GSNA Online Practice Questions and Answers
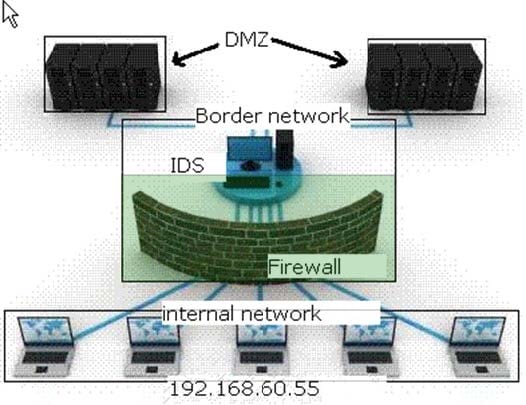
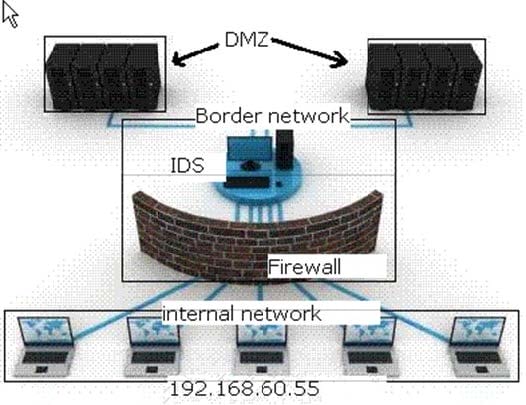
HOTSPOT
The network infrastructure of a company consists of a perimeter network. For security purposes, the network zones have been created and divided into a firewall-based Border network and a DMZ. The enterprise internal network is attacked
by a latest Internet worm.
Which of the following devices in the enterprise network should be upgraded or reconfigured to counter this type of attack?
Hot Area:
John works as a Security Professional. He is assigned a project to test the security of www.we-are- secure.com. John wants to get the information of all network connections and listening ports in the numerical form.
Which of the following commands will he use?
A. netstat -e
B. netstat 璻
C. netstat -s
D. netstat 璦n
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to run a command that forces all the unwritten blocks in the buffer cache to be written to the disk.
Which of the following Unix commands can you use to accomplish the task?
A. swapon
B. tune2fs
C. swapoff
D. sync
eBox Platform is an open source unified network server (or a Unified Network Platform) for SMEs. In which of the following forms can eBox Platform be used?
A. Unified Communications Server
B. Network Infrastructure Manager
C. Gateway
D. Sandbox
Sam works as a Network Administrator for Blue Well Inc. All client computers in the company run the Windows Vista operating. Sam creates a new user account. He wants to create a temporary password for the new user such that the user is forced to change his password when he logs on for the first time.
Which of the following options will he choose to accomplish the task?
A. User cannot change password
B. Delete temporary password at next logon
C. User must change password at next logon
D. Password never expires
Which of the following listeners need not be configured in the deployment descriptor? (Choose two)
A. HttpSessionBindingListener
B. HttpSessionAttributeListener
C. HttpSessionListener
D. HttpSessionActivationListener
Which of the following does an anti-virus program update regularly from its manufacturer's Web site?
A. Hotfixes
B. Permissions
C. Service packs
D. Definition
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to see the username, real name, home directory, encrypted password, and other information about a user.
Which of the following Unix configuration files can you use to accomplish the task?
A. /etc/passwd
B. /etc/printcap
C. /etc/hosts
D. /etc/inittab
Which of the following statements are true about KisMAC?
A. It scans for networks passively on supported cards.
B. It cracks WEP and WPA keys by Rainbow attack or by dictionary attack.
C. It is a wireless network discovery tool for Mac OS X.
D. Data generated by KisMAC can also be saved in pcap format.
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to track the system for user logins. To accomplish the task, you need to analyze the log configuration files.
Which of the following Unix log configuration files can you use to accomplish the task?
A. /var/log/messages
B. /var/log/secure
C. /var/spool/mail
D. /var/log/maillog