HPE2-W05 Online Practice Questions and Answers
You are troubleshooting ClearPass with IntroSpect, and you notice that in Access Tracker the IntroSpect Logon Logoff actions profile is executing. However, the ClearPass Log Source on the IntroSpect Analyzer is showing dropped entries.
Would this be a good troubleshooting step? (Confirm that the ClearPass context action is sending the User name, MAC Address, Entity Type, and User Role)
A. Yes
B. No
While troubleshooting integration between ClearPass and IntroSpect, you notice that there are no log events for either THROUGHPUT or ERROR in the ClearPass log source on the IntroSpect Analyzer. You are planning your troubleshooting actions.
Is this something you should check? (Check the authentication service being used in ClearPass for the Login - Logout enforcement policy.)
A. Yes
B. No
Refer to the exhibit.
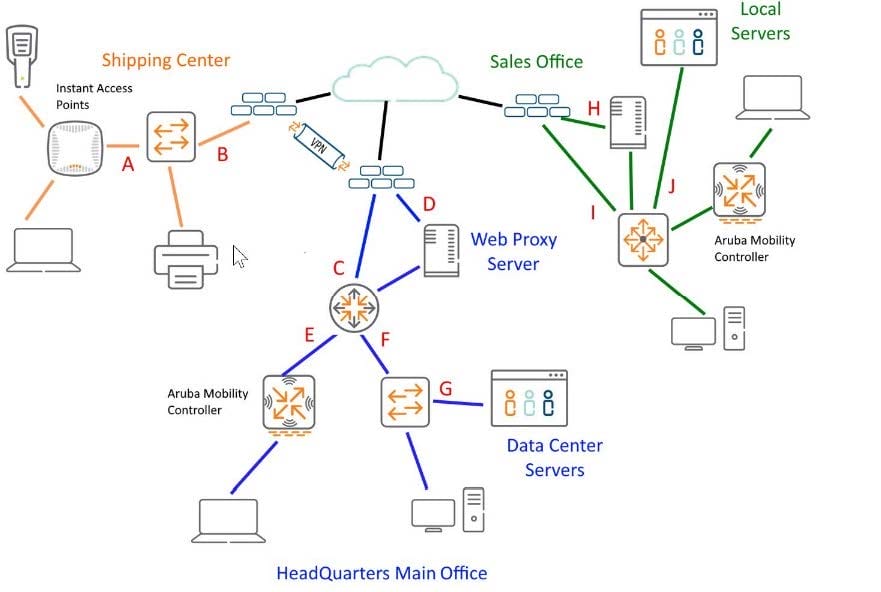
Given the network diagram, would this be a proper location for a network tap? (Port G at the Head Quarters Site would expose all East/West traffic bound for the data center.)
A. Yes
B. No
A company wants to integrate ClearPass with the IntroSpect. Is this a supported version? (ClearPass 6.7.3.)
A. Yes
B. No
Refer to the exhibit.
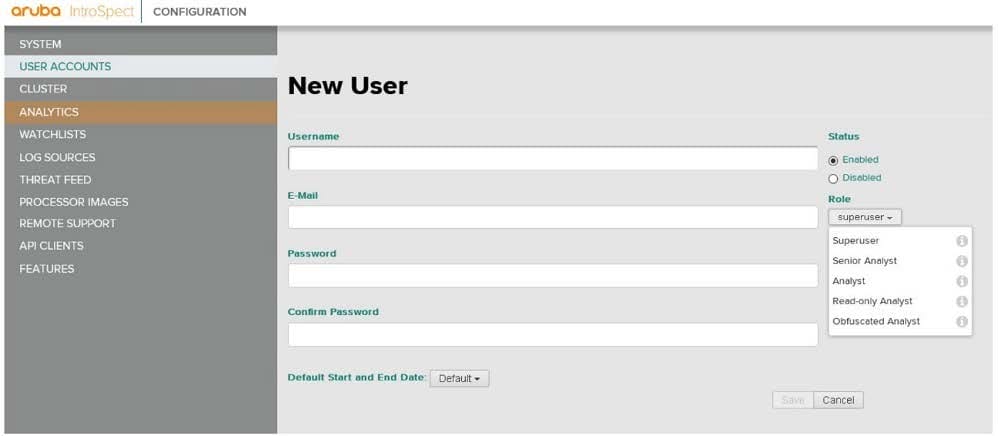
Would this be a correct option when configuring a user account for a ClearPass to use to communicate with IntroSpect? (The username must be the host name of the ClearPass server, and the email address needs to be the username on the ClearPass server.)
