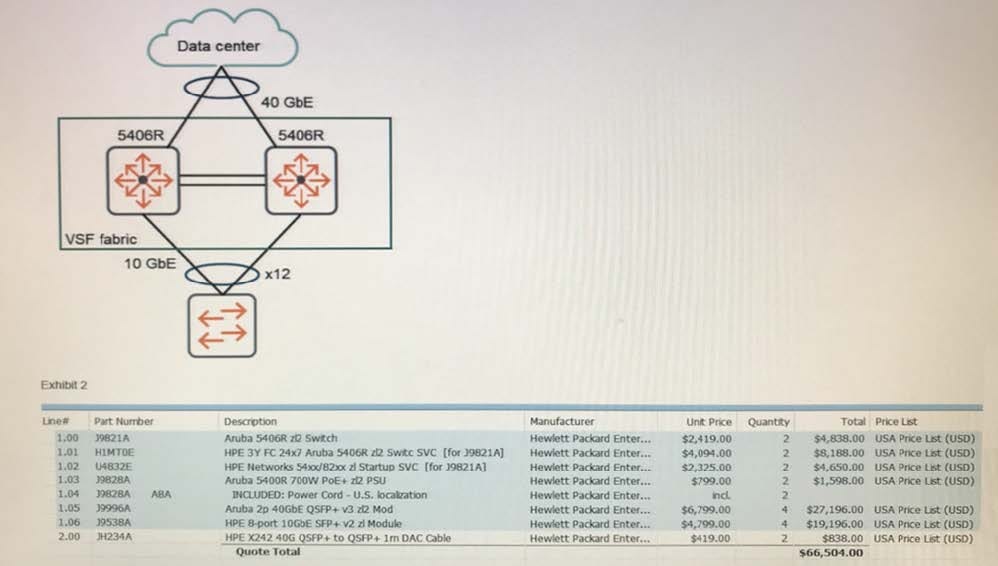
A. Add two QSPF+ MP0 SR4 transceivers.
B. Change the v2 modules to v3 modules.
C. Add stacking modules and cables.
D. Change the power supply type.
An architect needs to plan the RF coverage.
Which application has the greatest potential impact on RF design?
A. print
B. email
C. voice
D. secure web browsing
The customer has an office environment with users who have laptops that can connect with wired or wireless. Users also bring one or two of their own devices. An architect creates a proposal with Aruba AP325s, 7210 Mobility Controllers (MCs), a Mobility Master (MM), and Aruba 2930M switches at the access layer to support the laptops and APs.
The architect plans to recommend 802.1X authentication without tunneled node on Aruba 2930M switch ports that connect to laptops.
What is one advantage of this form of authentication?
A. ensures that Aruba firewall policies apply to wired user traffic.
B. prevents users from connection attempts with more than three devices
C. enables user access control and ensures only authorized users connect.
D. provides a second layer of protection for wireless users at the internal perimeter
A customer has very high availability requirements for wireless services. The architect plans to implement clustering on several Aruba Mobility Controllers (MCs).
Which benefit of this feature should the architect explain?
A. Clustering provides wireless client load balancing and seamless failover for client sessions.
B. Clustering provides high stability because one MC is active for all sessions and one is standby for all sessions.
C. Clustering enables an AP with a failed MC to operate on its own briefly to ensure seamless connectivity.
D. Clustering enables an AP with a failed MC to reconnect to a new AP after a short bootstrap.
An architect needs to plan a wireless deployment. The architect conducts a physical walkthrough, but still needs more information.
Which significant RF obstacle can be difficult to see visually and might require access to blueprints?
A. fiberglass
B. metal firewall
C. ceiling tiles
D. drywall
An architect needs to plan an 802.11ac wireless upgrade for a university building. What is one reason that it is important for the architect to identify auditoriums?
A. Auditoriums typically require a high-density AP design for RF coverage.
B. Users in Auditoriums often have Bluetooth devices, which can be a source of interface in the 5 GHz band.
C. Auditoriums typically require the use of 80 MHz channels to meet bandwidth requirements.
D. Auditoriums often require the use of DFS channels for sufficient 20 MHz channels.
Refer to the exhibit.
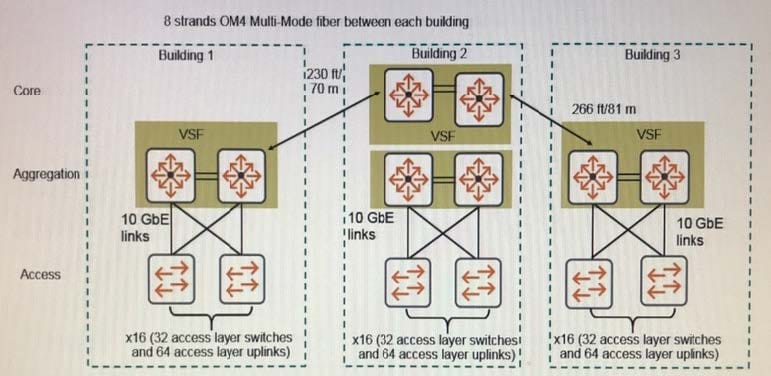
An architect selects 5406R switches for the aggregation layer.
What is an appropriate amount of bandwidth for the link aggregation between each aggregation layer VSF fabric and the campus core?
A. 60 Gbps
B. 160 Gbps
C. 200 Gbps
D. 320 Gbps
A plan includes these security settings for the employee WLAN:
1.
WPA2-Enterprise with AES encryption
2.
802.1X with PEAP-MSCHAPv2
However, the customer wants to use certificates to authenticate user devices.
Which change brings the plan in alignment with the customer requirements?
A. Use EAP-TLS instead of PEAP-MSCHAPv2
B. The TKIP encryption instead of AES.
C. Add WPA2-PSK as an alternative to WPA2-Enterprise.
D. Add Tunneled TLS (TTLS) as an alternative to PEAP-MSCHAPv2.
An architect proposes Aruba 2930F switches, which do not have OOBM ports. The customer wants to follow best practices for network management security.
Which guideline can the architect follow?
A. Assign access layer switches IP addresses on a VLAN that is dedicated for switch management.
B. Ensure that DHCP is enabled on only the switch Default VLAN.
C. Ensure that Telnet is enabled and set to listen on production VLANs.
D. Assign switches static IP addresses on the same VLAN on which APs are deployed.
What is one reason to recommend dedicated Air Monitors (AMs) for a customer, as opposed to APs that are doing WIPS in AP mode (hybrid)?
A. AMs can operate in a hybrid operation mode in which they can support clients, scan for threats, and contain detected threats.
B. AMs can implement wireless containment on any channel on which they detect a threat without negative impact on clients.
C. AMs can detect both 802.11 and non-802.11 sources of interference to the wireless network, while APs cannot.
D. AMs can maintain client and AP blacklists on their own without the need to communicate with a Mobility Controller (MC).