A. Yes
B. No
While investigating alerts you notice an entity has triggered a peer alert for visiting recruiting websites. Two days later the same user accessed the office for the first time in the late evening. You also noticed that they downloaded more data than their peers through the VPN session. Based on these conditions, is this a possible cause? (This user has just become a flight risk, and is now sending data off the network to use in their next job.)
A. Yes
B. No
You are visiting a site configured with IntroSpect, and the on-site admin tells you that they do not think that one of their database servers has fired any alerts for large download or strange access patterns. Could this be a reason? (The database server needs to be listed under Configuration>Analytics>User Correlation Config.)
A. Yes
B. No
Refer to the exhibit.
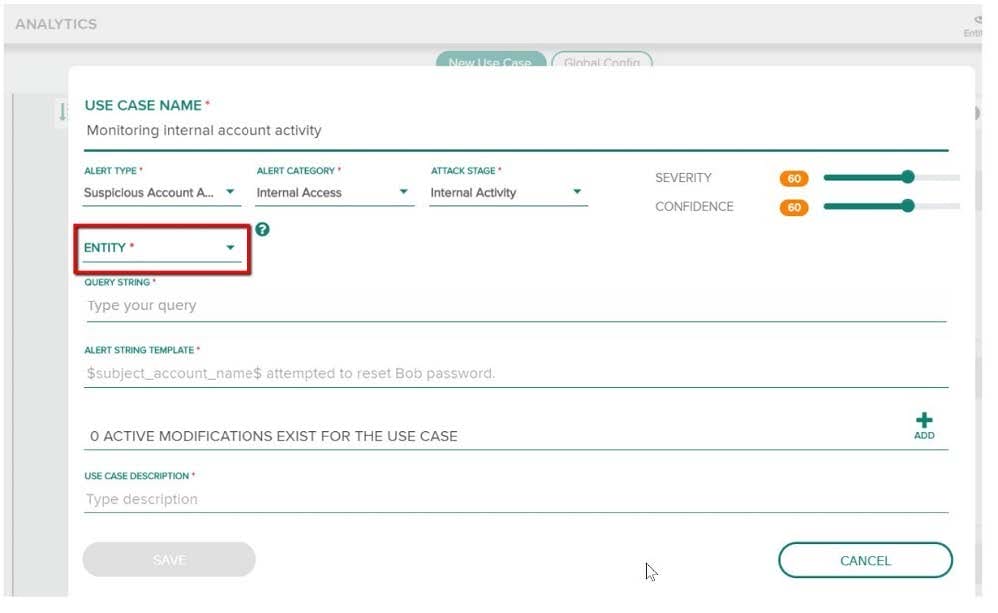
You have been assigned a task to monitor, analyze, and find those entities who are trying to access internal resources without having valid user credentials. You are creating an AD-based use case to look for this activity. Could you use this entity type to accomplish this? (Dest IP.)
A. Yes
B. No
Your company has found some suspicious conversations for some internal users. The security team suspects those users are communicating with entities in other countries. You have been assigned the task of identifying those users who are either uploading or downloading files from servers in other countries. Is this the best way to visualize conversations of suspected users in this scenario? (Visualizing Applications and Ports.)
A. Yes
B. No
The company has a DMZ with an application server where customers can upload and access their product orders. The security admin wants to know how you configure IntroSpect to monitor this server. Should this be part of your plan? (Configure the server in the DMZ as a High Value Asset in Menu>Configuration>Analytics>Correlator Config>so that IntroSpect will monitor the server for access patterns.)
A. Yes
B. No